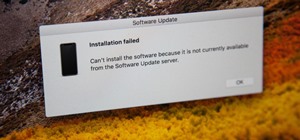
UnrealIRCd is an open-source IRC server that has been around since 1999 and is perhaps the most widely used one today. Version 3.2.8.1 was vulnerable to remote code execution due to a backdoor in the software. Today, we will be exploiting the vulnerability with Metasploit, exa ...more
SMB (Server Message Block) is a protocol that allows resources on the same network to share files, browse the network, and print over the network. It was initially used on Windows, but Unix systems can use SMB through Samba. Today, we will be using a tool called Enum4linux to ...more
Google Docs is made for teamwork and collaboration, but Apple's iWork suite also comes with the same functionality. If you're working on a Pages document on your iPhone, and you want input from other members of your team, you can easily invite them to view, comment, edit, and ...more
Apple's Reminders app has always been an underrated yet useful productivity tool for iPhone. It's not as powerful as many third-party to-do apps, but it makes it easy to keep track of a few basic tasks, and it's integrated deeply with iOS, macOS, and watchOS. In iOS 13, it's e ...more
For those with small hands, smartphones have gotten out of control as of late. Nearly every flagship phone is over six inches in length, so many are forced to use phones that are too big for them and hope they don't fall. Well, thanks to one developer, using these phones can b ...more
Phone numbers often contain clues to the owner's identity and can bring up a lot of data during an OSINT investigation. Starting with a phone number, we can search through a large number of online databases with only a few clicks to discover information about a phone number. I ...more
Gathering information on an online target can be a time-consuming activity, especially if you only need specific pieces of information about a target with a lot of subdomains. We can use a web crawler designed for OSINT called Photon to do the heavy lifting, sifting through UR ...more
Microsoft Office files can be password-protected in order to prevent tampering and ensure data integrity. But password-protected documents from earlier versions of Office are susceptible to having their hashes extracted with a simple program called office2john. Those extracted ...more
The ability to stay organized and be resourceful with data gathered from recon is one of the things that separates the true hackers from the script kiddies. Metasploit contains a built-in database that allows for efficient storage of information and the ability to utilize that ...more
The Pixel 3 XL versus Galaxy Note 9. Stock Android versus Samsung Experience. When I began this comparison, I thought the Pixel 3 XL would be unfairly outmatched. But after looking at the specs side-by-side, you'll see a different picture. This year, Google delivered a worthy ...more
One of the issues with rooting your device is the inability to update your phone via OTA. Any security patches or software updates pushed out by the OEM are lost because your bootloader is unlocked. However, you still can update your device, it just a take a bit more effort. ...more
Continuing our NR30 series this week, we focused on the leaders of the software development industry that make augmented reality experiences possible. In other news, two of the current leaders in making AR headsets, Microsoft and Magic Leap, are pursuing multiple verticals wit ...more
It's important to know who you're dealing with after hacking your target's MacBook. Getting remote access is simple, but covertly gathering information about the user and their system can be a challenge. Continuing with our situational awareness attacks, we'll be further orie ...more
One of the first steps in reconnaissance is determining the open ports on a system. Nmap is widely considered the undisputed king of port scanning, but certain situations call for different tools. Metasploit makes it easy to conduct port scanning from directly inside the frame ...more
As Android bug bounty hunters and penetration testers, we need a properly configured environment to work in when testing exploits and looking for vulnerabilities. This could mean a virtual Android operating system or a dedicated network for capturing requests and performing ma ...more
After first being announced at Mobile World Congress 2018, the ASUS ZenFone 5Z will finally be coming to the US. Deemed an iPhone X clone by some, there is more than meets the eye when it comes to this flasghip. While it is similar to the iPhone X, in some ways, it improves on ...more
Have you ever seen pictures or videos of balloons being let go into the sky and randomly floating away in all directions? It's something you often see in classic posters or movies. Well, guess what? Now you'll be able to do that without having to buy hundreds of balloons, all ...more
LG is really coming strong at the flagship smartphone market in 2018. They have already released three new flagship caliber smartphones this year: the V30S ThinQ, V35 ThinQ, and the G7 ThinQ. But LG isn't done with flagship phones yet — they've just announced the V40 ThinQ. T ...more
For most carriers, "unlimited" data plans aren't really unlimited, and they still cost more than data limited plans. So while subscribing to music streaming services and storing your own music library in the cloud may be more convenient, it may eat your data up like candy. To ...more
After two years of poor sales, LG decided to shake up its mobile division. New executives are at the helm, and changes to their flagship lineups are already underway. Specifically, the V series is expanding, as LG announced the second new device in the series, the LG V35 ThinQ ...more
