Welcome back, my novice hackers! This next subject might seem a bit obscure, but I promise you, this lesson will benefit you significantly either as a hacker or system admin. This tutorial will cover what is usually referred to as a regular expression, or regex for short. Ma ...more
Apple's latest mobile operating system, iOS 9, may not be the huge overhaul that iOS 8 was, but that doesn't mean there aren't plenty of new features. In fact, there are a ton of subtle changes that you may not notice right away. Here's a rundown of all the coolest new feature ...more
Instagram is addicting — and that's done on purpose. To stop your Instagram habits, your smartphone likely has a built-in feature to curb the daily usage of a particular app, like Apple's Screen Time for iOS and Google's Digital Wellbeing for Android. But you don't need to mes ...more
Does your Activity page on Instagram feel cluttered? You're not alone. Instagram lumps all alerts into one long, chaotic timeline, so if you want to see comments or likes, you have to weed through everything else including shares from other users, memories, recommendations, an ...more
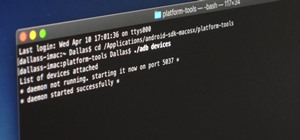
There once was a time in the Android rooting scene where we couldn't rely on using a custom recovery for all of our modding needs. Manual file flashing was very popular in the early days of Android before custom recoveries started taking over. With the rise of TWRP, it seemed ...more
In this jam-packed October, the Huawei Mate 20 Pro has flown under the radar in the US. Due to Huawei's lack of presence in the States, many are unfamiliar with the second largest OEM in the world. Huawei has continuously put out amazing mobile devices, and this year they rele ...more
I don't know about you, but I'm tired of hearing some of the same old jargon from people online who claim that all you need to make it on Instagram is to take good pictures and post consistently. Yes, for sure, but do you really think it's that easy? Instagram, if you're seri ...more
If you are a small account looking to get more followers and likes, then getting past Instagram's 30 hashtag limit may be what you need to increase engagement. While I don't recommend posting so many hashtags in your caption (it looks terrible), there are certain ways to add t ...more
Every year, tech companies use April 1st as a means to prove that they have a sense of humor. Sometimes their jokes are good for a chuckle, other times the gags backfire disastrously. For the most part, however, we'd be better off without the bulk of these annual antics. But ...more
It always looks different when it's not about you. The Internet is our world's Alterego. Those many bits don't really make sense unless we want them to be valuable, to mean something. Our rush to the future is too fast to keep up with. Denying technology is ignorance, isolat ...more
Whether it's for handling your business's social media account or just for personal reasons, like trolling an ex-girlfriend's page (not that I've ever done that) or posting on behalf of your pup, there are instances where having two different Facebook accounts on one device is ...more
Welcome back my fellow hackers. Today I'm going to teach you how to preform an Idle Scan. You may be asking what is an Idle Scan. Its a very stealthy scan because you don't use your own ip you use a zombie (in computer terms). Heads up. If you are root you don't need the sudo ...more
Well Welcome Back My Fellow Hackers. What is Slowhttptest? You may be asking. Slowhttptest is a Application Layer Denial of Service attack aka an attack on HTTP. You can read more about it here and also download it if you don't have Kali Linux. slowhttptest - Application Laye ...more
Instagram is all about sharing and interacting with others, but sometimes we hide in the shadows and lurk. Whether their ex-lovers, current crushes, former high school classmates, or future coworkers, we silently view their content without them knowing. You can deny it all you ...more
There are plenty of reasons not to use location information when you tweet, whether you're trying to stay safe or just don't want your crazy ex showing up while you're in line at the grocery store. But a new website called 'Please Don't Stalk Me' could actually make broadcasti ...more
Okay, so you rooted your Android phone .... now what? There are a few ducks you need to get into a row, like backing up your stock boot image, getting SafetyNet sorted, and improving security with biometrics. But there are also awesome root mods waiting for you — just don't ge ...more
Whether it becomes mandatory or not to show your COVID-19 vaccination card at events, restaurants, bars, hotels, airports, and other public places, it's a good idea to digitize the paper card on your smartphone so that it's always with you. It's also wise to give yourself quic ...more
You can mod every aspect of your phone's software with root, but if you want to make changes at the hardware level, you'll need a custom kernel. If you've looked into custom kernels before, one name undoubtedly kept coming up: ElementalX. It's easily the best custom kernel out ...more
Rooting. As an Android user, I'm sure you've heard the word once or twice. According to Kaspersky, 7.6% of all Android users root — but for the 92.4% who don't, we wanted to talk to you. Rooting allows you to remove barriers and open Android to a level of unprecedented contro ...more
