Fasting—or the practice of regularly abstaining from ingesting anything except water—is a pretty drastic move. I tried to fast for two days and made it to the 12-hour mark, which is when I broke down and ate a quart of ice cream. However, I may have to try it again, since "sh ...more
Unwanted advertising is everywhere. Annoying pop-up ads, overly loud late night commercials, spam...it never ends. And before spam, there was junk mail. Junk mail is even worse because unlike TV commercials and internet ads, it's physical. You can't just delete or ignore it—an ...more
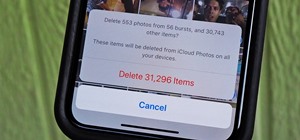
You may have recently seen a plethora of Instagram users, including celebrities and politicians, sharing a screenshot declaring that the platform will implement a new "rule" where it would own and could use your photos and videos however it wishes. The screenshots are part of ...more
Featured on MTV's Catfish TV series, in season 7, episode 8, Grabify is a tracking link generator that makes it easy to catch an online catfish in a lie. With the ability to identify the IP address, location, make, and model of any device that opens on a cleverly disguised tra ...more
Most companies have services like employee login portals, internal-only subdomains, and test servers they would prefer to keep private. Red teams and white hat hackers can find these obscure and often vulnerable services using a tool designed to help protect users from fraudul ...more
A router is the core of anyone's internet experience, but most people don't spend much time setting up this critical piece of hardware. Old firmware, default passwords, and other configuration issues continue to haunt many organizations. Exploiting the poor, neglected computer ...more
Walsh, a new community under construction on 7,200 acres of former ranch land near Fort Worth, Texas, will one day contain 15,000 homes. To sell prospective home buyers on the development before it is fully built, Republic Property Group is leaning on technology. A high-spee ...more
Android has several features built into the platform that improve user experience but require extra attention to prevent a security breach. By modifying these settings, you can drastically reduce the possibility of someone exploiting your device or intercepting information. B ...more
YouTube's massive user base comprises almost one third of all people on the internet, and collectively, users spend well over 100 million hours on the site watching billions of videos each day. Add it all up, and this means that YouTube is viewed by more people than any U.S. c ...more
There are over 1.6 million apps on the Google Play Store, which makes it the largest collection of mobile apps on the planet. However, a large portion of this total is occupied by apps with overlapping functions—think social media, news, weather, music players, and various oth ...more
Remember portable MP3 players like the classic iPod? Seems like forever ago that they were all the rage, and I don't think I've seen a real one in the wild for a good 5 years now. These devices died out so quickly as a direct result of the onset of smartphones, which allow us ...more
It's been a while when the major web browsers first introduced HTTP Strict Transport Security, which made it more difficult to carry Man In The Middle (MITM) attacks (except IE, as always, which will support HSTS since Windows 10, surprised?). SSLStrip and the HSTS Chronicles ...more
Hi everyone. Recently I've been studying some topics about Assembly, memory and exploitation, and thought I could write something nice, easy and fast about it, just because I like to share what I learn, and probably sharing what you learn and trying to explain it to a strange ...more
If you're marginally inclined towards computers, you've probably been approached at some point by a family member who wants you to "fix" their system during a visit home. With the holidays coming up, these opportunities (or ambushes) are even more likely. Even if nothing is w ...more
If I were to lose access to the entire internet for the rest of my life, one of the websites I would miss the most would have to be Wikipedia. Wikipedia has ended countless arguments, informed me of how old and single some of my favorite actresses are, and helped me brush up o ...more
Let's say that you've got the look down, and you have your Steampunk props all ready to go. Congratulations! You're a Steampunk! But now what do you do with yourself? You can sit there, patting yourself on the back, but that gets lonely after awhile. Your props will look nic ...more
Web application firewalls are one of the strongest defenses a web app has, but they can be vulnerable if the firewall version used is known to an attacker. Understanding which firewall a target is using can be the first step to a hacker discovering how to get past it — and wha ...more
Businesses leave paper trails for nearly every activity they do, making it easy for a hacker or researcher to dig up everything from business licenses to a CEO's signature if they know where to look. To do this, we'll dig into the databases of government organizations and priv ...more
Google is an incredibly useful database of indexed websites, but querying Google doesn't search for what you type literally. The algorithms behind Google's searches can lead to a lot of irrelevant results. Still, with the right operators, we can be more exact while searching f ...more
Reconnaissance is one of the most important and often the most time consuming, part of planning an attack against a target. Thanks to a pair of recon tools coded in Python, it takes just seconds to research how a website or server might be vulnerable. No matter what platform ...more
