In this video tutorial, viewers learn how to mount ISO files without burning DVD. This task is very fast, easy and simple to do. The first way is to simply right-click on the ISO file, go to Open With and select Open with "Archive Mounter". The second way is to open the Termin ...more
New to Ubuntu Linux? This computer operating system could be a bit tricky for beginners, but fret not, help is here. Check out this video tutorial on how to download files from FTP with Terminal on Ubuntu Linux. Download several files in one simple command using Terminal. Tr ...more
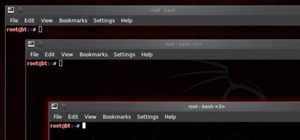
Blip TV user Mr. Root teaches you how to mount an ISO image file using the Unbent Linux terminal. To do this and have access to the files inside of an ISO, without unarchived it, start the terminal. Type in dirk CD. Make sure the ISO image is on your desktop. Then type in sud ...more
Need some help figuring out how to install an app in Linux with the terminal? It's an easy process and this home-computing how-to presents a complete demonstration. For more information, including detailed, step-by-step instructions, take a look.
The Ubuntu experience has improved greatly with version 10.04, providing an easy-to-use interface. Especially when it comes to installing programs. However, it still relies on an online internet connection for installing additional software. Well, not anymore. You can collect ...more
New to Ubuntu Linux? This computer operating system could be a bit tricky for beginners, but fret not, help is here. Check out this video tutorial on how to install and enable Flash for Chromium on Ubuntu Linux. To install the latest Chromium on Ubuntu, open a terminal and: ...more
New to Ubuntu Linux? This computer operating system could be a bit tricky for beginners, but fret not, help is here. Check out this video tutorial on how to install additional TTF fonts on Ubuntu Linux. Here's the command that you can type on your terminal if you want some fa ...more
Here is an alternative method to run Ubuntu 10.04 on a Mac without actually installing it on your internal hard disk. The idea is to install Ubuntu on your USB flash disk, instead of installing it on your internal hard drive. I'm talking about a full disk installation. It won ...more
This tutorial is for Ubuntu 10.04 users who want to tether their iPhone 4 (software version 4.2.1). No jailbreak needed! You have two options - you can tether through USB, or tether through Bluetooth. Tethering through USB Add PPA repository to your synaptic repositories. T ...more
Many windows users, if not all, run into a virus infection once in a while. This is unavoidable when using Microsoft's operating system. Without digressing too much, the fact that Windows is such a popular OS with no controlled software sources makes it easy for viruses and ma ...more
There's plenty of reasons why one would want to convert a webpage to a PDF document. And there's numerous ways on how one can convert that web page (HTML) into a PDF file. Check out this video tutorial on how to convert webpage HTML to PDF on Ubuntu Linux. You could just sele ...more
In this Null Byte, we are going to be installing Packet Injection capable drivers in Linux. These are the open-source drivers required to sniff wireless traffic, inject packets to crack a wireless access point, and go into "monitor-mode". These drivers are superior because the ...more
New to Ubuntu Linux? This computer operating system could be a bit tricky for beginners, but fret not, help is here. Check out this video tutorial on how to install Firefox 3.5/3.6 and make it the default browser on Ubuntu Linux. To install the latest Firefox 3.5 (final) or F ...more
This is my first contribution in an ongoing series on detailing the best free, open source hacking and penetration tools available. My goal is to show you some of the quality tools that IT security experts are using every day in their jobs as network security and pen-testing p ...more
Formerly ipchains, iptables is a script-based firewall that's included with both Mac and Linux operating systems. In my opinion, it's the best firewall in existence. The only downfall is that it's complicated for some people to use due to its script-based nature. But this shou ...more
I have had a lot of people ask me, "How does my neighbor keep getting into my wireless?!". Chances are, these people are all using WEP, a deprecated wireless encryption protocol. Either that, or you are using one weak WPA passphrase. If someone can access your wireless networ ...more
In this tutorial, we learn how to monitor hardware sensors in Ubuntu. First, go to your Synaptic Package Manager and download any IM-Sensors you need. You will also have to download and install "hddtemp". After you do this, go to your terminal and type in "sudo sensors-detect" ...more
If you're having some microphone troubles on your Ubuntu Linux system, this video might help you troubleshoot and solve the broken mic problem. This is about fixing the microphone input specifically. This tweak should fix it. step 1. Launch terminal and type " sudo gedit /etc ...more
This video tutorial in Computers & Programming category will show you how to delete temporary files in Ubuntu, Linux Mint or Debian. For this you will need the program called bleachbit. You could get it from Bleachbit Sourceforge/ or from Synaptic package manager. For synaptic ...more
Ubuntu and Windows may have trouble syncing time because when they are dual booted, they both assume that your hardware clock is set to a different time setting. Ubuntu assumes that your clock is set to UTC and Windows assumes that your clock is set to local time. Answers Laun ...more
