Wireless networks. Nowadays, everyone uses 'em, but most don't secure 'em. On average, I can drive up and down any block in my city and find at least one or two open or semi-open networks on any given day. With some changed MAC addresses for good measure, an attacker can use y ...more
No longer do you need to crowd around your tiny smartphone to watch a funny YouTube video with your friends. If you've got a display nearby with a web browser and internet access, you can take control of it with your mobile device for free with the new Clik app. It's simple. ...more
In this Computers & Programming video tutorial you will learn how to hack into a compuuter, the easiest way. Go to start > run, type in ‘cmd’ > OK. To find the IP address of a website, type in ‘tracert myspace.com’. This example is to find IP address of myspace.com. Th ...more
This video demonstrates how to set your Mac up to accept VNC connections.First we open up the "system preferences". Double click on Sharing and then go down to remote management and check this. We can see some options . Check the options Open and quit the application, Change s ...more
In this video we learn how find out IP addresses of websites and shut down the computers with those IP addresses. To do this click "start", then "run" then type command prompt. In the command prompt type "tracert website" (example tracrt Google.com) then hit enter. Various IP ...more
Most people own a Wii system, or at least have seen the infamous Wiimote that serves as the controller for the console. What most people have overlooked is that this handy piece of technology can be set to work on PC. Surf the web or scroll through photo albums without the nee ...more
VNC stands for Virtual Network Computing. It is remote control software which allows you to view and fully interact with one computer desktop (the "VNC server") using a simple program (the "VNC viewer") on another computer desktop anywhere on the Internet. The two computers do ...more
Brutus, first made available in 1998, is one of the fastest, most flexible remote brute-force password crackers you can get your hands on - it's also free. It is available for Windows 9x, NT and 2000. In this video tutorial, you'll learn how to use Brutus to crack a Linux box ...more
Wii Saber is a new MAC program that allows the player to hook up a Wii remote to the MAC OSX and play lightsaber games. Finally, the long-awaited union of MAC and Star Wars nerds. Watch this video computer tutorial and learn how to play lightsaber on a MAC with a Nintendo Wii ...more
This video describes that how to use the file transfer protocol prgram. First we have to download filezilla to our computer. Go to google and download it first into the computer. There is a username and password to use the FTP. Open the filezilla and come to Host. There we hav ...more
So, you've downloaded Boxee... Experience TV in a brand new way! This video will help you get started. You Will Need: • Boxee • A television (optional) • A remote control (optional) Step 1: Explore the feed and featured content Check out the home screen, Boxee’s command c ...more
Just last week, the Flashback trojan scared a lot of Mac users. Now, there's yet another trojan spreading across Mac computers—SabPub. The same Java vulnerability that allowed Flashback in seems to be how this SabPub malware snuck in, along with an Office vulnerability, which ...more
In this video from iPT2gGeec we learn how to control an iPhone from your computer. You need a jailbroken iPhone to do this and use a program called Veency. Open Cydia. Search for Veency. Install it. That is all you need to do with your iPhone. Now to get it to work on your co ...more
Tired of squinting over your laptop? There are several ways to turn a big-screen TV into your new computer monitor and enjoy video games, web content, and photos like never before. Step 1: Connect with S-Video First, connect a video cable. For PC users, an easy option is an S ...more
Microcontrollers are great. You can do anything from water your garden to catch wildlife trash diggers in the act—and on the cheap. I prefer to use the Arduino microcontroller because of the large and helpful community built around the website. Though it is my favorite, there ...more
Pull up outside any construction site and you'll see tools scattered about—hammers, jigsaws, nail guns, hydraulic pipe benders—these are the tools of the trade. You would be hard-pressed to build a home or office building with just your hands! On that same page, security profe ...more
In this tutorial, we learn how to map network driers from a remote server. First, go to run on your start menu, then type in the id address or server name for what you want to access and press enter. Now, right click on the folder you want to map and click on map network drive ...more
In this Computers & Programming video tutorial you will learn how to change the default Windows Remote Desktop port. It is actually a registry hack. You can check the IP address of our machine by typing ipconfig into the cmd prompt. For hacking into a machine, you should have ...more
This tutorial will show you how to view your iPod or iPhone screen on your desktop. First of all, you need to have a jailbroken iPod for the applications necessary and secondly you will need Wi-Fi. You will need to download the application RealVNC for your desktop and Cydia fo ...more
Picture this: the infrared sensor on your TV is not working and you are blaming it on your remote control batteries. Well, to make sure exactly what is going on, try testing TV remote to be sure. To the naked eye, you might not be able to see the infrared light, so you could t ...more
