When you're out and about in the dangerous world of Wi-Fi, it's hard for the average computer user to stay protected, or even know what being protected entails. Little do most people know, Windows 7 has a built-in security that few people take advantage of: a VPN (Virtual Priv ...more
The dreaded moment you hope never happens—someone has stolen your laptop. You could have private information, pictures, or even private information belonging to the company you work for, all lost forever. It can cause you pain, money, or even a job. There are paid services th ...more
You walk over to your laptop, wiggle your mouse to wake up the screen, then fire up your browser to come visit Null Byte. Catching the article about Anonymous and how they presumably will not take down the Internet, you find yourself wondering... how would someone take down th ...more
In my recent Darknet series, I attempted to connect the dots on the Deep Web. I covered the two largest anonymity networks on the Internet today, Tor and I2P. While my initial four articles were meant as an introduction, I ended up receiving a lot of interesting comments and m ...more
Amazingly, a lot of people I know haven't even heard of SOPA or PIPA. Now, every English-reading person with an internet connection will finally have those two four-letter acronyms emblazoned in their minds. For the entire day today, Wikipedia's English-language site will be i ...more
Wouldn't it be nice to just sit at your buddy's house, plug into his network, and see exactly what he's doing? What if it was as easy as that? What makes packet sniffers like Wireshark such potent tools is that a majority of local area networks (LANs) are based on the shared E ...more
How to track an email address. Useful if you meet someone who says they are from somewhere e.g. LA as given in the video and you don't believe them. Go to the Rate a Bull site type in their email address and then hit return or 'find them'. The site will give you options to see ...more
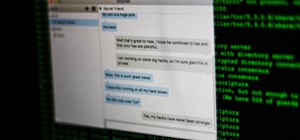
With an ordinary birthday card, we can introduce a physical device which contains malicious files into someone's home and deceive them into inserting the device into a computer. In my last series, we used a Post-it note to trick a neighbor into visiting a website that we cont ...more
Welcome back, my greenhorn hackers! In previous Wi-Fi hacking tutorials, I have shown you ways to create an Evil Twin, to DoS a wireless AP, and to crack WEP and WPA2 passwords, but in this tutorial, I will show you something a little bit different. In many restaurants, hote ...more
Want the convenience of a throwaway email address without all the hassle? How about anonymous text messaging so you can get to know someone before giving them your real information? Gliph has you covered. Gliph is a service that lets you create an identity around a set of thre ...more
Canary tokens are customizable tracking links useful for learning about who is clicking on a link and where it's being shared. Thanks to the way many apps fetch a URL preview for links shared in private chats, canary tokens can even phone home when someone checks a private cha ...more
In this how-to we will be sending an email with an image we get from a php script after running some fishy code. What you'll need Apache web server with PHP An image (included bellow) An email Account (I use gmail) Step 1: Setting Up Make a folder called "image.jpg" in your ...more
Seldom in recent history has a cyber security event caused so much media stir (maybe because it happened to a media company?) and international relations upheaval. Cyber security breaches seem to take place daily of major corporations, but the Sony hack seems to have captured ...more
It's not uncommon for hackers to attempt to move laterally between devices in proximity of a compromised device to maintain a prolonged presence in the network. Malware utilizing USB flash sticks to self-replicate and compromise air-gapped machines isn't a new concept. In bot ...more
Let's say that we want to see what someone is doing on their computer? In this tutorial, we'll be hijacking cookie sessions to do just that! Step 1: Preparing Kali In order to do this, we need three tools: Ettercap (duh) Hamster Ferret Ferret is a nice little tool that run ...more
When joining a new network, computers use the Address Resolution Protocol to discover the MAC address of other devices on the same network. A hacker can take advantage of ARP messages to silently discover the MAC and IP address of network devices or actively scan the network w ...more
After finding and monitoring nearby wireless access points and devices connected to them, hackers can use this information to bypass some types of security, like the kind used for Wi-Fi hotspots in coffee shops, hotels, and in flights high above the ground. By swapping their M ...more
With all of the bare-bones setup out of the way in our Mac for Hackers series, your Apple machine should be ready to run a significant amount of pentesting tools. We can pull tools from GitHub and compile them, we can pull dependencies or tools from Homebrew, we have both Pyth ...more
Five Phases of Hacking:- The five phases of Hacking are as follow: Reconnaissance Scanning Gaining Access Maintaining Access Covering Tracks The Five Phases of Hacking Reconnaissance:- This is the primary phase where the Hacker tries to collect as much information as possib ...more
Smartphones are inherently bad for privacy. You've basically got a tracking device in your pocket, pinging off cell towers and locking onto GPS satellites. All the while, tracking cookies, advertising IDs, and usage stats follow you around the internet. So no, there's no such ...more
