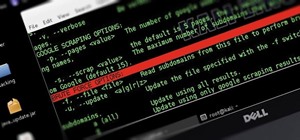
Before we dive any further into getting your Mac ready for hacking, I wanted to continue on with the concept of encryption. In the last part, we talked about full disk encryption on your Mac, but now I want to quickly cover the encryption of disk images before we dive into man ...more
Apple caught a lot of flak for removing the headphone jack in their iPhone 7 models, but they definitely got the last laugh when preorders with a delivery date of September 16 sold out within minutes. Headphone jack or not, the iPhone 7 and 7 Plus are still highly desirable pr ...more
Android has a single text file named build.prop that determines tons of various system-wide settings on your device. You need root access to edit this file, since it's stored on the system partition—but the various lines of codes it contains are actually fairly easy to interpr ...more
If you use Google Chrome as your default desktop/laptop browser, then Chrome OS will be pretty easy to get up and running if transitioning from Windows or macOS. Google has created an operating system that is fast, lightweight, and versatile enough to be adopted by pros and no ...more
When you think of Terminal, you probably imagine some hacker sitting in front of their computer in a dimly lit room trying to break into an FBI database. In reality, it's just a simple tool that can make using your Mac much easier. Now, I'm not saying that learning Terminal c ...more
As I've explained before, black app backgrounds save you a bit of battery life on your Samsung Galaxy S5. This is because the AMOLED display on your S5 does not have to power pixels or a backlight for portions of the screen that are black. Developer Kdio knows this, and that' ...more
The integration of technology into automobiles is becoming more and more widespread each year. Tesla's Model S features a 17" display in the middle of the dash with navigation, music control, and even an Internet browser. Mercedes is working on incorporating Google Glass into ...more
The price of hacking Wi-Fi has fallen dramatically, and low-cost microcontrollers are increasingly being turned into cheap yet powerful hacking tools. One of the most popular is the ESP8266, an Arduino-programmable chip on which the Wi-Fi Deauther project is based. On this ine ...more
Smartphones are like high tech buckets that collect our personal information through constant use. This has some obvious benefits, like getting a more personalized experience with our devices. On the other hand, this data is a tempting target for bad actors looking to make a b ...more
If you're one who enjoys a good DIY project, or if you're just tired of paying exorbitant labor fees to have your vehicle serviced every 5,000 miles, changing your own oil can be a rewarding endeavor. Even though cars and trucks are becoming increasingly over-engineered these ...more
Kali Linux has come a long way since its BackTrack days, and it's still widely considered the ultimate Linux distribution for penetration testing. The system has undergone quite the transformation since its old days and includes an updated look, improved performance, and some ...more
Samsung decided to jump into the foldable category early, announcing the Galaxy Fold in February 2019. After a major hiccup, Samsung released the phone four months later to praise. But Samsung's not finished with foldables, as the new Galaxy Z Flip is just on the horizon. Sam ...more
When Facebook launched its first hardware products last year, the Portal and Portal+ smart displays, the company mostly touted its video-calling features as it faced off against Amazon and its Echo Show. But Facebook also had an interesting feature that mostly flew under the ...more
For 2019, Sony is trying to shake its failures of the past and start fresh. Following the unsuccessful Xperia XZ series, Sony is changing the name of their flagship to a single number: Xperia 1. With the name change comes a few upgrades, one of which is its new look. Secondly, ...more
It is almost indisputable that smartglasses and head-worn displays are the future of augmented reality. However, at this precise moment, they are still a very niche market. Those who have been in the presence of a HoloLens, Meta 2, or Magic Leap One have witnessed how powerfu ...more
For anyone using open source information to conduct an investigation, a balance between powerful tools and privacy controls are a must. Buscador is a virtual machine packed full of useful OSINT tools and streamlined for online research. This program can easily be set up in Vir ...more
Razer just released their first flagship Android smartphone, appropriately named the Razer Phone. While mobile gaming fans are sure to enjoy the Razer Phone, the buttery-smooth 120 Hz display makes this an appealing option for anyone in the market for a new phone. If you've ju ...more
The last quarter of 2017 brought us some downright excellent smartphones. Between the iPhone X, Pixel 2, and Note 8, consumers have more fantastic options than ever when choosing a new device. It's now the perfect opportunity for Samsung to set the tone for 2018 smartphones wi ...more
One major component of Level 4 and Level 5 driverless cars is in very short supply. Venture capitalists and engineers from around the world are racing to fill the LiDAR production, price, and performance void. Production of LiDAR sensors is seeing months-long production bottl ...more
In mid-November, Vuforia officially released Vuforia 6.1, which has full support for the Microsoft HoloLens. They also released their AR Starter Kit to the Unity Asset Store, which contains scenes that show you how to use Vuforia features. While I have yet to find any confirma ...more
