Features like themes and a tab queue make Firefox an extremely versatile mobile browser. Mozilla is constantly adding bonus functionality like this to Firefox, but a long-time staple is perhaps the most powerful feature: Extensions. This system gives you the ability to add fea ...more
Mozilla baked an easily missed feature into their Firefox Browser for Android called the "tab queue," which you should definitely be using if you find yourself opening links a lot from emails, texts, and other link-heavy apps. With tab queuing enabled, you can save links as ne ...more
Ad blocking on Android usually requires root access, but a pair of new browsers based on the open source Chromium and Firefox builds are looking to change this. Today, I'll be going over two options for ad-free web browsing without root access. The first is the Chromium-based ...more
The idea of remote assistant apps in augmented reality has been taking off in the last couple of years, but Epson is introducing a differing kind of solution for companies that may benefit from a more straightforward dynamic before going full-on immersive with higher-end AR re ...more
A hacker with privileged access to a Windows 10 computer can configure it to act as a web proxy, which allows the attacker to target devices and services on the network through the compromised computer. The probes and attacks appear to originate from the Windows 10 computer, m ...more
Ever since the GDPR was implemented, it seems every website on the internet needs to inform you of how its privacy policies have changed. If your web browsing experience has been marred by a constant barrage of these cookie pop-ups and privacy dialogs, you should know there's ...more
If you ever get asked to update your WhatsApp to your favorite color, don't. It's probably spam. According to Reddit user Yuexist, a new WhatsApp adware is going around disguised as an update. The spammer used non-ASCII characters rather than ASCII to look identical to its " ...more
The Drug Enforcement Agency (DEA) has been purchasing spyware from the Milan-based Hacking Team and its US subsidiary Cicom USA since 2012. Public records reveal invoices between Cicom USA and the DEA that have ranged between $22,000 to $575,000 from 2012 to 2015. Hacking Tea ...more
There are many reasons to keep adult websites off your iOS device. They can pop up accidentally at the least opportune moments, can give your device malware, and are not welcome in a kid-friendly home. Plus, there's a chance that your porn viewing habits could become public o ...more
A group ironically called the "Guardians of Peace" hacked into Sony Pictures' computer systems and released a mountain of internal information such as medical records, leaked scripts, work complaints, and even celebrity aliases. Why did this happen? Sure, a lot of well-though ...more
Social media is where we post our thoughts for the world to see, but sometimes a little more exclusivity is needed. And that's where Scrambls comes in. Scrambls if a free extension for Chrome, Firefox, Safari, and Internet Explorer that scrambles your messages for super cool ...more
Apple had its Worldwide Developers Conference on June 3, 2019, which showcased big software announcements for all of Apple's hardware, and anyone can watch the keynote as it happened. WWDC 2019's biggest attraction is iOS 13, which was rumored to include a real dark mode, an ...more
Users are often the weakest link when probing for vulnerabilities, and it's no surprise they can be easily fooled. One way to do this is called clickjacking. This type of attack tricks the victim into clicking something they didn't mean to click, something under the attacker's ...more
Apple's macOS operating system is just as vulnerable to attacks as any Windows 10 computer or Android smartphone. Hacker's can embed backdoors, evade antivirus with simple commands, and utilize USB flash drives to completely compromise a MacBook. In this always-updated guide, ...more
If you've ever wanted to download YouTube videos directly to your iPhone, there's an easy solution — just update to iOS 12 and install Apple's new Shortcuts app. With the Workflow-replacement app, you can add a shortcut that lets you download any YouTube video you want, withou ...more
Note-taking apps are a dime a dozen on the Play Store. However, due to their inability to sync across devices, many can't compete with Google Keep. Mozilla decided to throw their hat in the ring with Notes by Firefox, and unlike others, their notes app syncs easily with one of ...more
Passwords stored in web browsers like Google Chrome and Mozilla Firefox are a gold mine for hackers. An attacker with backdoor access to a compromised computer can easily dump and decrypt data stored in web browsers. So, you'll want to think twice before hitting "Save" next ti ...more
At the end of 2017, Mozilla introduced the world to Quantum. While desktop Firefox received all the improvements, Android users were stuck waiting for one of the biggest components to hit, which brought speed that surpassed Google Chrome. Well the wait is over, the new and imp ...more
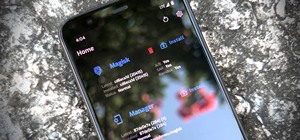
One unique feature of Firefox Mobile is extensions. Extensions allow users to add in features that didn't originally come with the browser. These add-ons provide an array of features, including improvement to privacy and security. There are a number of steps you can take to i ...more
There are over 3 million apps in the Google Play Store, all optimized for the small screen in your hands. While that number sounds staggering, there are still many online tools and websites that require you to use a mobile browser since app development is expensive. However, t ...more