The misconception that macOS is more secure than the Windows operating system is far from the truth. With just one small command, a hacker can completely take over a MacBook and control it remotely. The sheer volume of Windows computers currently in operation around the world ...more
Smartphones are still "phones," which means communicating with others is usually a primary use. Ranging from a simple "hi" to a more personal conversation and even sharing passwords, our messages should remain private so that only the intended recipient sees their content. Whi ...more
Welcome back my networking geeks. In this part we are going to keep discussing about IP Addressing and I hope after you finish reading it you will become an IP wizzard. So in the last tutorial we did what we did without the use of our default gateway. To be honest, in really ...more
Social engineering is a pretty important item in a hacker's toolkit. In Mr robot there was a time, we saw Elliot using social engineering to gain access to his therapist's boyfriend's email and bank accounts by calling him and pretending to be someone from his bank, then Elli ...more
Over the past decade the Internet community has been witness to the rise of many new forms of online interaction. These new technologies have given rise to anonymous networks (like TOR), black markets within the deep web network (like the Silk Road), and even forms of digital ...more
As a hacker or an aspiring one, You need to be careful and anonymous if your doing anything illegal. But you slipped up. Now someone is tracking you! Well luckily you read this post ahead of time and have a backup plan! The first step in remaining safe is to remain anonymous. ...more
What's your Twitter handle worth? If it's considered "desirable" (aka short and simple), it'll get you around 100 bucks, or, if you prefer, the affections of a teenage girl. A user with the handle @blanket found out the hard way that Twitter's security is atrocious when his a ...more
If you want to carry a variety of network adapters without looking suspicious, a perfect solution is accessing them through Airserv-ng. Tucked away in the Aircrack-ng suite, this tool allows a hacker to plug any number of network adapters into a Raspberry Pi and access them ov ...more
Search engines index websites on the web so you can find them more efficiently, and the same is true for internet-connected devices. Shodan indexes devices like webcams, printers, and even industrial controls into one easy-to-search database, giving hackers access to vulnerabl ...more
Automating port scanners, directory crawlers, and reconnaissance tools can be complicated for beginners just getting started with Kali Linux. Sparta solves this problem with an easy-to-use graphical interface designed to simplify a penetration tester's tasks. Sparta, authored ...more
In a previous guide, I demonstrated how to extract images from a security camera over Wi-Fi using Wireshark, provided you know the password. If you don't know the password, you can always get physical with the Hak5 Plunder Bug. Using this small LAN tap, we can intercept traffi ...more
Your social security number, credit card information, and medical history can fall into the wrong hands if you're not careful about how and where you share your data online. If you really care about your data, there are tools and techniques you can utilize to protect yourself ...more
Electronic warfare tactics work by jamming, disrupting, or disabling the technology a target uses to perform a critical function, and IoT devices are especially vulnerable to attacks. Wireless security cameras like the Nest Cam are frequently used to secure critical locations, ...more
Due to the overnight success of smartphones, millions of people are connecting with others. Currently, over 15 million text messages are sent every minute worldwide. Most of this communication is happening in the open where any hacker can intercept and share in the discussion ...more
In the world we live in now — a world of complete data overload — new ways to sort through that data moves well past "nice-to-have" and firmly into the needs category. Mind mapping has been one tool that allowed someone to break down large problems into like components and hel ...more
People have asked: "Here is an IP address. Can you hack this? Can you hack me right now?" Hacking takes time and skill. You can't just get an IP or an email and hack it in ten minutes unless the password is 1234. I say, "No. I can't really do what you want me to do like this ...more
A burner number isn't just for criminals and cheating spouses. In this digital world, with many of our interactions being conducted online, a throwaway phone number acts as a buffer — it lets you enjoy the web without having to give out your personal information, such as real ...more
In recent weeks, major bank websites around the world have experienced outages after being have been hit with Distributed Denial of Service (DDoS) attacks. Although few, if any, of these banks have been totally knocked offline, these DoS attacks have dramatically slowed the re ...more
Thanks to a couple of photoshopped images that made rounds across Twitter last year, iPhone users were duped into thinking that iOS 8 included a security feature that would lock individual apps. Of course, none of it ended up being true, but we covered other features and apps ...more
Welcome back, my rookie hackers! The more we know about a system or network, the better our chances of owning it and not leaving a trace for investigators to follow. One of the often overlooked sources for information is the Simple Network Management Protocol (SNMP). Many roo ...more
