This month, Iowa issued their first hepatitis C virus epidemiological profile and the news was not good. The number of cases of hepatitis C reported in Iowa between 2000 and 2015 rose nearly threefold, from 754 cases in 2000 to 2,235 cases in 2015. The news gets even worse wh ...more
You can get eggs and high-quality compost from backyard chickens—but you can also get Salmonella. Urban dwellers are increasingly taking a page from rural communities by keeping backyard chickens. Part of a grassroots sustainability movement, more people are discovering the b ...more
HIV-infected people who are treated long-term with antiviral drugs may have no detectable virus in their body, but scientists know there are pools of the virus hiding there, awaiting the chance to emerge and wreak havoc again. Since scientists discovered these latent pools, th ...more
New "radar road signature" technology from Bosch will be used to create maps for high-accuracy self driving. The new map is the first to use radar signals for a localization layer. Bosch's radar sensors have a detection range of up to 250 meters, compared to a maximum video r ...more
This is a video walkthrough of the "Prologue: Financial District" level in Mirror's Edge for the Xbox 360. The game has a realistic, brightly-colored style and differs from most other first-person perspective video games in allowing for a wider range of actions—such as slidin ...more
In most cases, gravity may as well not exist in Minecraft. The blocks all stick together in unreal ways, and you can even make things that just float in the sky. However, there are four exceptions to that rule: sand, gravel, water, and lava. All four of them obey the laws of ...more
The female mosquito feeds on blood so she can develop eggs, but in the process she can transmit disease. This video gives tips on how to avoid mosquito bites like avoid going out at dusk, application of repellent, wearing long sleeves and more. Avoid mosquito bites. Click thro ...more
Mononucleosis, an infection caused by the Epstein-Barr virus, can strike anyone, but those who experience the worst symptoms are teenagers. Follow these simple steps to avoid getting this virus. You Will Need * To avoid kissing * Clean hands * Your own utensils Step 1 Avoid k ...more
Though most warts disappear eventually without treatment, it's still useful to know how to prevent these unsightly marks from ever popping up. Watch this video to learn how to reduce your chances of warts. You Will Need * An understanding of wart transmission Step 1. Learn ...more
Even as health authorities describe the symptoms of Zika infection in the general population as mild, a new surveillance study finds serious side effects are more common, and serious, than previously thought. The Centers for Disease Control and Prevention (CDC) notes that man ...more
Gaming immerses you in environments. To get the most out of the gaming experience, you want the most immersive experience possible. That starts with great audio. You want to hear every footstep, detect the closest explosion, and hear your teammate calling out as you travel th ...more
By John Timmer, Ars Technica How much information can the world transmit, process, and store? Estimating this sort of thing can be a nightmare, but the task can provide valuable information on trends that are changing our computing and broadcast infrastructure. So a pair of r ...more
As a part of the already crowded field of diseases transmitted by ticks, you may not know the disease babesiosis, a dangerous infection caused by a parasite that infiltrates blood cells. While babesiosis may sound new to you, scholars believe it is the misfortune described in ...more
What if you forgot your car keys and that keyless entry remote banded to them, how are you going to get in your car? Well, if you haven't forgotten your cell phone, too, you can call up someone who has access to that keyless remote, so you can unlock your car or truck via the ...more
Welcome back, my novice hackers! This new series on Bluetooth hacking was inspired by a recent episode of Mr. Robot (my favorite TV show). In episode 6, Eliot hacked the bluetooth keyboard of the police office in order to hack the prison and release his nemesis, Vera. This is ...more
Spoofed phone calls originate from one source that's disguising its phone number as a different one, and you probably get these calls all the time. Maybe they're numbers from your local area code or for prominent businesses, but the callers are just hijacking those digits to f ...more
Wouldn't it be nice to just sit at your buddy's house, plug into his network, and see exactly what he's doing? What if it was as easy as that? What makes packet sniffers like Wireshark such potent tools is that a majority of local area networks (LANs) are based on the shared E ...more
Android comprises an entire ecosystem of apps, games, functions, and features, so it would only make sense that it has its own lexicon. Words, phrases, and acronyms that didn't exist ten years ago are now used in an off-the-cuff style by developers and support technicians acro ...more
Televisions used to be great for just one thing—watching TV. But a more connected world brought with it Smart TVs, devices that can access the web, stream Netflix, and even mirror your smartphone's display. And with this level of connectivity, OEMs like Samsung saw it fit to p ...more
Lack of appetite often signals a cold or flu. Eating can be the last thing we want to do when we have a sore throat or are too fatigued or achy to even get out of bed. When hungry, we don't feel as strong as when we are well fed—and we more than likely aren't as strong. The s ...more