Mozilla's Firefox has always been a highly praised internet browser. Since it's open-source, users know what they're getting without any secrecy. It's got plenty of features that are unmatched by any of its competitors on mobile. However, speed and performance have always been ...more
Sophisticated hackers have been exploiting vulnerabilities in Chrome and Firefox to trick even the most careful internet users into logging into fake domains for sites like Apple, Google, and Amazon. Typically, a careful internet user would always check the domain of any site ...more
If you want free Poké Balls and eggs when playing Pokémon GO, you can find them at PokéStops in variation locations around your city, which are marked with towering blue icons on your map. Once you're at Level 5, they'll also grant you Potions and Revives to help you in your b ...more
Macs are generally highly power efficient due to, in part, the optimized sleeping schedule with OS X. Yet in certain scenarios, you might not want your Mac to go to sleep: downloading a huge file, reading a book, reviewing a spreadsheet, analyzing some content on the screen... ...more
A year after making a splash at the annual Consumer Electronics Show in Las Vegas with Amazon Alexa integration, smartglasses maker Vuzix is bringing a notable weather app to its Blade smartglasses for the 2019 edition of the conference. Vuzix has announced that its Blade dev ...more
Apple revealed three new iPhone models on Wednesday, Sept. 12, at its "Gather Round" event in Cupertino, as well as announced the official release date of iOS 12, its newest mobile operating system. If you missed it and want to watch the full event, here's how to do it on your ...more
Facebook, parent company of Instagram, has allowed you to download photos and other account data for some time now, but the data request feature is also now available on Instagram to meet the GDPR data portability requirement in the EU — and it's available worldwide, not just ...more
No matter which smartphone you buy, it will come with an internet browser preinstalled. Depending on your OEM, the default browser might be called Samsung Internet, HTC Internet, Silk Browser by Amazon, ASUS Browser, or Google Chrome—there's just so many stock browsers availab ...more
Keyboard shortcuts can make using your Mac faster and easier, and leave your mouse feeling archaic. With just a few taps, you can save files, open new tabs, or play a movie—all without using your mouse even once. Don't Miss: 30+ Keyboard Shortcuts You Should Be Using on YouTu ...more
Without admin privileges, installing additional software, or modifying the Windows 10 firewall, an attacker can alter a router and perform a variety of exploits. It's accomplished by forwarding requests from Kali through a backdoored Windows computer to the router gateway with ...more
Information gathering is one of the most important steps in pentesting or hacking, and it can often be more rewarding to run things on the target itself as opposed to just running scripts against it remotely. With an SQL injection, a hacker can compromise a server and, ultimat ...more
Passwords and data stored in web browsers are extremely valuable to hackers. If not for financial gain, black hat hackers may still leak your passwords and personal information for amusement. Never undervalue what you're worth to a hacker. While I'm definitely no black hat, d ...more
Unlike many browsers, Firefox gives a lot of control to the user. By default, Firefox does a great job of balancing security and performance. However, within the app's settings, you can modify options to shift this balance in one direction or another. For those looking to shif ...more
As one of the most powerful Android apps for connecting your phone or tablet to your other devices in various ways, Pushbullet had always been a fan—and Gadget Hacks—favorite. However, ever since late last year, many of the app's popular and once-free features now require a c ...more
Compromised uTorrent clients can be abused to download a malicious torrent file. The malicious file is designed to embed a persistent backdoor and execute when Windows 10 reboots, granting the attacker remote access to the operating system at will. Torrent clients like uTorre ...more
With any password manager, the only password you need to remember is the master password that locks the vault from both hackers and the company. This makes the master password very important. But what happens if you forget this password? Well, LastPass has you covered. It isn ...more
Not all threats to our privacy come from hackers thousands of miles away. Often, we just want to keep our data safe from those around us, who may snoop in our phones or demand we reveal our secrets. That's where BlackBerry Locker comes in. Starting with the BlackBerry KEYone, ...more
Single sign-on (SSO) lets users login across different sites without having to manage multiple accounts. I'm sure most of us appreciate the convenience of seeing "Sign in with …" buttons that let us login with a single username. Hackers, however, see a possible avenue for expl ...more
Bookmarks and favorites are handy options for saving interesting websites you come across while surfing the web on Android but are far from ideal when it comes to instant access. Thankfully, Google Chrome gives you the added ability to save webpages and progressive web apps di ...more
When OnePlus announced the 5T, many were disappointed that it wasn't shipping with Android Oreo. To curb some of this disappointment, OnePlus quickly introduced an open beta for both the 5 and 5T and promised that each would receive the official version by Q1 2018. Well today, ...more
