Norovirus outbreaks occur all year long, but peak in the winter months, which means we are in the middle of norovirus season. But there's still time to protect yourself from the highly infectious bug. There's no vaccine for the virus that causes one to three days of misery—ab ...more
Let's say you gave your Wi-Fi password to your neighbor a while back, under the assumption that they'd only use it while they were at your house sharing stuff via Chromecast. But now, your connection is slower than it normally should be, and you have this sneaking suspicion th ...more
3D modeling is usually a very long and complicated process. Manipulating the thousands to millions of vertices, faces, and triangles to the correct shape you want is just the first part of the process, and can take a good while depending on the level of detail needed. From th ...more
LG, like many other OEMs, usually locks down their bootloaders with an airtight seal. There are a few good reasons for this, the big one being that an unlocked bootloader technically compromises some device security measures. LG would also argue that unlocking your bootloader ...more
The fact that this guide even exists is a downright shame, but that's neither here nor there. The truth of the matter is the iPhone 7 and 7 Plus don't have 3.5 mm headphone jacks, and since they use the Lightning connector to output audio, it's hard to charge your phone while ...more
The new iOS 10 won't be released to the public until September 13 via an OTA update, but the Gold Master edition is available right now. Essentially, it's the same version that Apple will release on the 13th, but only for developers so they can get their apps up to snuff befor ...more
When Google issues an Android update, the changes are usually all over the place—fixing issues, adding functionality, playing catch-up with the latest thing Apple added to iOS. It's how the smartphone wars have evolved, where the two competing operating systems continually mat ...more
We're wild for whipped cream in our coffee, atop our brownies, and in-between wafer cookies, so we always have some in our fridge. To be specific, we always have homemade whipped cream in our fridge, because the taste is just so much better than the pre-made stuff. Don't Miss ...more
Most people I've talked to agree that Shake Shack has mastered the upscale, fast food hamburger quite well. So when a new burger comes out on the ultra-popular fast food chain's menu, you've got to take notice—even if you live nowhere near one. Their latest creation, the Baco ...more
Greetings fellow students! I'm currently reading a book called "Violent Python: A Cookbook for Hackers, Forensic Analysts, Penetration Testers and Security Engineers" This book will teach you different kinds of Python programs for hacking, forensics or penetration purposes ! ...more
Alright so last time I gave you a homework assignment. This week we're gonna look at my version of the UDP-Flooder. It can be found here. Alright, I assume you've written yours or at least attempted to. First let's take a look at the struct used in this program struct sock ...more
Hello again, folks! I'm back with another (final) guide on runtime crypters which is an extension on my previous runtime crypter guide. If you have not read it yet, I highly recommend that you do since the fundamental theory of the PE format. Again, this will be a Windows-spec ...more
Good day people, today we will examine some basic, for some people well-known attacks, also we will take a look at some advanced attacks. At the beginning I must stress that this article is not technical - in other words if you wanna hands-on exercise, this is not article for ...more
What's good, peeps? I've been noticing some rather advanced tutorials slowly emerging here on Null Byte and I know that people want more of them but I've been reluctant to post something of such caliber because I fear that the information will just go over their heads, but hey ...more
What began as a regional specialty has turned into a national trend that looks like it's here to stay: Nasvhille hot chicken has caught on like wildfire, with hot chicken restaurants popping up across the country—not to mention the 8 hot chicken restaurants that you can find i ...more
Turns out, you no longer need third-party flight tracking apps to get information on yours or others' flights—your iPhone and Mac can now give you flight details right from your Mail, Notes, and Messages apps. Apple's flight data detectors were baked into iOS 9 and OS X El Ca ...more
Welcome back to a tutorial on malware. We'll be discovering a method to beef up our little trooper. Without further ado, let's jump right in! Recap In the previous tutorial, we learned how to write a program which opened itself for reading to write to a host file, overwritin ...more
Managing hard drives in Linux is crucial to understanding your system and its operation as well as understanding the system you are exploiting or conducting a forensic analysis on. Linux has numerous commands that can provide us with information, control, and management of har ...more
In the last tutorial, we learned how to make functions and how they work on the high level. This time, we will take a peek under the hood again, stare deep into its soul and see its ugliness face to face to see how it works in the lower level. The Code Segment The code segme ...more
When you're in a bind and need an internet connection for your laptop, look no further than your iPhone. Using the Personal Hotspot feature in iOS, you can share your iPhone's internet connection with other devices by way of Wi-Fi, Bluetooth, or even USB. Don't Miss: Increase ...more
