This is a two-part series to locking down the computer to provide maximum protection. Even though this guide will sound intrusive, we are talking about reality here. Extreme measures must be taken to protect our computers, especially when we have confidential documentation or ...more
Welcome to Minecraft World! Check out our tutorials, post to the community corkboard, and come play on our free server! Minecraft 1.2.5 has been planned for a few days now, but Jeb wanted to wait for modders to catch up to the new changes. This time around, things should run ...more
Whether you're in an airport, restaurant or waiting room, the insidious grip of televisions on human life is omnipresent. Sometimes it's nice to talk to other human beings while looking at them directly—actually hearing what they have to say. Thankfully, there's a DIY device ...more
Are you the expert hacker we're looking for? Do you have a great idea for an article on Null Byte? Do you have a passion to write, and more importantly... teach? We're officially looking for Null Byters on a weekly basis who are willing to take the time to educate the communi ...more
Last week in New York, I saw the new show Otherworldly: Optical Delusions and Small Realities at the Museum of Arts and Design, at Columbus Circle near the edge of Central Park, between Broadway and Eighth. Below is the museum’s description of the show: “Otherworldly: Optical ...more
How to Create Scenery in FSX This article will show you how to create scenery objects in Microsoft Flight Simulator X (unfortunately not available to the Standard FSX, but it is available to standard FSX with the Acceleration Expansion Pack) that you can see in the 'real world ...more
Microsoft SharePoint is a business management system introduced by MICROSOFT. It has many build in functions to work in web based environment easily. Microsoft SharePoint 2010 is released on April 17, 2010. It is introduced with the promise of better performance than its prede ...more
Is game play king? Or was it that graphics is king? or maybe the story? Arghhh... well, regardless from which school of thought you come from, Tera online has bet most of their chips on game play. Tera's game play separates this game from the rest. The ability to deal damage ...more
Today's post is a small go-to guide for beginner programmers in Null Byte. With many of our community members picking up programming from our Community Bytes, it only makes sense to lay out a one-stop guide for your reference. Hopefully this guide will help you make an educate ...more
Minecraft is not just a game. It is a creative tool. Over the past year and a half countless epic builds, servers, and community projects have been undertaken. I'm sure some of you have seen the one-to-one scale recreation of the Starship Enterprise from Star Trek or the epic ...more
I don't know what I'd do without my computer. I can't do my job without the internet. I communicate with employers, friends, and family through emails, video chat and Twitter. I schedule meetings and plan deadlines. I bank. I shop. I read the news. I play games. I watch my fav ...more
INTRODUCTION The everyday PC user doesn't think much about its PC and problems that can cause critical damage to their data or other stuffs stored on Hard drive and other electronic parts until the problem actually occurs. Once a failure happens, the repairs can be costly and ...more
In this Webcast, Password Management for Windows and Beyond, you will learn how to: Increase security standards cross-organization by easily customizing and enforcing password policies for Windows, Unix, Linux, and Java users. Decrease the cost associated with password resets ...more
OpenBSD implements security in its development in a way that no other operating system on the planet does. Learning to use the Unix-like operating system can help a hacker understand secure development, create better servers, and improve their understanding of the BSD operatin ...more
Kali Linux is established as the go-to operating system for penetration testing, but in its default configuration, it's less than ideal for regular desktop use. While in many scenarios, a live boot or virtual environment can resolve these issues, in some situations, a full ins ...more
Augmented and mixed reality experiences attempt to break us out of windowed computing experiences and allow us to place software anywhere in the room. But that software doesn't have to take a rectangular form—theoretically, the web doesn't have to restrict itself to a page in ...more
It's been a while since I wrote up an article for this series but I did say that I'd be covering some WinAPI. So if you're interested in programming for the Windows platform, hop aboard and follow along. Note: This is an extension of the standard C that the previous material ...more
Cross-compilation allows you to develop for one platform (like Kali) and compile to run on a different platform (such as Windows). For developers, it means that they can work on their platform of choice and compile their code for their target platform. For hackers, it means we ...more
Linux and Mac users have long enjoyed the use of multiple virtual desktops to free up clutter on their home screen and keep individual workflow environments separated, but Windows users have always been stuck with one solitary desktop. That's finally changing with Windows 10, ...more
Welcome back, my hacker apprentices! Metasploit framework is an incredible hacking and pentesting tool that every hacker worth their salt should be conversant and capable on. In a previous post, I had provided you a cheat sheet of meterpreter commands. These commands are ess ...more
