This step-by-step tutorial will show you how to install Mac OS on Windows 7 on Virtual Box. Video: . All important links are below: Learn about BIOS Check if your PC has Virtualization Technology (HAV Tool) Enable & find Virtualization option in BIOS More info about virtual m ...more
Whether you're at work or in class, there are times when using your phone is unacceptable, regardless of that subtle yet sudden twitch in your arm that arises every time you hear the vibration of a text message. To combat being seen, addicted text messagers have devised ways ...more
I love my Mac to pieces, but there have been times, so many times, that I wanted to silence that classic Apple start-up chime. I mean, the only thing the sound does is notify everyone around you that you have a Mac, and that you have turned said Mac on, right? Well it's not so ...more
When I left off on our last hack, we had hacked into the ubiquitous Windows Server 2003 server by adding ourselves as a user to that system so that we can return undetected at any time. The problem with this approach is that a sysadmin who is on their toes will note that a new ...more
Over the past decade, Marvel Studios has been a dominant force at the box office, raking in more than $21 billion dollars. Averaged out over that span of time, the yearly earnings of those movies outweigh the gross domestic product of some countries. And while those films hav ...more
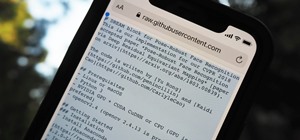
Apple's iOS 15.4 update for iPhone is out after 46 days of beta testing, and it has some exciting features you won't want to miss. Here's everything you need to know about the new software. The iOS 15.4 software has been available to developers since Jan. 27, 2022, and public ...more
Post-exploitation information gathering can be a long and drawn-out process, but it is an essential step when trying to pivot or establish advanced persistence. Every hacker should know how to enumerate a target manually, but sometimes it is worth it to automate the process. M ...more
A majority of iPhone users, including our whole staff here, have an irritating issue with media playback from car stereos: The first song alphabetically in the iPhone's library will play automatically when connecting to the head unit either via USB cable or Bluetooth. CarPlay ...more
If you want to follow Null Byte tutorials and try out Kali Linux, the Raspberry Pi is a perfect way to start. In 2018, the Raspberry Pi 3 Model B+ was released featuring a better CPU, Wi-Fi, Bluetooth, and Ethernet built in. Our recommended Kali Pi kit for beginners learning e ...more
Root, TWRP, Xposed, Magisk, custom ROMs — before you can have any of these, the first thing you should do is unlock your bootloader. Thankfully, the Pixel 2 and Pixel 2 XL are some of the most modder-friendly phones out there, so you only need to send a single fastboot command ...more
Apple gave the Messages app a massive makeover with iOS 10, with a slew of options that made iMessages on the iPhone a lot more fun. While not quite as comprehensive, iOS 11 builds upon that success and makes the app more user-friendly and all-inclusive. iOS 11 brings plenty ...more
If you have a local Trader Joe's, you know first-hand how enchanting the frozen aisles are—almost every item offers the promise of a delicious meal or dessert. (We're always tempted to open the package and eat the cookie butter cheesecake, stat.) While cooking from scratch is ...more
We here at Food Hacks are all about saving you, our wonderful readers, time and trouble in the kitchen. So when I saw that Barilla had come out with their Pronto line of "One Pan, No Boil, No Drain" pasta, I had to give it a try. While no-boil lasagna noodles have been around ...more
Welcome back, my greenhorn hackers! As expected with Null Byte's dramatic growth over the last year, we have added many new aspiring hackers who are still lacking in the basics of networking. In addition, with the new "White Hat" certifications coming out shortly, the exam wi ...more
Welcome back, my fledgling hackers! Let's continue to expand our knowledge of digital forensics, to provide you the skills necessary to be a digital forensic analyst or investigator, as well make you a better hacker overall. In your attempts to enter a system or network undet ...more
As a regular Mac OS X user, I have a love/hate relationship with the "Open With" contextual menu. Sometimes, it has just what I need. Other times, it's often packed with unnecessary or duplicate items, or missing the app I want to open the file up with the most. Unfortunately ...more
Welcome back, my hacker novitiates! Many of you have probably heard of a man-in-the-middle attack and wondered how difficult an attack like that would be. For those of you who've never heard of one, it's simply where we, the hacker, place ourselves between the victim and the ...more
In my last quick clip, I demonstrated how to take a bottle of soda and freeze it on command. I received many requests for a more detailed article on this, so here we go. This "super cool" trick works with cans of soda too, not just bottles! Video: . This project was inspired b ...more
An internet connection has become a basic necessity in our modern lives. Wireless hotspots (commonly known as Wi-Fi) can be found everywhere! If you have a PC with a wireless network card, then you must have seen many networks around you. Sadly, most of these networks are sec ...more
You may or may not have heard of alt-rock band Panic! at the Disco, but a year and a half ago they released a single called "The Ballad of Mona Lisa", which had an accompanying music video that was Steampunk-themed. In fact, here's the video: Video: . Well, I'm going to give y ...more