Microsoft's Windows 10 has proven to be a solid release by Microsoft, with faster adoption rates than its predecessor builds. The seamless integration of cloud services and tweaks both major and minor make using Windows easier than ever now. And it's almost enough to forget yo ...more
Hello All, So to recap in part 1 I went through setting up the dchp server. Part 2 detailed the bash script. Now in part 3 I will post the entire bash script. I am doing this in its own post because Part 2 is just way to much info on one post IMO. Here is the script. Please ...more
When attempting to compromise a target, we want as much control as possible over the victim. Metasploit's meterpreter allows us to have immense control over the victim, the only issue is that sometimes we can't land a meterpreter. We may only be able to land a standard shell, ...more
Greetings dear null byters, today we start a new series, we will start to attack users using social networking that are popular such as Facebook, Skype, and much more, and in part 1 of the series will engage users of Skype. What we are going to do today? 1 - get the IP from h ...more
Roughly four years ago, Adobe decided to abandon development of the mobile version of their popular Flash Player browser plugin. Their excuse at the time was that this move would enable them to focus more on HTML5 development for mobile devices and allow them to put more effor ...more
Star Trek Communicator badges rule. If you're a Trekkie, you know they are iconic to the TV series. The Next Generation, Voyager, and Deep Space Nine all had these awesome communicator badges. Video: . Step 1: Draw Your Communicator Badges I designed mine in a product called ...more
Have you ever been using your computer when a friend randomly decides it's time to start up a text message conversation? You usually have to stop what you're doing on the desktop, then go pick up your smartphone and respond to the text. Then, if your buddy replies with another ...more
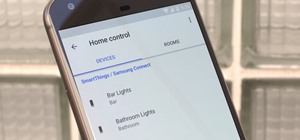
Being an Google fanboy means that I pretty much use anything with the company puts out, so it's no surprise that out of all the cloud services out there, I stick with Google Drive. But, this is way more than just some blind allegiance. Seeing that Google Drive is integrated s ...more
Arcade games have always been more about chance than skill (at least when I play them). Whether you're at a children's party at a Chuck E. Cheese's or drinking it up with your pals at a barcade like Dave & Buster's, you'll find similar games that hold the golden ticket to fun ...more
Man-in-the-Middle attacks can prove to be very useful, they allow us to do many things, such as monitoring, injection, and recon. What Is a Man-in-the-Middle Attack? Essentially, a man-in-the-middle attack is when an attacker places them self between two parties. This passes ...more
Microsoft has invested years and countless man-hours in an effort to get their cloud storage service on par with competitors like Dropbox and Google Drive, who have long resided at the top of this market. Their hard work has definitely paid off, as OneDrive (formerly SkyDrive) ...more
In the past, updating a rooted Samsung Galaxy device has always involved the complicated process of downloading the proper firmware for your variant, installing device drivers, then sideloading the update with Odin. Luckily, though, with the release of the Galaxy S6, Samsung ...more
When setting up a new Mac, there can be a bunch of settings that need to be changed in order to get the system running the way you like it. That usually involves going through tons of System Preferences panes and app settings—but it doesn't have to. If you'd rather get everyt ...more
Like most food lovers, I adore sushi. And like anyone who is a living, breathing human being, I'm a pretty big fan of sriracha sauce. I guess you can see where this is going. Yes, sriracha sushi, which I've decided is my new favorite thing. I discovered how to make sriracha s ...more
Although iOS 8.4 was just released, the team behind the iOS 8.3 jailbreak have updated their tool for the latest operating system, and will work on an iPad, iPhone, or iPod touch. So if you've been wanting to get all your tweaks back, or want to start exploring all of Cydia's ...more
If you have a ton of photos and videos on your iPhone, backing up to iCloud is probably a no-go since it only provides 5 GB of free storage. Yes, you can buy more storage, but who wants to do that? And what happens if you run out of storage, stop backing up, and your phone get ...more
Apple's latest update to Mac OS X, 10.11 El Capitan, is currently available in the Mac App Store for everyone to download and install at no cost. The new OS features Split View mode for better multitasking, a cleaner Mission Control, smarter Spotlight, a way to mute Safari tab ...more
Imagine this scenario: You exploited a system using metasploit and you want to install a backdoor. You have a few options; Use the meterpreter persistence command. Use the meterpreter metsvc command. Use netcat to listen on a port continuously. You have already tried option ...more
Relentless in its fury, the iOS text messaging exploit that exploded onto the scene late last week seems to do more damage than initially reported. Used to reboot devices and crash the Messages app, the string of text can also be used to crash third-party apps such as Instagr ...more
I grew up in a rural town, and that meant that we dehydrated a lot of food. Even with a hungry family of five, there was no way that we could eat all of the season's tomatoes before they molded, or all of the orchard's apples before they grew soft, or all of the wild mushrooms ...more