Mobile wallet Curve just released a new feature that lets you correct past mistakes. Sounds incredible, right? Unfortunately, the mistakes you can erase aren't things like forgetting to do an assignment in school, screwing up a job interview, or, well, your ex. However, you ca ...more
When will the drama end? The lawsuit between Waymo and Uber is back in the news with no signs of stopping. Today the court denied yet another request from Uber to shield itself with the fifth amendemnent, securing a small victory for Waymo. Let's recap where we are with this ...more
A new app called Roadie now makes life a little easier by connecting users to people who can transport their stuff. The app allows users to transport anything from dogs to getting rid of your ex's things. Furthermore, anyone can register as a sender, or become a driver to make ...more
When developing for the HoloLens, keeping a constant 60 fps (frames per second) while making things look beautiful is a challenge. Balancing the processing power to display complex models and keeping the frame rate where it needs is just a straight up painful process, but a so ...more
Thanks to a newly discovered iOS exploit, a text message can now ruin your day. It will literally cripple your iPhone, and the worst thing is that anyone with a phone that supports double-byte unicode can do it to you. While it initially sounded like bullshit, we tried it out ...more
It's becoming more and more apparent that Siri continually drops the ball when it comes to lock screen security. In the past, Siri was exploited in iOS 7.0.2 to send messages without needing a passcode. Then in iOS 7.1.1, Siri was use to bypass the lock screen again to access ...more
Log in to your LinkedIn profile, and you'll immediately be prompted to check out who's peeked at your profile. With one click, you can discover how many recruiters, companies, and random people have viewed your online resume. Every page you visit is tracked, and everyone know ...more
When we take pictures with our smartphones, it’s safe to assume we’re taking more than one. We're either trying to capture the right light, look, or expression… or maybe a slight nod to the right to show off your good side. Whatever the case may be, taking many pictures is an ...more
Facebook has been looking to launch a new product for a while now, and it seems they've finally realized what they're best at—being as creepy as possible. If you thought your boss checking out your girlfriend's beach photos was weird, Facebook's new Graph Search has only upped ...more
You might have missed it, but the virtual keypad you use to enter phone numbers in your smartphone's dialer and contacts app isn't all numbers. Take a closer look, and you'll notice a few mysterious buttons you've likely been tuning out unconsciously. But it's time to stop ign ...more
The Calculator app is probably one of Apple's most-used iPhone apps, yet I always meet people who don't know all the little tricks there are to using it more efficiently. You may know most of them, but there's a chance you don't or at least forget about some of them. What a " ...more
Xiaomi made a new phone with their sights set on picking up some ex OnePlus users. As a result, the Pocophone F1, or just Poco in some markets, is quite unlike most other Xiaomi phones. While you can't buy the F1 in stores in the US, you can get its home screen app on almost a ...more
Last week's Augmented World Expo felt like a distant memory by this Monday, as Apple unveiled ARKit 2.0 at its annual Worldwide Developers Conference. Certainly, this news would overshadow anything augmented reality this week as it nearly eclipsed AWE when early reports leaked ...more
Noted poet T.S. Elliot once wrote that "April is the cruelest month." But Magic Leap might argue that March is the most miserable, as the Ides of March brought more legal woes to augmented reality startup. Elsewhere, its closely-held branding secrets have been spilled by way o ...more
Whether inappropriate or unimportant, some emails don't need to be viewed at a certain times of the day. For example, you might not want to see any personal emails during work hours. By default, Gmail will notify you of all emails that hit your inbox, but fortunately, there's ...more
I thought eventually that my ex's Instagram account would magically clear from my "Suggested" search history. It's been six months now, and I'm sorry, babe, but enough is enough. It's time to clear out your very cute face. (On Instagram, of course.) I don't want to be reminde ...more
Today's pollution, hectic lifestyle, inadequate sleep and no time for pampering can leave your skin lackluster resulting in drying skin and making dry skin drier ultimately causing the early appearance of wrinkles and aging. A good fruit facial helps relax your skin from deep ...more
Finding the motivation to make a change can be tricky. It's difficult to resist the urge to procrastinate, or even give up when goals seem distant and difficult. If you wish you could stick to your New Year's resolutions, or maybe even just commit to pursuing smaller goals, yo ...more
