Yosemite is definitely an improvement over Mavericks, but there are still some painfully obvious and annoying bugs that occur within certain apps. One such example is the elongated "Open" and "Save" dialog boxes, which sometimes stretch all the way down so that the "Open," "S ...more
The Nexus 6 uses an Ambient Display notification system that was heavily inspired by the Active Display feature on the Moto X. Essentially, the device shows a black-and-white version of the lock screen whenever you receive a new notification or pick the phone up. This is all m ...more
One of the few areas where Android lags behind iOS is a comprehensive backup solution for apps. Root tools, such as the popular Titanium Backup, are capable of backing up all of your apps and their data, but not everyone wants to root their device and potentially run into issu ...more
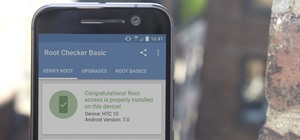
Google's latest Nexus device is big, bold, and beautiful—and now it's got root. Thanks to some quick work by legendary Android developer Chainfire, the Nexus 6 already had a clear-cut root method before most stores even had it in stock. CF Auto Root is a wonderful tool that h ...more
After lots of waiting and anticipation, the OnePlus One Android smartphone has been unveiled, and it's ready to take down the Nexus. Video: . This CyanogenMod based device comes in with high-end features and a killer price point, and is set to go on sale in May. The OnePlus O ...more
NSA aside, Apple makes it difficult for users to extract and download text messages from their iPhones onto a computer. For whatever reason (legal, devious, neurotic, etc), we've all found a time where we'd like to save backups of certain meaningful, important, or perhaps incr ...more
Nearly two years ago, Peter Chou, CEO of HTC, confirmed that the company would no longer be locking bootloaders. Whether or not they've actually lived up to this claim is debatable. Any phone bought from a wireless carrier comes locked. Only the new HTC One Developer Edition s ...more
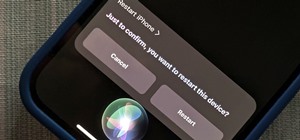
Siri can perform many actions for you on your iPhone, such as sending messages, providing information, getting directions, looking up a contact, and playing music. Still, there are even more important Siri voice commands that every iPhone owner should know — even the ones who ...more
When we think about operating systems, we tend to view them from the perspective of a user. After all, most of us have spent a substantial amount of time on our computers, and so we've become more than acquainted with the ins and outs of whatever system we have running on our ...more
Google switched to gestural navigation in Android 9, and in removing the back/home/recents buttons, they were able to greatly reduce the size of the navigation bar at the bottom of the screen. However, there's still a white line, aka "The Pill," taking up space to show you whe ...more
For enterprise augmented reality platform makers, remote assistance apps represent one of the greatest opportunities to show off the power of immersive computing. These apps enable experts to guide front-line workers or customers with AR prompts and other content in the field ...more
Password cracking is a specialty of some hackers, and it's often thought that raw computing power trumps everything else. That is true in some cases, but sometimes it's more about the wordlist. Making a custom, targeted wordlist can cut down cracking time considerably, and Wor ...more
Lover it or hate it, Android 10 is a big improvement over Android 9 Pie. Based on previous versions, most flagships released in the last two years will get Android 10, but the question is when. So while you wait for those cool new gestures, how about I show you an app that giv ...more
Another year, another battle between Samsung and Apple. We recently saw what Samsung is bringing to the table this year with the release of the Galaxy Note 10+, and now it's Apple's turn. For those who want a truly large device, Apple is offering the iPhone 11 Pro Max. Let's s ...more
Samsung decided to shake things up this year. In the past, the Galaxy Note series was one large phone. This year, it's two phones: the Galaxy Note 10 and Note 10+. So for the first time in a long time, we can compare the latest standard iPhone, the 11 Pro, to a Galaxy Note dev ...more
Despite newer phones having larger batteries, after a few months, my battery life drops significantly. I started researching solutions after my third phone. No matter who I asked, the most recommended solution was always Greenify. And unlike other solutions, you don't need roo ...more
The hugely successful S10 series of flagships may be a tough act to follow, but Samsung has proven that it's up to the task with the Galaxy Note 10. The latest phablet bearing the Note name is the first of its line to come with an even larger variant, and boasts an eye-pleasin ...more
Apple CEO Tim Cook has said that augmented reality (or, AR for short) will "change everything." But what, exactly, is augmented reality? Generally, augmented reality refers to the process of presenting virtual objects and imagery — usually through a wearable lens or external ...more
You can easily deck out your favorite phone with great wallpapers, ringtones, and icons, but what about fonts? Not all Android skins let you change the system font, and even when they do, the options are often limited to a few choices. Certain root apps can open up the system ...more
The first few minutes after gaining access to a MacBook are critical — but where do we begin? Using tools built into macOS, we can develop an in-depth understanding of running background processes, detect antivirus software, locate sensitive files, and fingerprint other device ...more