One major problem in previous iOS versions is that there was no way to keep messages in sync between an iPad, iPhone, iPod touch, and Mac. If you deleted a message in the Mac app, it would not be deleted on your iPhone, and vice versa. Apple finally fixed this issue in iOS 11. ...more
Whether you're white hat, black hat, or some shade in-between, navigating through a network is a core part of hacking. To do that, we need to be able to explore a network to discover the addresses of gateways, interfaces, and other attached devices. When ifconfig just isn't en ...more
Karen Gillan must have had an absolute blast chewing the scenery as Nebula in Guardians of the Galaxy Vol. 2, seeing as how Nebula is a ball of pure, seething fury pretty much 24/7. Combine that larger-than-life personality with her iconic blue and silver cyborg look, and you ...more
Every other year, Apple comes out with "S" model iPhones that enhance and speed up their main series models from the previous year. This year, however, because of the highly-anticipated 10th anniversary iPhone, aka the iPhone X, Apple has dropped the "S" and moved straight to ...more
In my previous article, I discussed installing and configuring OpenVAS on Kali Linux. Now it's time to start using OpenVAS with the Greenbone Security Assistant to audit networks for security issues. This can be extremely helpful when you are looking for vulnerabilities or mis ...more
OpenVAS is a powerful vulnerability assessment tool. Forked from Nessus after Nessus became a proprietary product, OpenVAS stepped in to fill the niche. OpenVAS really shines for information gathering in large networks where manual scanning to establish a foothold can be time- ...more
Nothing has stopped you from taking a screenshot of a funny moment in a FaceTime video call before, and nothing probably will. But screenshots are old news. Apple has made it even easier to take capture FaceTime moments on your iPhone, and the results are more lively. Unlike ...more
Data for mapping and other applications is the lifeblood of machine-driven cars, and so far, Tesla has taken a definitive lead in information it has gathered ahead of other driverless players, including Waymo. But Tesla's position could be short-lived, if the world's largest ...more
As pentesters and hackers, we're going to be working with text frequently — wordlists, configuration files, etc. A lot of this we'll be doing on our machine, where we have access to whatever editor we prefer. The rest of it will be on remote machines, where the tools for editi ...more
Gaining access to a system is always exciting, but where do you go from there? Root or bust. Sure, a compromised host is a great way to run a botnet, or do some other boring, nefarious thing—but as hackers, we want root. We also want to take the easiest path possible, search o ...more
Throwaway phones aren't just for seedy criminals and spies—they can be useful for many everyday situations. For example, you don't necessarily want to give your real phone number out to strangers when you're buying or selling something on Craigslist, managing an Airbnb listin ...more
We've always loved a good summertime hot dog, placed lovingly in a soft simple bun with ample ketchup and mustard. But after eating hot dogs this way and this way alone for the majority of our lives, we grew tired of the same old thing. Enter: The search for the 10 best hot d ...more
Hello everybody. I'm back with Part-2 of this series. In this part we will be programming in C our server and i will be explaining one more "key concept" so everybody got a better understanding on this. Ok first let's see that concept. Little Endian and Big Endian So, as pe ...more
We already know that Samsung's Galaxy S7 is one of the most versatile smartphones ever made, complete with edge-to-edge displays, water resistance, and a huge battery. But what's versatility without durability? How much punishment can the Galaxy S7 take? Let's play a game of S ...more
Welcome back everyone. I apologize for the lack of training articles, but I've been rater busy lately. I've recently picked up a second job and my college courses are now back in session, so I'm a bit strapped for time. FTP is a very important protocol. It's not only importan ...more
Welcome back, my tenderfoot hackers! As you should know from before, Snort is the most widely deployed intrusion detection system (IDS) in the world, and every hacker and IT security professional should be familiar with it. Hackers need to understand it for evasion, and IT se ...more
When performing something such as a mass mailer attack on a company, sending executables usually isn't the best option. That's why, in this tutorial, I'll be teaching you how to code a VBA script macro into a Word document in order to compromise a system. Combined with a littl ...more
What's up readers? Today I'll be introducing to you a new vulnerability called the Format String vulnerability (in case you missed the title). It won't be much, just a little motivation to keep you guys going. A little teaser, if you may. Pre-requisite information: For those ...more
These days, if you're having friends over, they'll probably ask to log into your Wi-Fi network before asking for a drink. But if you've forgotten your password, it can be quite hard to find, since most devices obscure the characters with asterisks. But it honestly doesn't tak ...more
Welcome back, my nascent hackers! In the conclusion of the Mr. Robot television series, Elliot and fsociety successfully completed their mission of encrypting all of Evil Corp's data with AES-128 encryption and destroying the key. Now that all of the data on Evil Corp's serv ...more