Phone numbers often contain clues to the owner's identity and can bring up a lot of data during an OSINT investigation. Starting with a phone number, we can search through a large number of online databases with only a few clicks to discover information about a phone number. I ...more
Just days before the release of the first image of the Magic Leap device, the company's CEO, Rony Abovitz, knew that the biggest moment of his life was about to unfold the following week. But instead of hunkering down in the Florida-based confines of the company's skunkworks, ...more
Some of us woke up at the KRACK of dawn to begin reading about the latest serious vulnerability that impacts the vast majority of users on Wi-Fi. If you weren't one of those early readers, I'm talking about the Key Reinstallation Attack, which affects nearly all Wi-Fi devices. ...more
The Operative Framework is a powerful Python-based open-source intelligence (OSINT) tool that can be used to find domains registered by the same email address, as well as many other investigative functions. This reconnaissance tool provides insight about your target through ex ...more
There is an Indian story called the Legend of Paal Paysam, and while it doesn't seem like it at first, it has a lot to say about what motivated Paul Travers in the augmented reality space. The story is about a king that loved chess and the sage that he challenged. To motivate ...more
While its direct-selling model echoes brands like Avon and Tupperware, Indonesia's MindStores gives the approach a modern twist—with augmented reality. Recognized as the first partnership store network to use augmented and virtual reality, MindStores equips its store owners w ...more
The internet was blowing up recently over this mind-blowing, mouth-watering video of a woman making a cake decoration out of… wait for it… chocolate bubble wrap. Yes, that's right: she turned the ubiquitous packing material into the mold for an absolutely gorgeous cake embelli ...more
Have you ever used an open wifi, which after you connect displays a website to enter your credentials to get internet? That website is called captive portal and widely used in airports, hotels, universities etc. Have you ever wondered what would happen if someone would set up ...more
With the countless daytime talk shows starring and featuring doctors, nurses, and other medical specialists, discovering new ways to live a healthy life is just a remote click away. Although their shows might draw you in with incredible facts and mind-blowing secrets to weight ...more
We all know that it's important to drink water regularly throughout the day. After all, it has so many benefits, including flushing toxins out of the body and maintaining kidney health and good bowel movements. Turns out that's only part of the story. While being properly hydr ...more
The point of ice in your cocktail is to make it cold, right? Yes and no. Obviously, ice does lower the temperature of your cocktail, but it also does other things: enhances certain flavors while masking others (handy if you're drinking less than stellar booze or wine). As Sim ...more
Brands are increasingly adopting augmented reality to promote their products and services, and they have multiple paths for bringing AR experience to their audiences. To promote its stage production, the Harry Potter franchise turned to Facebook to pull together an AR experie ...more
Smartphones are inherently bad for privacy. You've basically got a tracking device in your pocket, pinging off cell towers and locking onto GPS satellites. All the while, tracking cookies, advertising IDs, and usage stats follow you around the internet. So no, there's no such ...more
Compromised uTorrent clients can be abused to download a malicious torrent file. The malicious file is designed to embed a persistent backdoor and execute when Windows 10 reboots, granting the attacker remote access to the operating system at will. Torrent clients like uTorre ...more
You don't have to be a frequent flyer to know how indispensable navigation apps have become. Many of us rely on these apps for traveling from state to state and getting around in foreign cities, but even more of us count on these apps to beat rush hour traffic and find the qui ...more
You can mod every aspect of your phone's software with root, but if you want to make changes at the hardware level, you'll need a custom kernel. If you've looked into custom kernels before, one name undoubtedly kept coming up: ElementalX. It's easily the best custom kernel out ...more
Samsung isn't known for its timely rollout of major Android updates, and Android 9.0 Pie won't be an exception. If we go by their Oreo update timeline, we can expect Android Pie to officially touch down for the Galaxy S9 and S9+ sometime around November, with the final version ...more
In the previous article, we learned how to set up our VPS, configure our PHP server, and developed an in-depth understanding of how the payload works. With all that taken care of, we can get into disguising our payload to appear as an image and crafting the note in the greetin ...more
In a previous article, we learned how to take advantage of a feature, Dynamic Data Exchange (DDE), to run malicious code when a Microsoft Word document is opened. The biggest challenge of this attack is that it requires getting the user to agree to a pop-up prompt. Fortunately ...more
If you need to scan a large number of domains for a specific web app vulnerability, Dorkbot may be the tool for you. Dorkbot uses search engines to locate dorks and then scan potentially vulnerable apps with a scanner module. This tool is useful if you're managing a large num ...more