This video shows in detail and with annotations how to add plugins as sources in XBoxMediaCenter. With these plugins, you can watch selected media content from the web without browsing the websites with the computer. You browse through the items as if they were on the hard dri ...more
If you have a new Mac and run OS X, you probably already use your Apple Remote for your photos, music and movies. But did you know you can use it for your Keynote presentations as well? While running Keynote, press play to begin the presentation, use the forward, or back, butt ...more
Big name individual hackers and hacker groups everywhere in the news are getting caught and thrown in jail. Everytime I see something like this happen, I won't lie, I get a little sad. Then I wonder, how are these guys getting caught? If a group like LulzSec, with all the fame ...more
Fans of Doctor Who know that the sonic screwdriver is the ultimate tool. It can unlock doors, turn on lights, detect life forms, solder wires, and sabotage weapons. Presumably, the sonic screwdriver creates sonic vibrations to achieve whatever the doctor wants by vibrating th ...more
SSH is amazing, and we praise its existence on Null Byte for many reasons. Notably, it allows us to reroute our traffic through encrypted ports on our local host to be sent to its destination when on the go. You can even control your home computers remotely over a secure and e ...more
Haven't you ever wanted to live in a futuristic home? I think that homes are headed towards an era where they will be controlled by our computers and smartphones. No longer will you have to find your keys to unlock your door, or wait until you get home to monitor your security ...more
SSH is what is referred to as the Secure SHell protocol. SSH allows you to do a plethora of great things over a network, all while being heavily encrypted. You can make a remote accessible shell on your home computer that gives you access to all your files at home, and you can ...more
When you're out and about in the dangerous world of Wi-Fi, it's hard for the average computer user to stay protected, or even know what being protected entails. Little do most people know, Windows 7 has a built-in security that few people take advantage of: a VPN (Virtual Priv ...more
Wired posts a gallery of the original models of now iconic devices, with some fun tech-fetish facts. Did you know the first cell phone weighed a whopping 4.4 pounds? Or that the world's first super soaker was invented completely by accident? Examples below; click through for W ...more
You can connect to an SSH server or connect to an FTP server from you windows computer. Open the run dialogue in your windows and type in cmd. Press OK to open the command prompt. Type in ftp command and press enter. This brings up the ftp prompt. Type o to connect to a server ...more
I've seen numerous tutorials on how to create a "strong" password. This makes me laugh. These titles imply "one" password, which is wrong in and of itself. A person should have many passwords, all different, and all extremely long. People may ask how they're supposed to rememb ...more
Piezoelectric Energy In this article, I'll show you how to make a small, wallet-sized device that generates electricity from kinetic energy. The concept is simple: Piezoelectricity is the charge that is produced when certain solid materials (commonly ceramic and crystal) in r ...more
Like the recent XSS 0day exploit found in the Mac and Windows versions of Skype, a similar one has been found in the Skype app for iPhone. The vulnerability allows an attacker to send a message that contains malicious JavaScript code in the "Name" parameter. This code can stea ...more
With the Kodak Zi8, the power to capture razor-sharp, full 1080p HD video fits in the palm of your hand. Its easy, one-touch operation and incredible versatility make it the perfect camera for beginners, experts, and everyone in between. Step 1: Get started Get started in a s ...more
A lot of different places have computers with controls on them for several things; some have controls for installing software, some for running software, blocking websites, opening certain file formats, etc. Obviously, not all places use the same methods, and not all of the m ...more
I have an absolutely wonderful time making projects and writing articles for all of you mad scientists! Today, I will bring you behind the scenes for a look at the workbench, tools, and software that make the Mad Science World possible. Above is my beautiful workbench! My who ...more
When it comes to webcams these days, most people are using their laptops over desktops. The cameras are centered, integrated, and require no configuring. They're a cinch and usually have great resolution. So, then what do we do with all of those old wired desktop webcams that ...more
This Null Byte is a doozey. On Sunday, September 19th, an exploit for the latest Mac OS X 10.7 "Lion" was discovered by Patrick Dunstan. This exploit allows for an attacker, even remotely, to request to have the root user's password changed without knowing the password to the ...more
This German video is amazing. A joyously analog interpretation and deconstruction of the digital gaming experience. Malte Jehmlich is as primitive and inspiring as the the Vanuatu natives who devoted themselves to cargo worship after World War II! Try to imagine. It's 2010 an ...more
Smartphones are crazy awesome. You can do your banking, track your children, find directions, and even pretend to have a mustache. The only thing that these personal supercomputers are missing is physical interaction with the environment. I wanted to be able to call my house ...more