Amazon is slowly trying to gain as much influence in the tech world as it has in the consumer market, and with the Amazon Fire HD 7, they have their eyes set on taking on the "budget tablet" space. For the amount of money you spend on the Fire HD 7, you get a pretty decent ta ...more
Like the majestic mountain structure it's named after, Apple's latest version of OS X, El Capitan, goes a little deeper to expand on the foundation laid by Yosemite. While the update may not be as monumental as some have hoped, it is an improvement and includes tons of useful ...more
Welcome back, my novice hackers! This new series on Bluetooth hacking was inspired by a recent episode of Mr. Robot (my favorite TV show). In episode 6, Eliot hacked the bluetooth keyboard of the police office in order to hack the prison and release his nemesis, Vera. This is ...more
Developing GUI apps in python is really cool. I ask those who understand the language to help convert some of the command-line or console programs or apps ( I mean programs that are useful to a hacker ) to GUI. I know GUI makes us lazy and not wanna learn but we should all kno ...more
Welcome back, my aspiring hackers! Although this article may have been better placed first in this series, I doubt that anyone would have read it when just starting out studying Linux. Now, that you are well into your Linux studies and have some familiarity with how it operat ...more
Your waffle maker might just be the most underutilized tool in your kitchen. This one appliance can make bacon, eggs, hash browns, cupcakes, falafel, mac and cheese, and cinnamon rolls much more quickly and with less mess than traditional methods. Plus, the results all come ou ...more
If you took a big step back and really looked at the world, you'd see how downright silly our nations look when they put up fences to separate themselves from one another. Creatures big and small roam free while respecting each other's space, but humans create borders and phys ...more
Audiobooks are great because they require little-to-no effort on your behalf. When driving in traffic, why not listen to George R.R. Martin's lengthy A Feast for Crows instead of repetitive, commercial-laden radio? Maybe it harks back to prepubescent bedtime readings, but havi ...more
While most of us don't think twice about dragging a pattern or using Touch ID to open our phones, or entering a password in for our email and bank accounts, these features are there to protect some of our most private information. Only problem is, they don't do a good job of i ...more
Welcome back, my budding hackers. So many of you are interested in hacking Wi-Fi that I have decided to revisit my Wi-Fi Hacking series with some updated and more in-depth material. I strongly suggest that you look at some of my earlier posts, such as "Getting Started with Te ...more
While the preview images for Android's upcoming "L" release just came out yesterday, the new firmware has already been rooted, as is standard with its openness. So if you were feeling reluctant to try Android L because it didn't support existing root methods, then you might wa ...more
It used to be easy to hack tethering—root your device and install a third-party or modded tethering app. But snuck in amongst the changes in Android 4.3, a new data-monitoring service of sorts made its debut. There used to be a time when your data connection was yours. You pai ...more
Welcome back, my neophyte hackers! Many newbie hackers seem to be confused regarding the process or methodology to employ a successful hack. Most want to simply go straight to the exploit without doing the due diligence to make certain that the hack will work and you won't ge ...more
Welcome back, my fledgling hackers! A short while ago, I did a tutorial on conducting passive OS fingerprinting with p0f. As you remember, p0f is different from other operating system fingerprinting tools as it does not send any packets to the target, instead it simply takes ...more
Welcome back, my novice hackers! There are SOOOO many ways to hack a system or network, which means you need to think creatively in order to be successful. Many novice hackers focus way too much energy on cracking passwords (which should be a last resort unless you have spec ...more
Unless you're a pretty avid home cook, you probably don't know a lot about sous vide. Sous vide is a low-temperature cooking method where food is cooked in vacuum-sealed plastic bags in a water bath for a prolonged period of time. Sous vide machines are used mostly in high-en ...more
Welcome back, my greenhorn hackers. When Wi-Fi was first developed in the late 1990s, Wired Equivalent Privacy was created to give wireless communications confidentiality. WEP, as it became known, proved terribly flawed and easily cracked. You can read more about that in my b ...more
Welcome back, my greenhorn hackers! Now that we're familiar with the technologies, terminology, and the aircrack-ng suite, we can finally start hacking Wi-Fi. Our first task will be to creating an evil twin access point. Many new hackers are anxious to crack Wi-Fi passwords t ...more
Apple is widely known for keeping a tight grip on iOS, disallowing open-source and third-party downloads. While there are many reasons for this, the three most frequently referenced are quality control, malware prevention, and of course—money. The number one reason why Apple ...more
The iPod changed the music and electronics industries when it was first introduced way back in 2001. It is credited with ushering in the age of "connected devices," and has held a huge market share of around 70% for years. At the height of its popularity, the iPod made up almo ...more