There is a whole world of smartphone accessories out there, some of which are more quirky than others and don't get the recognition they deserve. But these sometimes strange, sometimes embarrassing products can really make life easier on your iPhone or Android phone. We've fo ...more
After you unlock the bootloader, install TWRP custom recovery, and flash Magisk to gain root access, what might be the next step of your modding adventure? A custom kernel, of course! Flashing a custom kernel onto your device gives you a whole new level of tweaks and customiza ...more
Seeing that wonderful blue verified badge on Twitter really adds something to your public persona, doesn't it? That's why, when I found out that the average person could get verified on Twitter with the right tools, I jumped on the chance to add that little blue check to my ow ...more
When it comes to modding an Android device, a custom kernel can take you farther than almost anything else. Most offer the ability to overclock your processor for performance gains, change your CPU governor, or even under-volt to increase battery life, among other features. O ...more
In this tutorial I am going to show you how to create an undetectable Meterpreter Trojan using a Domain name. I have taken a few guides/tutorials and built it into one. The first part is creating the DNS Payload. The second part is creating the Executable file. Part 3 is using ...more
Third-party keyboards have been available for iPhone ever since iOS 8, but which ones are worth checking out? There have been many options over the years, and if you want keyboard features like swipe-typing and themes, you're going to have to put Apple's stock QuickType keyboa ...more
In the UK, 20 percent of divorce filings include the word "Facebook." You may think you're being slick by using the site to chat with your ex, but the problem is that Facebook saves everything, and I mean everything. All someone needs is your login information and they have ac ...more
When you unlock the bootloader on your Essential PH-1, you open your device to a host of new possible tweaks. One popular modification is a custom kernel, which can not only speed up your phone, but give you new features that wouldn't be possible otherwise. The kernel control ...more
You don't need an obsessive ex stalking you to benefit from the ability to record calls on your iPhone in a pinch. Besides protecting yourself from nefarious intent, recording important conversations like verbal contracts and agreements can help you cover all your bases and en ...more
Some of us woke up at the KRACK of dawn to begin reading about the latest serious vulnerability that impacts the vast majority of users on Wi-Fi. If you weren't one of those early readers, I'm talking about the Key Reinstallation Attack, which affects nearly all Wi-Fi devices. ...more
hello my dear colleagues, I made a visit to nullbyte and found that there is not a complete tutorial about the google dorks, so I felt the need for this tutorial, and seeing that there are many newbies around, so here's a tutorial that will teach you how to use google to hack. ...more
In my last guide, I showed how you could crack the combination of any Master Lock combination padlock in 8 tries or less using my online calculator. Now, as promised, I'll be showing you how I devised the attack, which is based off the well-known technique that reduces the 64, ...more
Microsoft's first venture into the tablet market, the Surface RT, combines many of the capabilities of a normal Windows 8 laptop into a super compact tablet, whose super-thin touch cover and kickstand can transform it into a functional mini-laptop, small and light enough to go ...more
Despite its rocky start, the Essential PH-1 has a lot going for it. Not only does it get consistent security patches and system updates hours after the Pixels, but like the Google-developed lineup, it's also great for rooting. Not only is your warranty not void with rooting, b ...more
With the release of the Pixel 2 XL and the iPhone X, smartphones have hit a new high not just in price, but also raw processing power. These new flagships not only cost more than twice as much as an Xbox One or PlayStation 4, they have also become almost as powerful as far as ...more
Unruly customers. Crazy exes. Horrible bosses. When you need proof of insanity or just want it for your records, recording a phone call is a must. Problem is, it's not the easiest thing to do on an iPhone — but it's completely possible. Even though there are plenty of legit r ...more
Everything you post on social media lives there forever — even if you delete it. Just ask anyone that's ever posted something stupid. Instagram does not provide built-in tools to save or download images and videos from other users, but there are workarounds. Third-party tools ...more
You might think that you have your microwave all figured out, but chances are you don't know all of its secrets. Some microwave tricks are truly hidden; obscure information nowhere to be seen in the user manuals. Other tricks are hiding in plain sight, often overlooked or toss ...more
At launch, Chromecast with Google TV is fairly limited in the number of compatible apps. Many of the usual suspects are there, but there are some interesting omissions, like Google Stadia (though support is coming). However, at its core, the device runs on Android 10, which me ...more