Many Android utilities use Android Debug Bridge, or ADB for short, to send commands from a computer over to your phone or tablet. This enables such utilities to run terminal commands that, in some cases, wouldn't be possible on Android without root access. Before getting star ...more
Android Debug Bridge (or ADB for short) serves as a remote terminal interface for executing shell commands on any Android device. Put simply, ADB lets you send commands from your computer to your phone or tablet, some of which would require root access if they were performed o ...more
After several weeks of testing out the public beta, Apple has finally released iOS 8.3 to the general public. The latest iteration of iOS for iPad, iPhone, and iPod touch serves mostly as an update to fix many of the bugs that plagued earlier versions, but there are still a co ...more
Android Lollipop still doesn't have a simple way to add a custom lock screen wallpaper, so when I came across Corgi For Feedly from developer Stan Dmitriev, I had to check it out. What sets Corgi apart from other lock screen replacements is that it connects directly to your Fe ...more
As technology continues to advance, we as consumers are privileged enough to be able to take higher quality photos and videos and listen to clearer and better-sounding music on our mobile devices. But sometimes we forget that there's a price to pay for that awesome content—eno ...more
Although this century is still young, with little fanfare we may have just witnessed the "Hack of the Century." AV software developer Kaspersky of Russia recently announced that they found that some hackers have stolen over $1 billion from banks around the world! Advanced Per ...more
Welcome back, my aspiring hackers! As I mentioned in earlier posts, the best hackers (or at least those not behind bars) have a keen understanding of digital forensics. If I am tasked to intrude upon an enemy's file server to retrieve war plans, such as in this tutorial, it i ...more
Welcome back, my novice hackers! As we saw in my first tutorial on Facebook hacking, it is not a simple task. However, with the right skills and tools, as well as persistence and ingenuity, nothing is beyond our capabilities. One of the cardinal rules of hacking is: "If I ca ...more
With the sheer amount of photos, videos, and miscellaneous files we place on our computers, proper organization becomes necessary. Not only so that we can quickly get to a file when it's needed, but also to declutter folders and keep them from looking like random file dumps. ...more
With Apple's Yosemite build of Mac OS X came Continuity, a feature that has allowed us to connect our mobile devices to our computers, letting us access apps, send text messages, answer phone calls, and more while seamlessly switching from one device to the other. Pushbullet, ...more
While you can do a lot of things on your smartphone that were once only done on a computer, having a laptop is still necessary and critical for many tasks. Often times, the two devices work very well together. We recently covered Google's Chrome Remote Desktop, an app that al ...more
Welcome back, my fledgling hackers! With this first article, I am initiating a new series intended to convey to my readers the skills necessary to develop your own exploits. As many of you know, soon after an exploit is found in the wild, software developers begin to work on ...more
Welcome back, my nascent hackers! Like anything in life, there are multiple ways of getting a hack done. In fact, good hackers usually have many tricks up their sleeve to hack into a system. If they didn't, they would not usually be successful. No hack works on every system a ...more
Using a combination of my phone, laptop, and an arsenal of apps and plugins, I can send pretty much anything to my Chromecast. However, nothing is ever perfect, and the file type that was still giving me headaches were torrent and magnet files. Yes, I could download them to m ...more
Coffee shops are a relaxing place to get work done on your laptop; there's free Wi-Fi, fresh coffee, and people generally leave you alone. Inevitably, those cups of coffee will go straight through you, resulting in a much-needed bathroom break. But while you're attending to yo ...more
One of the biggest improvements in Mac OS X Yosemite came to the Spotlight search feature, allowing users to not only search through their applications, but also their emails, text messages, iCloud, and the web. But with this great power, it seems that Spotlight collects your ...more
I may not be a parent just yet, but I've dealt with enough worrisome mothers to know that keeping a watchful eye over your child is of the top-most importance. Since most people cannot afford to stay right by their child's side 24/7, developers are always looking for ways to m ...more
Eating healthy poses a challenge nowadays with so many options that taste great but aren't really good for you. Nutritionists have made it their life's work to understand what actually does a body good. Here's how you can follow their example. Cut Back on Added Sugar I spoke ...more
Voicemails are like chores for me. I have to listen to them, but never really feel like doing it. When I finally do, most of them get deleted right away, but every so often they'll be one I save and listen to over and over again, whether it's a cute birthday wish from grandma ...more
Loaded with a gorgeous display and a powerful processor, the Kindle Fire HDX is an impressive all-around tablet, especially when it's used for what Amazon Kindles were built for—reading electronic versions of novels, textbooks, and other printed works. While the Kindle Store ...more