It can feel pretty chaotic when you have a lot of open windows on your Mac that are different sizes, but there's an easy way to organize the mess in just a few seconds. I regularly have a lot of windows open across my MacBook and external displays. Right now, I have 11 apps o ...more
The iPhone doesn't stop at last year's excellent iPhone 12 lineup. Apple's been developing its iPhone 13 models for a while now, and there are a lot of rumors already with eight or nine months still to go until a release. This year, we're expecting four new models with similar ...more
The top five apps of the 2010s were all social media apps of some kind, and the fact that's not surprising to you says a lot. We may use them for other reasons here and there, but our phones are social media machines at their cores. The thing is, some make better machines than ...more
Android 10's new dark mode is a pleasure to behold for longtime users. Ever since OLED panels became widespread, we've been clamoring for the feature. But now that we have it, there's a new problem: it doesn't turn on automatically based on time of day. Thankfully, a simple ap ...more
A development duo has concocted an iPhone app that displays related tweets based on objects recognized by the device's camera. Or Fleisher and Anastasis Germanidis compiled the experiment, dubbed Twit.AR, using Apple's CoreML machine learning platform and Google's Inception v ...more
Ride-sharing firm Lyft says it will continue to rely on drivers in the near and long term even as it replaces them with driverless cars, Taggart Matthiesen, Lyft's director of product, said during a Podcast with Recode. In other words, Matthiesen says Lyft plans to offer oppo ...more
Do you remember my last article on how to hook any web browser with MITMf and BeEF? Well, we are using the tool once again, but this time for auto-backdooring.... How It Works MITMf (if you don't already know) is a man in the middle attack framwork. MITMf literally stands fo ...more
Cooking rice, pasta, and other grains in water is so boring. There is a much better way to guarantee they will have your mouth chewing something seriously tasty: cook them in something that isn't water. Alternative liquids such as stock, milk, juice, or even tea will give blan ...more
Want to get even this Halloween? Want to scare somebody with nothing but a few lines of code? Here's how it can be done... So, with arguably the best holiday quickly approaching us, I thought I'd do a fun post on a cool way to prank your friends, enemies, or maybe even the wh ...more
The desktop layout in Mac OS X Yosemite is undeniably beautiful—it's sleek, simple, and easy to admire. Thing is, I do too much on my Mac to install a developer preview as my main OS (even though I can make a bootable install drive and dual-boot it), but I do want the aestheti ...more
Let me start out by saying that Steampunk isn't about being historically accurate, and that everything I'm about to tell you is entirely optional. That said, let's take a look at the history of screws! What many people don't realize is that before we had metal screws, wooden s ...more
While many of the features in the iPhone 16 and 16 Pro series build on what we've seen in previous iPhone models, Apple has packed the 2024 lineup with iOS 18 and plenty of fresh upgrades worth considering. The iPhone 16 Pro and 16 Pro Max boast several groundbreaking feature ...more
You may know the traditional way to take a screenshot on your iPhone, but it may not be the best action for your needs. There are faster ways to capture an image of your iPhone's screen, methods for capturing overlays and other elements that won't show in regular screenshots, ...more
Have you ever heard a sound when you shut down, boot up, or restart your iPhone? Probably not, but it doesn't have to stay that way. Many computers and Android devices support power-related sounds and have for some time now, but it's something Apple always omitted from iOS — ...more
If you live in the US, it's pretty simple: The Google Pixel 4a is the best phone for rooting and modding in 2020. Its price keeps the risk-reward ratio nice and low, and its unlockable bootloader makes it easy to modify virtually any aspect of Android. But recent updates to A ...more
After jumping to the head of the class of augmented reality journalism in 2019, USA Today is continuing to push the medium forward in 2020. The latest AR story from the media company explores one of the biggest stories of 2019 in the Boeing 737 Max aircraft, which the Federal ...more
When you think about your Apple Watch, what comes to mind? Fitness tracking? Replying to texts? There are a lot of things Apple Watch is good for, but social media doesn't appear to be one of them based on the App Store. If that's your perception, however, it's time for a real ...more
Apple has seemingly always made it a priority to show how much it cares about user security and privacy — enough that it has a page dedicated to it, proclaiming that "privacy is a fundamental human right." It's true that there are few issues more important than user privacy wh ...more
With a tiny computer, hackers can see every website you visit, exploit services on the network, and break into your Wi-Fi router's gateway to manipulate sensitive settings. These attacks can be performed from anywhere once the attacker's computer has been connected to the rout ...more
The Pixel 3a came out of nowhere and flexed its muscles to show the industry that you can have a great phone without a hefty price tag. Since Pixel smartphones are first-party devices straight from Google, you can be sure you'll have root access one way or another. For right n ...more