Thought I would cross-post a piece I did a while ago. So here is a piece I made a while back. I found this brass and glass bottle at the thrift store. At the time of purchase it had a broken music box on the bottom. I actually was able to fix the music box and it plays "How D ...more
There are tons of different versions of maze games. First, there were paper mazes that you had to draw your way out of. Then, there were computer and video games, and later, smartphone apps. Now, Windows Phone developer Matt Cavanagh has put a modern twist on the classic by c ...more
Google Glass, the augmented reality head-mounted display, has sent ripples through the technology world ever since its inception in 2012—even warranting Time Magazine to recognize it as one of the "Best Inventions of the Year 2012". Today, Google announced that it’s now openin ...more
LEGO has not attempted a blimp, zeppelin, or similar airship since 1999, the 5956 Expedition Balloon which used highly specialized parts. This is unfortunate as these vessels are well and truly part of the pulpy adventure and steampunk scene. I think Ssorg's Majestic Airship ...more
So you bought a new flat screen, and now you have to tackle the next issue—you have to mount it somewhere. Most people go for the wall, which is the most obvious place, but if you want to go for something a little different, the ceiling is always an option, too. There are ple ...more
Need a camera stabilizer, but don't have the cash? With an old pair of jeans, a bag of lentils, and an hour or two of your time, you can make one for cheap. Maybe even free, if you have a bag of those legumes already. This tutorial comes courtesy of Jeff Meyer on TechRadar. H ...more
Love old-school games like Pac-Man and Space Invaders, but don't have the extra space for an arcade machine? Get the best of both worlds (and save some cash) with this DIY Arcade Coffee Table built by Sam Wang. He started with just an ordinary IKEA table and drawers, then cut ...more
Want an electric car without the price tag? You could always build your own, or maybe just hack your old gas guzzler into an eco-friendly electric machine... This weekend at Defcon, security consultant David Brown showed off his "Voltswagon" project, a 1974 Beetle named Shocky ...more
So this is what I did for the dashbount phone holder. I used a cologne box. A lot of them come with another box inside thats much more sturdier than the one on the ouside. I didnt take pictures from the beginning so bear with me. Heres what the finished box looks like: Just ...more
Fireworks are the best part about the Fourth of July and other celebrations, but they can easily cause accidental injuries. It's both safer and more fun to set them off remotely, so we'll hack some standard fireworks with nichrome wire, a relay, and an Arduino to ignite remote ...more
Apple CEO Tim Cook has said that augmented reality (or, AR for short) will "change everything." But what, exactly, is augmented reality? Generally, augmented reality refers to the process of presenting virtual objects and imagery — usually through a wearable lens or external ...more
After years of rumors and waiting, Samsung's first foldable smartphone is finally a reality. The phone itself is a bit wild, but with Samsung going so far out of their comfort zone with this one, there were some bumps in the road that caused a delayed release. The launch has b ...more
It's the icing on top of your cake (or whipped cream on top of your Android Pie) of despair. You may have not had the easiest time rooting your device, but you feel like you overcame all of the obstacles. Only now to discover that those very apps and mods you were rooting for ...more
With smartphone cameras and software getting better and better every year, more and more users are getting passionate about photography. So when you're shopping for a gift to get someone, if they have a smartphone, chances are they'll more than appreciate some tools and access ...more
The "controversial" Pixel. No phone in the history of Google's Pixel lineup deserves this title more than the Pixel 3 XL. For some (including myself), the design is a welcome change that embodies the modern design of 2018 flagship phones. For others, it has an ugly huge displa ...more
If you want to follow Null Byte tutorials and try out Kali Linux, the Raspberry Pi is a perfect way to start. In 2018, the Raspberry Pi 3 Model B+ was released featuring a better CPU, Wi-Fi, Bluetooth, and Ethernet built in. Our recommended Kali Pi kit for beginners learning e ...more
The Raspberry Pi is a credit card-sized computer that can crack Wi-Fi, clone key cards, break into laptops, and even clone an existing Wi-Fi network to trick users into connecting to the Pi instead. It can jam Wi-Fi for blocks, track cell phones, listen in on police scanners, ...more
When Steve Jobs introduced the first iPhone, he pointed out that the biggest problem with physical keyboards on mobile phones is that they're always there, whether you need them or not. Now, 17 years later, a new company is bringing us full circle, giving us the best of both w ...more
If you're ever in a situation where you need to take a peek at the wireless spectrum, whether it's for Bluetooth or Wi-Fi devices, there's a fascinating Python 3-based tool called Sparrow-wifi you should check out. It's cross-platform, easy to use, and has an impressive GUI th ...more
Following on the heels of the announcement that ThirdEye's Gen X2 MR glasses began shipping in September, ThirdEye has revealed it has developed an app that helps soldiers aim their weapons during battle situations. The company just posted a short clip of a soldier using the ...more