This time it's serious. Really. The largest web security vulnerability of all time went public on Monday, April 7th, 2014, resulting in widespread panic throughout the Internet as system administrators scrambled to secure their websites from the OpenSSL bug known as Heartblee ...more
You may not always want to, but there will probably be a time when you'll want to know if an email you send — like a job application or a support request — is opened by the recipient. It's actually easy to implement, and you may be using an email client on your device right no ...more
With a cheap computer, smaller than the Raspberry Pi, an attacker can create a remote hacking device. The device can be attached to a target router without anyone's knowledge and enable the hacker to perform a variety of network-based attacks from anywhere in the world. As th ...more
While there are a variety of privacy-focused search engines available like StartPage and DuckDuckGo, nothing can offer the complete trust offered by creating one's own search engine. For complete trust and security, Searx can be used as free metasearch engine which can be host ...more
In the previous article, we learned how to set up our VPS, configure our PHP server, and developed an in-depth understanding of how the payload works. With all that taken care of, we can get into disguising our payload to appear as an image and crafting the note in the greetin ...more
Welcome back my, tenderfoot hackers! Many people come to Null Byte looking to hack Facebook without the requisite skills to do so. Facebook is far from unhackable, but to do so, you will need some skills, and skill development is what Null Byte is all about. Sometimes, if yo ...more
If you've been visiting websites of ill repute, or if you've been Christmas shopping and don't want to spoil the surprise, it would be a disastrous situation if anyone were to come across your browsing history. Visited sites, cookies, and cache can paint a very clear picture o ...more
Hello again, ***UPDATE: Adding links to the other Two articles**** I recently started working on creating evil twin ap's, after reading OTW's article. I wanted to find a way to automate this process as much as I could, so I started looking for sample bash scripts and found t ...more
Part 1: What is Popcorn Time? Part 2: What is a torrent? Part 3: Why am I at risk? Part 4: What is a VPN? Part 5: Are all VPNs the same? Part 6: How do I stay protected? Part 1: What Is Popcorn Time? Popcorn Time is, essentially, a torrent client (look to Part 2 for further ...more
Welcome back, my tenderfoot hackers! A short while ago, I started a new series called "How to Spy on Anyone." The idea behind this series is that computer hacking is increasingly being used in espionage and cyber warfare, as well as by private detectives and law enforcement t ...more
With all of the productivity tweaks and usability enhancements that we cover here at Gadget Hacks, it's nice when we come across a unique and noteworthy app that's simply about having fun. This is the case with the latest offering from the development team at Privax. Their ap ...more
When browsing the web, you may not be quite as anonymous as you think, especially if you are using public WiFi. The easiest way to stay as anonymous and safe as you are going to get, is to use a VPN (there are a number of great free ones). In this tutorial, we will show you ho ...more
Welcome back, my newbie hackers! We've already saved the world from nuclear annihilation and covered our tracks afterwards, but the world is still threatened by a malicious, megalomaniacal dictator with missiles and nuclear weapons. We need to keep a close eye on him, so in ...more
If you've recently built a Wi-Fi spy camera out of an ESP32-CAM, you can use it for a variety of things. A baby monitor at night, a security camera for catching package thieves, a hidden video streamer to catch someone going somewhere they shouldn't be — you could use it for p ...more
Giving up your Wi-Fi password can be giving up more control than you think. Because of the way Chromecast and other IoT devices communicate, anyone on the same Wi-Fi network as your device can often make it do whatever they want. With a script called "Cast All the Things," we ...more
Using Netcat to backdoor a macOS device has its short-comings. If the compromised Mac goes to sleep, the Netcat background process will occasionally fail to terminate correctly; This leaves Netcat running infinitely in the background and the attacker with no new way into the d ...more
Hello Strangers, This is my first article for null-byte and its about staying anonymous on the Internet. But the question is why would you want to stay anonymous online? May be you are an vigilante hacker like me? or You don't want companies logging your Data (Also like me ...more
CEO's of IT companies doesn't know this because they are not a hacker. Only a true hacker can become a successful Security head officer. Head of Security: Well let me tell you something my good friend. Many companies we have today they are still getting attacked from hackers ...more
What if someone asks you to do a Nmap scan but you left your pc at home? What if a golden opportunity shows during a pentest but you were walking around the building, taking a break? But leaving your phone at home or in the office when you go out is absurd, I mean, everyone b ...more
Welcome back, my fledgling hackers! Awhile back, I demonstrated one of my favorite little tools, netcat, which enables us to create a connection between any two machines and transfer files or spawn a command shell for "owning" the system. Despite the beauty and elegance of th ...more