Apple released iOS 12.3, the latest version iOS 12 for iPhone, on May 13. Great features to know about include Apple TV Channels such as HBO and Showtime that you can subscribe to in the TV app, support for audio, image, and video streaming to AirPlay 2-enabled TVs, and the ab ...more
Many of our online accounts now come with an added two-factor authentication (2FA) functionality to help keep our data safe. This essentially means no one would be able to access the account until a specific set of requirements were met. It could be a combination of a password ...more
After the spectacular rise and fall (and rebirth) of Glass, Google is taking another run at augmented reality smartglasses. Citing documents from companies involved in the project, WinFuture reports that Quanta will serve as the contract manufacturer for the wireless headset, ...more
After a hacker has configured Metasploit on a remote private server, created a resource script for automation, and created a simple payload, he or she can begin the process of remotely controlling someone's Windows 10 computer with just a few moments of physical access — even ...more
With Virtual Network Computing, you don't need to carry a spare keyboard, mouse, or monitor to use your headless computer's full graphical user interface (GUI). Instead, you can connect remotely to it through any available computer or smartphone. Virtual Network Computing, be ...more
The threat of an evil access point has been around for a long time, and with the rise of open public Wi-Fi, that threat is often overshadowed by how comfortable we are using third-party Wi-Fi hotspots at coffee shops and public spaces. While we've shown an evil twin attack usi ...more
Apple released the second version of its iOS 11.2 developer beta Monday, exactly one week from beta 1, then opened up the public beta version on Tuesday. While beta 2 has been available on iPhone X since Friday, Nov. 3, all compatible iPhones can now update to this version. T ...more
If you need to scan a large number of domains for a specific web app vulnerability, Dorkbot may be the tool for you. Dorkbot uses search engines to locate dorks and then scan potentially vulnerable apps with a scanner module. This tool is useful if you're managing a large num ...more
As augmented reality becomes more and more integrated into the mainstream, people have been wondering the future of AR is going to look like. Jay Samit has a pretty clear idea. Samit is an expert in digital media innovation. He has been called a leader in digital "disruption" ...more
While the USB Rubber Ducky is well known by hackers as a tool for quick in-person keystroke injection attacks, one of the original uses for it was automation. In this guide, I'll be going the latter, explaining how we can use it to automate Wi-Fi handshake harvesting on the Ra ...more
In December of last year, Australian Feliks Zemdegs broke the human world record for solving a Rubik's Cube with a time of 4.737 seconds. Well, this robot did it way, way faster by solving one in under 1 second. Don't tell me a robot takeover isn't real possibility. Video: . D ...more
Apple's plans for virtual, mixed, and augmented reality have remained a mystery for some time, but now we at least have some idea of what they're thinking about. UploadVR uncovered a patent showing a VR headset design that looks like a thick pair of sunglasses and utilizes an ...more
When you hand your unlocked iPhone to somebody so they can use the internet real quick, check out some cool photos, or do whatever, there's a possibility that they could snoop around where they don't belong. If you have some secret recipes, login credentials, intellectual prop ...more
The title might not be in harmony with the post, but thinking a good title that perfectly matches your post... isn't that easy. Especially for this post. And it's not like I'm sharing any personal experience, mine is a WinXP machine that wouldn't even pick 7. I'm rather telli ...more
Hello y'all! I apologize if this question has been solved somewhere else, but I have looked around on Google, Yahoo, and Null Byte and have not been able to find any working solutions. I've been trying to set up my first ever virtualbox guest (Kali Linux 2.0), but I'm having ...more
There are many ways to take a screenshot in macOS (previously Mac OS X), but all of the well-known options give you a drop shadow in the picture when snapping application windows. If you use the Command Shift 3 shortcut, it takes a screenshot of the entire screen. If you use ...more
Welcome back, my novice hackers! Reconnaissance is one of the most important preparatory steps to hacking. As I have emphasized many times before here on Null Byte, you must know the operating system, the ports, the services, the applications, and sometimes even the language ...more
If you've ever owned an HTC device or anything in the Nexus line, odds are, you have typed the word "fastboot" into your command line at one time or another. That said, odds are, you have only just barely scratched the surface of what this handy little Android tool can do. Let ...more
The microwave oven is a monumental technological achievement that's saved college students and single people from starvation for decades. Almost 97% of all American households have one, which makes it the most-owned kitchen appliance in US homes right after the refrigerator. ...more
I can't tell you how many times I've force-closed or restarted Chrome due to it freezing or loading pages incorrectly. And don't even get me started on that obnoxious "Aw, Snap!" error. I guess you could say I have a love-hate relationship with my most used browser. But, it t ...more