This video describes about accessing an iPhone in Ubuntu using open SSH, cyber-duck, Netatalk. For accessing using SSH, make sure your iPhone's Wi-Fi connectivity is on. Now open your terminal and type "SSH root@'address'". Here address refers to the IP address of your iPhone. ...more
This video shows the method to recover deleted files in Ubuntu using Testdisk. The demonstration is done by deleting a set of pictures and recovering them later. The test disk is installed at first. Then we click on the terminal icon and go to the list options available. These ...more
New to Ubuntu Linux? This computer operating system could be a bit tricky for beginners, but fret not, help is here. Check out this video tutorial on how to enable font anti-aliasing on Wine Ubuntu Linux. Type this in the terminal window Step 1. wget http://files.polosatus.r ...more
This video tutorial from izbyfl shows how install Google Chrome and enable its plugins in Ubuntu. First download application from here: http://www.google.com/chrome/intl/en/eula_dev.html?dl=unstable_i386_deb. Make sure you download Gdebi Package Installer. Install applicati ...more
Ever hear of SmillaEnlarger? It's a small graphical tool (based on QT) to resize, especially magnify bitmaps in high quality. Check out this video tutorial on how to back up and restore data easily on Ubuntu Linux. Hundreds of different solutions exist to reduce the resolutio ...more
New to Ubuntu Linux? This computer operating system could be a bit tricky for beginners, but fret not, help is here. Check out this video tutorial on how to enable USB support in VirtualBox on Ubuntu Linux. By default, USB support was disabled in VirtualBox, so you'll probabl ...more
New to Ubuntu Linux? This computer operating system could be a bit tricky for beginners, but fret not, help is here. Check out this video tutorial on how to install Zekr (Qur'an Study Tool) on Ubuntu Linux, Windows, and Mac OS. Zekr is an open platform Quran study tool for si ...more
As many of you Null Byters may know, I was planning on writing this article a week or two ago. Better late than never! So, let's get right to it then—choosing the right Linux distro for your needs. First off, you need a base for your search. Picking a Base Right now, there ...more
In Linux, all password hashes are normally stored using the MD5 hashing algorithm in the /etc/shadow file, but MD5 is algorithmically weak due to collision vulnerabilities. The new recommended standard are the higher level SHA-2 hashing algorithms, SHA256 or SHA512. As a frien ...more
Sharing a laptop's wireless Internet connection with other computers connected to its Ethernet port is a great skill to know. It can be good for a number of reasons; Your computer may not have proper hardware to have a standard setup, or you may have an awkward network topolog ...more
As you progress in the world of information security, you'll find yourself in situations where data protection is paramount. No doubt you will have files to hide and secrets to share, so I'm going to show you how to use the GNU Privacy Guard (GnuPG or GPG for short) to encrypt ...more
When it comes to webcams these days, most people are using their laptops over desktops. The cameras are centered, integrated, and require no configuring. They're a cinch and usually have great resolution. So, then what do we do with all of those old wired desktop webcams that ...more
File Transfer Protocol, or FTP, is a network protocol made for transferring files in a client and host fashion over a Transmission Control Protocol (TCP) network, such as the internet. FTP is integrated into most browsers, and you have probably used it before. It is a common w ...more
Gamers who have their Xbox 360's firmware flashed may have recently noticed an inability to play backups, or even make backups of newer games that have come out, such as Gears of War 3 and Dead Island, to name a few. This is because Microsoft has come out with a new disc form ...more
GRUB, or the GRand Unified Bootloader, is a program that installs to your Master Boot Record and controls what operating system you load at boot time. Normally, it is used for multi-boot systems. Multi-boots allow you to switch between operating systems installed on seperate d ...more
SSL stands for Secure Socket Layer. It's an encryption standard used on most sites' login pages to avoid their users' passwords being packet sniffed in simple plain-text format. This keeps the users safe by having all of that traffic encrypted over an "https" connection. So, w ...more
Hey, hackers! Now that you've hacked/owned your first "box" in my last article, let's look a little closer at another great feature of Metasploit, the Meterpreter, and then let’s move on to hacking a Linux system and using the Meterpreter to control and own it. Why Meterprete ...more
Ubuntu users can directly copy flash videos from the web with Firefox. There's no need to install software such as a YouTube downloader, which are available in abundance throughout the web. First, you need to know where to find the temporary flash file in Ubuntu (see my other ...more
As you already know, Ubuntu doesn't update a major Firefox update to their repository. Here are the steps to do a major Firefox update on Ubuntu. Launch Terminal on Ubuntu and type in the following: Add the Firefox Stable PPA to your system's software sources. sudo add-apt- ...more
With a simple social engineering trick, sudo passwords can be captured in seconds without the target's knowledge. The passwords can then be saved to a file or exfiltrated to another computer on the network. After exploiting a system, penetration tester's and hackers will ofte ...more