After backdooring a MacBook not protected by FileVault or using a fake PDF to gain remote access, an attacker may wish to upgrade their Netcat shell to something more fully featured. While a root shell allows attackers to remotely modify most files on the MacBook, Empire featu ...more
Spotify is one of the most popular music streaming services available and allows you a high degree of control over the way you experience your music. Included in that is the album art for your playlists. While not an option ingrained in the mobile app itself, changing a playli ...more
One of the biggest improvements with the Galaxy S9 and S9+ is the redesigned camera, with the latter scoring an impressive 99 overall on DxOMark. But with an abundance of features and enhancements, tweaking the camera's settings for optimal performance can be a little confusin ...more
The latest and greatest in Qualcomm's long line of mobile processors, the Snapdragon 845, is now set to touch down along with the Galaxy S9 and S9+. And as gorgeous as Samsung's newest flagships are, the processor that powers them under the hood is just as highly anticipated. ...more
The world around us keeps getting smarter. Not only do we have advanced AI services like the Google Assistant, but now we've got the Internet of Things connecting physical objects to the digital world. It's amazing when you think about it, but the real sci-fi stuff starts to h ...more
Keystroke injection attacks are popular because they exploit the trust computers have in human interface devices (HIDs). One of the most popular and easily accessible keystroke injection tools is the USB Rubber Ducky from Hack5, which has a huge range of uses beyond simple HID ...more
Very often we have processes in Linux that we want to always run in the background at startup. These would be processes that we need to start at bootup and always be available to us. If we are running a Linux distribution with a GUI (graphical user interface) like Kali or Ubu ...more
For many people, the two main advantages of buying a Nexus device are prompt updates and the ability to root without much hassle. But in a cruel twist of fate, these two features are almost mutually exclusive, since OTA updates will refuse to run on rooted devices. In the pas ...more
If you're experiencing issues with an app or custom ROM and would like to report your problem to the developer, there's no better way to do it than by capturing a logcat. Android keeps track of all the commands that have been executed by various apps and services, which means ...more
If you're completely new to Android, you're in for a treat with all of the software tweaks and customization options that your smartphone or tablet offers out of the box. But if you really want to take things to the next level, the ability to mod your device expands exponentia ...more
Have you ever used an open wifi, which after you connect displays a website to enter your credentials to get internet? That website is called captive portal and widely used in airports, hotels, universities etc. Have you ever wondered what would happen if someone would set up ...more
Welcome back, my greenhorn hackers! Throughout this series on Metasploit, and in most of my hacking tutorials here on Null Byte that use Metasploit (there are many; type "metasploit" into the search bar and you will find dozens), I have focused primarily on just two types of ...more
Not too long ago, Sony was looking to create a method for theming the interface of their Xperia smartphones and came up with a framework called Runtime Resource Overlay (RRO). They then contributed this framework to Android's main code base, and Google has since taken over the ...more
As Android's de facto virtual assistant, Google Now lets us speak directly to our phones in plain English to answer our questions and perform many basic tasks. With the app open, just say "Okay Google," then wait for the beep, and ask almost any question. But several Google N ...more
Hi all, Pro Hackers/Crackers, Let's see how we can use batch for our own Protection instead of exploiting someone with it. And this tutorial is going to explain the same. #1 Protection, PC Security: I will tell you how to add another level of security to your PC, instead of j ...more
Welcome back, my aspiring hackers! Those of you who use Windows in a LAN environment understand that Windows machines can share directories, files, printers, etc. using "shares." This protocol dates back to the 1980s when the then dominant computer firm, IBM, developed a way ...more
Google has already started to roll out the over-the-air update of Android 5.0 Lollipop to older Nexus series phones and tablets, but chances are it will take a long time for the OTA to hit your device. If you don't want to wait, you can manually install Lollipop right now if ...more
Welcome back, my aspiring hackers! Many of you have installed Kali Linux as a virtual machine (VM) using VMware or VirtualBox, while others have installed Kali (or BackTrack) in a dual-boot system. The drawback to installing these hacking systems as a VM is that it then requi ...more
I'm all about saving time. If there's a quicker way to do something, I'm going to find it. For this reason, whenever I need to search through old emails or compose new ones in Gmail, I do it directly from Chrome's address bar, or as Google likes to call it, the omnibox—and you ...more
When it's most important for me to browse the web incognito, I always seem to forget to enable private browsing. If that sounds like you, it's time you stop making that mistake for good. Manually deleting the cache and browser history is a thing of the past, and as it turns ou ...more