Open-source data scraping is an essential reconnaissance tool for government agencies and hackers alike, with big data turning our digital fingerprints into giant neon signs. The problem is no longer whether the right data exists, it's filtering it down to the exact answer you ...more
While the world is only recently becoming aware of its existence, augmented reality has been around in some form or another since the '90s. In the last decade, with the advancement and miniaturization of computer technology — specifically smartphones and tablets — AR has becom ...more
In the past, to see a pre-constructed state of the house that you would one day live in, you had to be able to read blueprints or hire an artist to sketch it out. Later came the ability to have a 3D rendering of that house on a screen, but you'd still have to work hard to envi ...more
If you have a HoloLens, you can now control the lighting throughout your home or office via holographic controls using the free Hue Lights app in the Windows Store. The app, made by California-based AfterNow, works with the Philips Hue colored lighting system and is much more ...more
It's that time of the year, y'all—when the air becomes crisp, the nights grow long, and people crave hearty, warm soups and stews. And of all the season's offerings, my hands-down favorite has to be chili: It's versatile, meaty, and above all else, it's damn easy to make. (Tha ...more
I've been an Android user almost as long as the operating system has existed, so when I received my first iPhone in April, I felt like I was in a foreign land. Sure, it runs most of the apps I'm used to, and the phone itself feels about the same in my hand as any similarly-siz ...more
If you don't want to dress up as a vampire, witch, werewolf, or zombie again this Halloween, step things up a notch and go viral. There have been a ton of funny memes and absurd news since last October, so the only hard part is settling on the right one for inspiration for you ...more
These days, that pocket-sized computer we call a smartphone is home to your entire digital life. But with the onset of mobile payments and online banking, the line between your virtual world and the physical realm is becoming increasingly blurred. We vigilantly remember to lo ...more
Unless you're vegan or lactose intolerant, butter is an indispensible ingredient. However, butter is no one-trick pony. It can take many forms that make it even more versatile and useful in the kitchen. Clarified butter has many advantages over regular butter—but there are cer ...more
If you've read any health news in the past year or so, you've probably been bombarded with headlines announcing that frequent sitters face certain death, even when you're just relaxing and watching TV at home. From increased health risks and added laziness, sitting is becomin ...more
It has been a long while since I last came here to write an article. Graduate school keeps you busy. After I looked over what I had written previously, I decided that I should introduce another fun topic from cryptography. In this case, steganography. In this article, I will ...more
I obviously do a lot of Steampunk projects, but there are a ton of things out there that I haven't tried yet. So, in an effort to broaden my horizons, I recently taught myself how to use Arduinos, which I plan to incorporate into some of my future Steampunk builds. Since ther ...more
If you're living or staying out in the middle of nowhere or a rural area outside of a big city or town — where there are no reliable cable, fiber, or wireless networks available — how can you get an internet connection? There are several possibilities, but they all come with t ...more
When it comes to cybersecurity, one layer isn't enough. A complex password (or one created with a password manager) does a good job of protecting your data, but it can still be cracked. Two-factor authentication strengthens this by adding a second layer of security, giving you ...more
People fundamentally distrust magicians. And they should. The illusions they proffer are just that, illusions meant to astound rather than tangible interactions and results that have weight and meaning in our real world. Our lizard brains know this, and, no matter what the out ...more
Phones these days are expensive. The iPhone 11 Pro is presumed to start at $999, following the iPhone XS and iPhone X's leads. One way to bring down that cost is to trade in your old iPhone, but there isn't one clear-cut way to do that. You could trade your iPhone into a parti ...more
Planning a vacation overseas can sometimes feel overwhelming with the number of things you need to remember before heading out. Since smartphones keep us connected at all times, it's essential that you have everything you need here as well. Unexpected events can arise while on ...more
There's a lot of misinformation about VPN services, and it stems from the fact that not all of them are created equal. Some focus on privacy, others on security, and a few VPNs are seemingly even purpose-built for the polar opposite: data collection. We made this guide to help ...more
The latest film addition in the American-produced Millennium series, The Girl in the Spider's Web, was just released on Blu-ray a few days ago. As you could expect, the movie has many hacking scenes throughout, just like the previous English and Swedish language movies centere ...more
For the uninitiated, it can be difficult to buy that special hacker in your life a perfect holiday gift. That's why we've taken out the guesswork and curated a list of the top 20 most popular items our readers are buying. Whether you're buying a gift for a friend or have been ...more