Safari for iPhone is generally a good mobile browsing experience — except when it isn't. Popup ads are a real issue, and they cause both great annoyance as well as concern over iOS security. How do you stop these nuisances and return to a web without fear of popups? Through a ...more
After numerous scandals like the Equifax data breach and the 2016 US election, cybersecurity has become a significant issue for Americans. Unfortunately, anytime we use our devices, we're open to a cyber attack — especially when we browse the web. However, there are ways that ...more
Although they're often times the primary source of income for websites, on-site advertisements can annoy even the most tolerable reader. That's why ad blockers have been some of the most popular downloads on Firefox and Chrome for some time now, demonstrating that when it come ...more
One of the first orders of business after purchasing a new smartphone is to load up your shiny new toy with phone numbers, email addresses, and general contact information for all the important people in your life. Don't Miss: Android Basics: Get Started with Your New Smartph ...more
Out of the box, Windows 10 allows you to search the web right from the taskbar. However, the search engine is set to Bing, and there is no option to change it like you can in the Edge browser. Don't Miss: 45+ Tips & Tricks You Need to Know for Windows 10 This is surely to ir ...more
Update (February 2019): The methods below will help on older Android versions, but we've recently revisited this topic. So if you have a newer Android phone and you want to get rid of Google, head here. It seems like every week there is a new exposé revealing all of the backr ...more
While stickers have long existed in the messages section of Facebook, they've only just recently rolled out sticker capability in comments for events, groups, and timeline posts. That means you can now reply with a cute sticker of a cat eating a slice of pizza on someone's sta ...more
Chrome and Firefox are the leading third-party web browsers on the desktop platform, so it would make sense that they'd go head-to-head in a fight for living room supremacy. The team at Mozilla has been covertly working on a direct competitor to Chromecast over the past month ...more
Phishing is the easiest way to get your password stolen, as it only takes one mistake to log in to the wrong website. A convincing phishing site is key to a successful attempt, and tools to create them have become intuitive and more sophisticated. SocialFish allows a hacker to ...more
Firewall solutions for macOS aren't impervious to attacks. By taking advantage of web browser dependencies already whitelisted by the firewall, an attacker can exfiltrate data or remotely control a MacBook, iMac, Mac mini, or another computer running macOS (previously known as ...more
KeePassX, 1Password, and LastPass are effective against keyloggers, phishing, and database breaches, but passwords managers rely on the operating system's clipboard to securely move credentials from the password vault to the web browser. It's within these few seconds that an a ...more
Cross-site scripting is one of the most common vulnerabilities found on the web today, with repercussions of this type of flaw ranging from harmless defacement to sensitive data exposure. Probing for XSS can be tedious and time-consuming for an attacker, but luckily there are ...more
With just one line of Ruby code embedded into a fake PDF, a hacker can remotely control any Mac computer from anywhere in the world. Creating the command is the easy part, but getting the target to open the code is where a hacker will need to get creative. Ruby is just one wa ...more
It's always a good idea to know how an attack works at the very basic level. Manual techniques for exploitation often find holes that even the most sophisticated tool cannot. Sometimes, though, using one of these tools can make things so much easier, especially if one has a so ...more
If there's one strength of Apple's that iOS and Android fans can agree on, it's the company's dedication to user privacy. With each new iteration of iOS, Apple builds upon these foundations, enhancing and increasing each iPhone's ability to protect its user's data. In iOS 12, ...more
We need to take our privacy and security much more seriously. Whether it's malware-infected apps or the mishandling of our data by companies like Facebook, there are threats all around us in this digital world. Fortunately, some smartphones are simply designed to protect us be ...more
A convincing domain name is critical to the success of any phishing attack. With a single Python script, it's possible to find hundreds of available phishing domains and even identify phishing websites deployed by other hackers for purposes such as stealing user credentials. ...more
There are a number of options and hidden menus within Android that provide users more control over their device. With this control, you can better manage how your phone operates. We came up with a list of tips and shortcuts that, when used, will slowly put you on a path to bec ...more
Deleted bank statements and private photos are still within an attacker's grasp, so don't think that emptying your recycling bin is enough to keep your files from coming back to life. It's possible for a hacker to recover compromising files and images from a backdoored compute ...more
Screenshots taken from a compromised computer can provide hackers with access to private emails, photographs, and information found in sensitive documents. This data can be used by the attackers to build profiles of a target for social engineering attacks and blackmail or even ...more