Welcome back, my budding hackers! As you know, I firmly believe that to be a true professional hacker, you need to be proficient in Linux. This is for a number of good reasons. Most hacker tools are developed in Linux (well over 90 percent). Linux offers us greater granulari ...more
Now that we've officially seen the HoloLens 2 and Microsoft has shown off the improvements and new superpowers of the augmented reality headset, what about the specs? Luckily, Microsoft has laid bare the full specifications for its next-generation headset. Let's dive in and s ...more
Today, anyone with a compatible PC can download the Windows 10 Fall Creators Update and experience Windows Mixed Reality. Also arriving today are Windows Mixed Reality headsets from Acer, Dell, HP, and Lenovo, which are all available through Microsoft Stores. Best Buy also se ...more
Windows Insiders running Build 14971 of Windows 10 in the Fast Ring can now look for the "Windows Holographic First Run" app to check to see if their PCs are up to the task of running Windows Holographic. It won't detect your VR headset yet, but at least you'll be able to see ...more
Most popular virtual reality headsets, like the HTC Vive and Oculus Rift, require a tethered connection to the computer and that imposes some obvious restrictions on how much we can move in our space. We'd all prefer a simpler, untethered option, and Intel wants to provide jus ...more
Hola my fellow hackers! I promised you the tutorials on setting up RAT's and Botnets, but before jumping into those, i want you to know about the precautionary measures and detection of RATs which might be on the system without your prior knowledge. Of course the Anti-virus do ...more
Welcome back, my amateur hackers! Many of you here are new to hacking. If so, I strongly recommend that each of you set up a "laboratory" to practice your hacks. Just like any discipline, you need to practice, practice, and practice some more before you take it out to the rea ...more
Why do you need augmented reality? Because enterprise, they say. And while that's certainly true for several disciplines, there's still that mainstream use case hanging out there waiting for users to discover beyond the realm of enterprise and gaming. After much thought — and ...more
While there are a variety of privacy-focused search engines available like StartPage and DuckDuckGo, nothing can offer the complete trust offered by creating one's own search engine. For complete trust and security, Searx can be used as free metasearch engine which can be host ...more
Koadic allows hackers to monitor and control exploited Windows systems remotely. The tool facilitates remote access to Windows devices via the Windows Script Host, working with practically every version of Windows. Koadic is capable of sitting entirely in memory to evade detec ...more
Hacking from a host machine without any form of proxying is reckless for a hacker, and in a penetration test, could lead to an important IP address becoming quickly blacklisted by the target. By routing all traffic over Tor and reducing the threat of malicious entrance and exi ...more
In 2013, Offensive Security released Kali Linux, a rebuild of BackTrack Linux derived from Debian. Since then, Kali has gone on to become somewhat of a standard for penetration testing. It comes preconfigured with a collection of tools accessible by a menu system, tied togethe ...more
Most of us work with a single monitor, but even with one or two extras, they still offer a rather confined workspace. Virtual reality, however, doesn't have such boundaries. As a result, VR headsets can work as excellent productivity tools. Windows can't just adapt on its own, ...more
Welcome back, my aspiring hackers! Those of you who use Windows in a LAN environment understand that Windows machines can share directories, files, printers, etc. using "shares." This protocol dates back to the 1980s when the then dominant computer firm, IBM, developed a way ...more
Many of my aspiring hackers have written to me asking the same thing. "What skills do I need to be a good hacker?" As the hacker is among the most skilled information technology disciplines, it requires a wide knowledge of IT technologies and techniques. To truly be a great h ...more
Clearing the cache on your computer is (usually) a quick and easy way to help speed it up. Deleting those temporary files frees up space, helping you computer run smoother, especially if you have not cleared the cache for a extended period. However, finding the different cache ...more
Welcome back, my hacker novitiates! As you know by now, the Metasploit Framework is one of my favorite hacking tools. It is capable of embedding code into a remote system and controlling it, scanning systems for recon, and fuzzing systems to find buffer overflows. Plus, all o ...more
Sitting in a cubicle and never seeing sunlight during the workday is unpleasant to even think about—and sitting in a flourescent-light cube can have terrible effects on both our work performance and overall attitude. Yet there are ways to counteract the effects of cubicle sitt ...more
Welcome back, my budding hackers! One of the keys to being successful as a hacker, pentester, or cyber warrior is the ability to find vulnerabilities or flaws in the target system, which are what we exploit when we hack. We have looked at several ways to do that including var ...more
Welcome back, my aspiring hackers! One of the areas that often gives Linux newcomers problems are the environment variables. Although Windows systems have environment variables, most users, and for that matter, most administrators, never manage their environment variables. To ...more