A powered-off Windows 10 laptop can be compromised in less than three minutes. With just a few keystrokes, it's possible for a hacker to remove all antivirus software, create a backdoor, and capture webcam images and passwords, among other highly sensitive personal data. The ...more
RouterSploit is a powerful exploit framework similar to Metasploit, working to quickly identify and exploit common vulnerabilities in routers. And guess what. It can be run on most Android devices. I initially covered RouterSploit on Kali Linux and macOS (OS X), but this tuto ...more
After finding and monitoring nearby wireless access points and devices connected to them, hackers can use this information to bypass some types of security, like the kind used for Wi-Fi hotspots in coffee shops, hotels, and in flights high above the ground. By swapping their M ...more
Welcome back, my budding hackers! With this article, I am initiating a new series that so many of you have been asking for: Hacking Web Applications. In previous tutorials, we have touched on some of the techniques and tools for web app hacking. We looked at web app vulnerab ...more
RFID chips are everywhere. They're in passports, credit cards, and tons of items you've bought in the last 5 years or so. Big retailers like Walmart started using tracking products with RFID as early as 2004, and today, they're used in everything from mobile payments to hospit ...more
Hackers often find fascinating files in the most ordinary of places, one of those being FTP servers. Sometimes, luck will prevail, and anonymous logins will be enabled, meaning anyone can just log in. But more often than not, a valid username and password will be required. But ...more
If you have a modern iPhone, you have an excellent video recorder at your disposal. Every iPhone since the 6S has the ability to shoot in 4K resolution, and each new iteration has brought new capabilities to the table. But even the best mobile shooter can use a little extra he ...more
In five short years, three generations of ultra-low-cost Raspberry Pi devices have challenged the boundaries of what a person can do with a $35 computer — especially with Kali Linux. With each Pi more powerful and cheaper than the last, the addition of the Pi Zero in 2015 too ...more
Record stealthily, in the dark. This hack is simple and will turn any LED flashlight into an infrared night vision light you can use with any video camera. Infrared light is invisible to the human eye, but it will illuminate any area you are shooting. IR radiation is electrom ...more
Smartphones and laptops are constantly sending Wi-Fi radio signals, and many of these signals can be used to track us. In this guide, we'll program a cheap IoT device in Arduino to create hundreds of fake networks with common names; This will cause nearby devices to reveal the ...more
Still have an old tape deck installed in your car? This nifty hack lets you upgrade to the digital age without sacrificing your love for cassettes. There's nothing wrong with some low-fidelity tunes in your car every now and then, but if you want to listen to the tunes on your ...more
In the first part of this series, we learned about darknets, as well as how they came about. But these patches of forgotten Internet are not the oasis of free information you might think. Despite being hidden—or just harder to come across—these networks are no more safe then a ...more
Samy Kamkar, security researcher and friend of WonderHowTo, just had one of his devices featured in Mr. Robot. If you've never heard of Samy, you've at least probably heard of one of his hacks. For instance, the Samy computer worm that hacked MySpace, his compressed air trick ...more
Wi-Fi devices are continually emitting "probe frames," calling out for nearby Wi-Fi networks to connect to. Beyond being a privacy risk, probe frames can also be used to track or take over the data connection of nearby devices. We'll explain how to see nearby devices emitting ...more
All fields of study have their own language. For people interested in learning about microbes, the language can sometimes be downright difficult — but it doesn't need to be. From antibiotics to xerophiles, we have you covered in an easy-to-understand glossary. Terms are liste ...more
Auditing websites and discovering vulnerabilities can be a challenge. With RapidScan and UserLAnd combined, anyone with an unrooted Android phone can start hacking websites with a few simple commands. RapidScan does an excellent job of automating the deployment of vulnerabili ...more
Using a keylogger to intercept keys pressed on an infected computer can circumvent encryption used by email and secure chat clients. The collected data can often reveal usernames, passwords, and potentially compromising and private information which hackers abuse for financial ...more
Apple's macOS operating system is just as vulnerable to attacks as any Windows 10 computer or Android smartphone. Hacker's can embed backdoors, evade antivirus with simple commands, and utilize USB flash drives to completely compromise a MacBook. In this always-updated guide, ...more
Step 1: What Exploit Development Is and Why Should I Be Interested on About This Topic An exploit is a piece of software, a chunk of data, or a sequence of commands that takes advantage of a bug or vulnerability in order to cause unintended or unanticipated behavior to occur ...more
Due to weaknesses in the way Wi-Fi works, it's extremely easy to disrupt most Wi-Fi networks using tools that forge deauthentication packets. The ease with which these common tools can jam networks is only matched by how simple they are to detect for anyone listening for them. ...more