After teasing what smartglasses powered by Snapchat might look like with two product cycles of camera glasses, Snap has now added augmented reality capabilities to its third take on Spectacles. On Tuesday, the company unveiled Spectacles 3, which packs a pair of temple-mounte ...more
After improving hand-tracking and adding multi-user sharing features in the last Lumin OS update, Magic Leap has upped the ante yet again. In the Lumin OS 0.95 update (accompanied by SDK 0.21), Magic Leap introduced tracking for eight key poses from varying positions, as well ...more
For the uninitiated, it can be difficult to buy that special hacker in your life a perfect holiday gift. That's why we've taken out the guesswork and curated a list of the top 20 most popular items our readers are buying. Whether you're buying a gift for a friend or have been ...more
Hackers often rely on lazy system admins and unpatched vulnerabilities to get access to a host. Keeping intruders off of our machines requires us to update daily, only run the services we need, and read the code, among other things, but we can still make mistakes. Luckily for ...more
Update: Monday, 11 p.m. ET: In a report from Bloomberg, eMagin CEO Jeffrey Lucas has contradicted what appeared to be investor information found in SEC filings that surfaced on Monday. Although Apple is listed among several other investors in the company in filing, Lucas told ...more
Until self-driving cars become mainstream, augmented reality might be the next big technology to hit your dashboard. AR navigation company WayRay recently walked away with the grand prize at the AutoMobility LA trade show, beating out nine other startups with innovations incl ...more
Apple has sprung a massive AR following since the announcement of their ARKit, with users waiting to see what exactly the tech giant will do next. Now, thanks to a patent application published today, we might have an idea of what's coming: augmented reality glasses. The rumo ...more
Modern warfare takes on a more literal translation with the advent of new augmented reality displays revealed recently by the US Army to improve soldiers' situational awareness on the battlefield. A new helmet-mounted displays, named Tactical Augmented Reality (TAR), integrat ...more
Most popular virtual reality headsets, like the HTC Vive and Oculus Rift, require a tethered connection to the computer and that imposes some obvious restrictions on how much we can move in our space. We'd all prefer a simpler, untethered option, and Intel wants to provide jus ...more
The Nexus 5X and Nexus 6P have identical camera hardware—in fact, both use one of the highest-end camera sensors ever put into a smartphone. The only real difference between the cameras on Google's latest flagship devices is that the 6P natively supports electronic image stabi ...more
The new 007 film, Skyfall, comes out this Friday, and dreams of becoming a super-spy have taken over my mind. Only I can't afford any of James Bond's awesome gadgetry or amazing cars—and you probably can't either. But that doesn't mean you can't fake it a little by adding a t ...more
Love chess, but hate having to stop in the middle of a game when you don't have time to finish? This DIY vertical chess set made by Redditor pigthunder will ensure you never have to abandon a game again. It hangs on the wall, so you can pick up where you left off anytime. Here ...more
Everyone knows that using your phone and driving is illegal, and rightfully so. Tons of people die on the road everyday due to careless people texting or calling someone. Everybody knows that it's wrong, yet everyone still does it anyway. Unfortunately, there are some of us t ...more
When setting up your home office or giving it a makeover, the desk is the key to making the room a functional workspace. And if you're in there all day, it also has a significant impact on your health. Standing desks can help offset some of the adverse health risks associated ...more
If you can't curb your TikTok obsession, at least make it more efficient by taking your hands out of the equation. So when you're eating breakfast, working on your computer, or using your hands for another non-TikTok task, you don't even have to touch your iPhone or iPad to sc ...more
For all of its many perks — from the best iPhone camera system money can buy, to arguably the best smartphone display on the market — the iPhone 12 Pro Max is undeniably huge. It has the largest iPhone screen to date despite being 0.46 cubic inches smaller than the iPhone 11 P ...more
Last week, I updated VirtualBox on my computer since I had skipped a few versions, then I could no longer copy text or paste text from my Kali virtual machine to my host OS and vice versa. Installing the Guest Additions didn't seem to do anything, and the bidirectional shared ...more
Some investors play the short game, placing their bets on industries that show the quickest return on their investment, and, in the augmented reality space, that means the enterprise sector. RealWear is among the smartglasses makers capitalizing on enterprise AR, and the comp ...more
Back in 2018, Spotify began testing a new mobile feature that has grown very tiresome: three to eight-second looping videos that take over the entire screen. Known as Canvases, they effectively hide the cover art and lyrics of the current song — and they're still very much aro ...more
Automotive augmented reality company WayRay has set its destination for a $1 billion valuation with an estimated time of arrival of 2019, and it has just passed a major milestone towards that goal. On Tuesday, the company announced that it has closed an $80 million Series C r ...more