SSH, or the secure shell, is a way of controlling a computer remotely from a command-line interface. While the information exchanged in the SSH session is encrypted, it's easy to spy on an SSH session if you have access to the computer that's being logged in to. Using a tool c ...more
When people first learn that their Android device is capable of dual-booting different operating systems, e.g. Linux, they almost universally respond with, "That's so cool." And for those of us ambitious enough to actually try one out, we are typically filled with glee as we s ...more
You've protected your Ubuntu system from physical attacks, annoyed network hackers, and sandboxed potentially malicious applications. Great! Now, the next logical steps to locking down your OS include thoroughly auditing Ubuntu for weak points, using antivirus software that re ...more
While our time with the Protostar VM from Exploit Exercises was lovely, we must move on to bigger things and harder challenges. Exploit Exercises' Fusion VM offers some more challenging binary exploitation levels for us to tackle. The biggest change is that these levels are al ...more
Transferring hundreds of screenshots, webcam recordings, keystroke logs, and audio recordings between your VPS and a local Kali machine can be tricky. Services like Dropbox don't always have the best privacy policies and suffer data breaches just like any other website. To mit ...more
If you've ever wiped your computer without having a proper backup of your operating system, or just wanted to cause some havoc online, chances are you've had to rely on Linux to help you out, specifically the Ubuntu distro. Ubuntu doesn't get a lot of love compared to powerho ...more
No more carrying around heavy laptops and thousands of Linux Live CDs and USBs to always be ready for pentesting on the fly! I hope you had a good Christmas and happy new year! Update1: Added the section "weaponizing your Android" where I talk about apps and fundamental Kali ...more
With the release of the Mirai source code, botnets are back in a big way. In the early days of botnets, zombies (infected hosts) would report to IRC (Internet Relay Chat) channels for CNC (command and control) instructions. Modern botnets have evolved, but they continue to use ...more
Hacker's are always looking for new ways to exploit systems and exfiltrate passwords, even in hashed form. Sophisticated brute-force attacks powered by high-end GPUs can perform millions of password attempts per second. But Ubuntu and Debian users aren't completely helpless. T ...more
In one of my previous articles, I discussed ShinoBot, a remote administration tool that makes itself obvious. The goal is to see if the user could detect a remote administration tool or RAT on their system. In this article, I'll be demonstrating the use of Pupy, an actual RAT, ...more
Tor is an excellent obfuscation network for web traffic, and while instant messaging over the network is very useful, it can be relatively difficult to configure. In this guide, we'll look at two synchronous communications platforms (instant messengers) which can be routed ove ...more
Kali Linux is probably the most well-known hacking distribution among penetration testers. However, there are alternative distros which offer versatility and advanced package management systems that are absolutely worth considering. One such distribution is Pentoo, a Gentoo-b ...more
The internet is constantly under siege by bots searching for vulnerabilities to attack and exploit. While conventional wisdom is to prevent these attacks, there are ways to deliberately lure hackers into a trap in order to spy on them, study their behavior, and capture samples ...more
A man-in-the-middle attack, or MitM attack, is when a hacker gets on a network and forces all nearby devices to connect to their machine directly. This lets them spy on traffic and even modify certain things. Bettercap is one tool that can be used for these types of MitM attac ...more
SSH local forwarding is a must for covering your tracks and getting out there to do your work. Also called SSH tunneling, this process will put one or more steps between your machine and the machine you're working on, for security and other purposes. It can be a bit daunting f ...more
Welcome back, my budding hackers! Metasploit, one of my favorite hacking/pentesting tools, has so many capabilities that even after my many tutorials on it, I have only scratched the surface of it capabilities. For instance, it can be used with Nexpose for vulnerability scann ...more
There's over 20 million people out there who use Ubuntu as their main operating system, and the number is steadily increasing due to its thriving community. While it's easy enough to download Ubuntu on your PC, the process to get it on your mobile devices can be fairly more di ...more
When we think about operating systems, we tend to view them from the perspective of a user. After all, most of us have spent a substantial amount of time on our computers, and so we've become more than acquainted with the ins and outs of whatever system we have running on our ...more
Web application firewalls are one of the strongest defenses a web app has, but they can be vulnerable if the firewall version used is known to an attacker. Understanding which firewall a target is using can be the first step to a hacker discovering how to get past it — and wha ...more
If you find yourself with a roommate hogging limited data bandwidth with video games or discover a neighbor has invited themselves into your Wi-Fi network, you can easily take back control of your internet access. Evil Limiter does this by letting you control the bit rate of a ...more