Hashes containing login passwords are transmitted between Windows computers on local Wi-Fi networks. By intercepting and decrypting these hashes using Responder and John the Ripper, respectively, we can learn a target's login credentials which can be later used to gain physica ...more
The Windows 10 desktop and microphone can be livestreamed without using Remote Desktop Protocol (RDP) software and without opening any ports on the target computer. A hacker with low user privileges can monitor and exfiltrate a target's every move and private conversation in r ...more
Passwords on Windows are stored as hashes, and sometimes they can be tough to crack. In certain situations, though, we can get around that by using the hash as is, with no need to know the plaintext password. It's especially interesting if we can manage to get the hash of an a ...more
Nmap is more powerful than you know. With a few scripts, we can extend its functionality beyond a simple port scanner and start to identify details about target servers sysadmins don't want us to know. Possibly the most popular and well-known reconnaissance tool currently ava ...more
Wish your home wireless network was faster? You can always buy a signal booster, but if you'd rather not spend the money, here are a few tips and tricks to speed up your wireless connection, including how to make a homemade signal booster with things you probably already have ...more
The herpes simplex virus (HSV) can cause devastating complications for infected newborns whose mothers have genital herpes. Understanding risk and research can help you, and your baby, when the time comes. In the US, about one out of six people aged 14 to 49 have genital herp ...more
Here at Null Byte, we've spoken a lot about securing and anonymizing traffic. This is a big deal. With all of today's business taking place electronically via computers, we need to be secure when on-the-go. A lot of businesses don't even train their employees to secure their c ...more
Using just a small sticky note, we can trigger a chain of events that ultimately results in complete access to someone's entire digital and personal life. Imagine arriving home one night after work and there's a Post-it note on your apartment door with the website "your-name- ...more
We have no control on the weather yet it is a part of our lives which influence what we do, what we eat, what we wear and many times where we live. How did people predict the weather before there was the Internet, television, radio or the weatherperson with all of their gadget ...more
Connecting to your headless Raspberry Pi on the go typically requires a network connection or carrying around bulky peripheral hardware like a screen and keyboard. With the help of an old-school connecting standard, though, you can log into your Pi from any computer using a si ...more
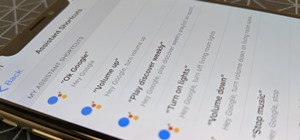
What started as an accessibility setting for hearing aids turned out to be a super helpful tool for anyone with a good set of Bluetooth headphones. The problem is that most iPhone and iPad users still don't know about it. If you're one of them, you need to see what this underr ...more
Apple has seemingly always made it a priority to show how much it cares about user security and privacy — enough that it has a page dedicated to it, proclaiming that "privacy is a fundamental human right." It's true that there are few issues more important than user privacy wh ...more
The latest Star Wars movie, Solo: A Star Wars Story, has grossed almost $350 million worldwide during its first month in theaters. This is a good opportunity to discuss how hackers can use media hype (in this case, Hollywood movie hype) to disarm an unsuspecting Windows user i ...more
Interested in transmitting and receiving files via Bluetooth on your Windows 7 computer (to download pictures from your phone, for example?). This clip will show you how it's done. It's simple! So simple, in fact, that this home-computing how-to can present a complete, step-by ...more
As Android bug bounty hunters and penetration testers, we need a properly configured environment to work in when testing exploits and looking for vulnerabilities. This could mean a virtual Android operating system or a dedicated network for capturing requests and performing ma ...more
With Gboard, Google created a keyboard with more functionality than just inputting words. The app includes features such as GIF search and live text translation, but it gets even better when you let it learn more about you. With this data, Gboard grows from a good keyboard to ...more
Google is an incredibly useful database of indexed websites, but querying Google doesn't search for what you type literally. The algorithms behind Google's searches can lead to a lot of irrelevant results. Still, with the right operators, we can be more exact while searching f ...more
What appears to be an ordinary MP4 may have been designed by an attacker to compromise your Linux Mint operating system. Opening the file will indeed play the intended video, but it will also silently create a connection to the attacker's system. Understanding the Attack Whi ...more
If you've wanted to get into Wi-Fi hacking, you might have noticed that it can be pretty challenging to find a safe and legal target to hack. But you can easily create your own test network using a single ESP8266-based microcontroller like the D1 Mini. Our goal is to crack a ...more
If you've ever wanted to track down the source of a Wi-Fi transmission, doing so can be relatively easy with the right equipment. Using a directional Wi-Fi antenna and Wireshark, we can create a display filter to target any device in range to plot the signal strength on a gra ...more