You've probably seen those deep-web images floating around on the Internet. Usually, it goes something like this: There is a towering iceberg and the deeper the underwater portion extends, the more “hidden” and “exotic” the content is described to be. Sometimes these images ar ...more
Hallelujah, a miracle tool has been released to the world. This Windows/Mac tool is called Spirit and it enables you to jailbreak any iPhone, iPod Touch or iPad quite easily. And Gizmodo is all over it, with an in-depth guide on exactly how to do it. Some of you may be hackin ...more
Technology: The Less You Know the Better? I'm sure everyone is now aware of GPS technologies and tracking techniques these days, with the release of numerous documents (even lawsuits) on big name companies like Apple, Microsoft, and Google. Yes, 2011 was a good year for eye-o ...more
WonderHowTo is a how-to website made up of niche communities called Worlds, with topics ranging from Minecraft to science experiments to Scrabble and everything in-between. Check in every Wednesday evening for a roundup of user-run activities and how-to projects from the most ...more
Every new Apple computer ships with an Apple remote, which can activate the Front Row program and let you play music, view photos or watch videos when you are away from your computer. However, Apple remotes will connect to all nearby devices, so people with multiple Macs or iP ...more
Tutorial showing the basic netbios commands in Windows to access or hack a remote, unprotected computer. Use basic netbios commands. Click through to watch this video on tricklife.com
Bring harmony to your digital world by getting your iPhone and your computer to work together. Watch this video to get the scoop on RemoteMouse from Cydia, a hack that will turn your iPhone into a remote control for your computer.
Remote desktop in windows is set up with these easy to follow steps. First go to your start menu this is in the bottom left corner of your desktop. In the start menu locate your control panel. In the control panel open up your systems folder. Once this is open click the remote ...more
While SSH is a powerful tool for controlling a computer remotely, not all applications can be run over the command line. Some apps (like Firefox) and hacking tools (like Airgeddon) require opening multiple X windows to function, which can be accomplished by taking advantage of ...more
Remote Desktop gives you access to your Windows 8 PC or device from wherever you are to run your applications and access your files remotely. Left an important document on your work computer? Want to run a legacy x86 desktop app from your Surface? You can use Remote Desktop ...more
While you can do a lot of things on your smartphone that were once only done on a computer, having a laptop is still necessary and critical for many tasks. Often times, the two devices work very well together. We recently covered Google's Chrome Remote Desktop, an app that al ...more
Having access to your computer from your cell phone is an extremely useful feature. Whether you need to edit documents or send files that are on your home desktop, or you simply want to watch movies you have saved on your computer, access is key. Kind of makes you wish you co ...more
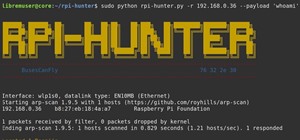
With a cheap computer, smaller than the Raspberry Pi, an attacker can create a remote hacking device. The device can be attached to a target router without anyone's knowledge and enable the hacker to perform a variety of network-based attacks from anywhere in the world. As th ...more
Hacking Wi-Fi is a lot easier than most people think, but the ways of doing so are clustered around a few common techniques most hackers use. With a few simple actions, the average user can go a long way toward defending against the five most common methods of Wi-Fi hacking, w ...more
If you've ever needed to prove you have remote access to a device, or simply want a way to convince someone their computer is haunted, SSH can be used to make a device begin to show signs of being possessed. Spooky Action at a Distance If you need to prove you've got remote ...more
Google TV gives the new Chromecast a home screen full of curated content from your various streaming subscriptions, but it's just that — a home screen app. Underneath, Google's new dongle is running Android TV, meaning its home screen is just a launcher that can be installed o ...more
If you're worried about the security of your Mac, there are easy measures to prevent the most dangerous attacks. Named after the tactic of accessing an unattended computer in a hotel room, we can thwart "evil maid" attacks with Do Not Disturb and LuLu, free macOS tools by Obje ...more
Apple's macOS operating system is just as vulnerable to attacks as any Windows 10 computer or Android smartphone. Hacker's can embed backdoors, evade antivirus with simple commands, and utilize USB flash drives to completely compromise a MacBook. In this always-updated guide, ...more
BitTorrent—corporations hate it with a passion, but the people love it. The notorious file-sharing protocol was responsible for 36.8% of all upstream Internet traffic last year, as well as 10.3% of all traffic. Unfortunately, BitTorrent has gotten a bad rap with its role in p ...more
If you've grown bored of day-to-day hacking and need a new toy to experiment with, we've compiled a list of gadgets to help you take password cracking and wireless hacking to the next level. If you're not a white hat or pentester yourself but have one to shop for, whether for ...more