Kali Linux has come a long way since its BackTrack days, and it's still widely considered the ultimate Linux distribution for penetration testing. The system has undergone quite the transformation since its old days and includes an updated look, improved performance, and some ...more
Now that the dust has finally settled on Microsoft's big HoloLens 2 announcement, the company is circling back to offer more granular detail on some aspects of the device we still don't know about. Aside from making some team members accessible for interviews, the company has ...more
Most of today's mobile augmented reality apps focus on individual experiences, but a new entrant into the space wants to make things a bit more social. Battle tested for years in the realm of virtual reality, vTime is finally bringing its immersive social chat experience into ...more
The addition of a new research mode for Microsoft HoloLens will enable researchers and developers to tap into a wider range of data collected by the device's sensors. Available in the Windows 10 RS4 update for HoloLens, application code in Research Mode can access computer vi ...more
When it comes to hacking guides, most are written from the perspective of a Linux user. There are a few outliers, but it's mainly Linux, which leads to the idea that Linux is the only OS that's viable for hacking. This couldn't be further from the truth. A properly set up Appl ...more
Greetings my fellow aspiring hackers, Android Development like other programming languages requires the use of some basic essential components, programs and configurations to get started. Android Development requires a little bit of knowledge of the Java language which means ...more
If you have ever wanted to mod your Android device, your new best friend is easily going to be Team Win's TWRP custom recovery. This gives you access to file flashing on the fly, which can include such things as Magisk for root access, or even a custom ROM to replace the stock ...more
Kali Linux is the go-to Linux distribution for penetration testing and ethical hacking. Still, it's not recommended for day-to-day use, such as responding to emails, playing games, or checking Facebook. That's why it's better to run your Kali Linux system from a bootable USB d ...more
The Pixel 3a runs smoothly out of the box already, but installing a custom kernel can supercharge your experience even more. From fine-tuned CPU tweaks for boosting performance or battery life to adjusting the display colors for your screen how you want, ElementalX kernel can ...more
Over the last few years, the only thing teased by Magic Leap more than the Magic Leap One itself has been the company's flagship gaming title Dr. Grordbort's Invaders. The game, developed by New Zealand studio Weta Workshop, finally got its debut last week during the L.E.A.P. ...more
Since getting our hands on the Magic Leap One last week, we've been methodically delving into each feature and reporting our findings step-by-step. Earlier this week, we took a look at the Screens app (a video viewer) and the Helio app (an AR web browser). This time around, we ...more
After exploiting a vulnerable target, scooping up a victim's credentials is a high priority for hackers, since most people reuse passwords. Those credentials can get hackers deeper into a network or other accounts, but digging through the system by hand to find them is difficu ...more
In many urban areas, GPS doesn't work well. Buildings reflect GPS signals on themselves to create a confusing mess for phones to sort out. As a result, most modern devices determine their location using a blend of techniques, including nearby Wi-Fi networks. By using SkyLift t ...more
When new Android versions come out, the modding community has to find new ways to root the OS. It's a fun cat and mouse game to follow, but it also means the process of rooting isn't exactly the same as it was the last time you did it. Android 10 changes how root works on a sy ...more
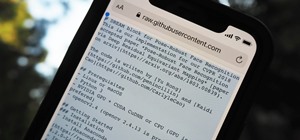
Microsoft.com is one of the most extensive domains on the internet with thousands of registered subdomains. Windows 10 will ping these subdomains hundreds of times an hour, making it challenging to firewall and monitor all of the requests made by the operating system. An attac ...more
Nearly a year to the day after the unveiling Magic Leap One, Magic Leap has dropped another update to the Lumin OS that runs the device. Lumin OS version 0.94 is available now as an over-the-air update or via download on the Creator Portal for Magic Leap One users. The bulk ...more
With the addition of the OpenSSH client and server in the Windows 10 Fall Creators Update, you no longer have to rely on third-party programs to open an SSH server and connect to a Windows machine. While still a beta feature, this represents a long-overdue update fulfilling a ...more
Augmented reality is beginning to leak out into the mainstream world. This is thanks, in part, to ARKit and ARCore. These releases turned the current smartphones owned by millions of Apple and Android users into AR-capable machines. And while there are definitely some awesome ...more
With Virtual Network Computing, you don't need to carry a spare keyboard, mouse, or monitor to use your headless computer's full graphical user interface (GUI). Instead, you can connect remotely to it through any available computer or smartphone. Virtual Network Computing, be ...more
While the USB Rubber Ducky is well known by hackers as a tool for quick in-person keystroke injection attacks, one of the original uses for it was automation. In this guide, I'll be going the latter, explaining how we can use it to automate Wi-Fi handshake harvesting on the Ra ...more