This year's I/O was all about bringing Android into the future and onto new devices. On top of announcing the upcoming "L" release of its mobile OS, Google showcased Android Wear, Android Auto, and Android TV. With a unified design language and notification mirroring, the var ...more
The Nexus line of devices consistently offer the most bang for your buck. It's why many of us purchased a Nexus 5—at a $350 entry price, it's half the cost of any other phone with similar specs. Google manages to sell these devices at that insanely low price point by cutting ...more
The beauty of having a Google Play Edition HTC One is the ability to get as close to stock Android as possible while still getting some extra non-Google, proprietary HTC features. The newest version of Android, 4.4.3, has just hit the Nexus and Google Play Edition line of phon ...more
Recently, Sprint announced a partnership with Harman Kardon to deliver exclusive sound FX technology to their variant of the HTC One M8. The joint effort between the two companies is both to entice customers to switch to Sprint as well as improve the overall audio quality comi ...more
Welcome back, my hacker novitiates! Recently, I demonstrated a hack where you could redirect traffic intended for one site, such as bankofamerica.com, to your fake website. Of course, to really make this work, you would need to make a replica of the site you were spoofing, or ...more
Welcome back, my budding hackers! I've written several listener guides on creating a malicious PDF or malicious Word document that would carry in it a payload with the Meterpreter, or reverse shell enabling you to own the system. One of the hurdles to using these techniques i ...more
Welcome back, my hacker apprentices! In recent weeks, the revelation that the NSA has been spying on all of us has many people up in arms. I guess I take it all in stride as I just assume that the NSA is spying on all of us—all of the time. Don't get me wrong, I don't condone ...more
In this article, I'll be continuing my series on microcontrollers. If you haven't read part one, I'd recommend heading over there and reading it! So How Does Arduino Think? Arduino is programmed with ones and zeros, but hopefully that's not how we programmers have to write t ...more
After a two-month delay, Apple has finally released iTunes 11, which was initially slated to be released alongside iOS 6. Video: . The new highly revamped music player is a substantial upgrade from the old version, but that isn't really saying much; iTunes has never really had ...more
The biggest hurdle to rooting is that it usually requires a computer. Things get complicated when you're trying to use a desktop operating system to exploit a mobile OS, and the connection isn't always reliable. But with the help of Magisk, you can now use one Android phone to ...more
Twitter's official iOS app is adequate if you're not much of a tweeter, but if you are, there's a lot of useful features that are missing. Luckily, there are plenty of free Twitter clients available that you can use on your iPhone. These third-party apps have features such as ...more
Smartphones and laptops are constantly sending Wi-Fi radio signals, and many of these signals can be used to track us. In this guide, we'll program a cheap IoT device in Arduino to create hundreds of fake networks with common names; This will cause nearby devices to reveal the ...more
If you can't always see what you're typing very well on your iPhone, iPad, or Mac, you no longer have to adjust the font size for the app or entire system just to read your writing more easily. One of Apple's newer Accessibility features gives you a customizable, magnified vie ...more
The Camera app on your iPhone includes new features with the iOS 17 update that will help you take better photos and more impressive videos, but there are a lot of cool new things available that you might not see right away. Many of Camera's new features are exclusive to the ...more
With the arrival of Facebook Ray-Ban Stories smartglasses commanding the recent spotlight, the tech world acted like it forgot about Facebook's first foray in consumer hardware — the Portal line of video calling devices. Well, this is how Facebook reminds you about Portal, wi ...more
You know the drill: After booting up your iPhone, you need to swipe up or press the Home button, then punch in the passcode to unlock Face ID or Touch ID. It's the way things have always been — but it doesn't have to be. Instead, you can unlock your iPhone using just your voic ...more
The art of fuzzing is a vital skill for any penetration tester or hacker to possess. The faster you fuzz, and the more efficiently you are at doing it, the closer you come to achieving your goal, whether that means finding a valid bug or discovering an initial attack vector. A ...more
PirateBox is a great way to communicate with others nearby when cellular and Wi-Fi networks aren't available. With it, you can anonymously share any kind of media or document and even talk to one another by voice — without being online. However, it needs a Raspberry Pi, which ...more
TWRP is the premiere custom recovery for Android because of how many devices it supports and how simple it is to use. But installing it in the first place hasn't always been the easiest thing to do — until now. With the help of a Magisk module, you can finally use one Android ...more
If you've ever wanted to track down the source of a Wi-Fi transmission, doing so can be relatively easy with the right equipment. Using a directional Wi-Fi antenna and Wireshark, we can create a display filter to target any device in range to plot the signal strength on a gra ...more