A recent TED Talk makes a strong case for the healthcare industry to adopt augmented reality as a means to expanding access to surgical care across the globe. During her presentation held in New Orleans in Nov. 2017, Nadine Hachach-Haram, surgeon and co-founder of Proximie, a ...more
Although lots of the bigger hotel chains are lessening the restrictions they put on their room TVs, some smaller ones are still taking measures to prevent you from plugging in computers or streaming devices into an HDMI port. However, there are a few steps you can take to bypa ...more
Comparing the present-day states of the consumer and enterprise sectors of augmented reality is like evaluating the merits of sports car versus work trucks. Like consumer AR, sports cars are sexy and exciting, but perhaps a bit impractical at times. On the other hand, enterpri ...more
A relay is an electrical component that works like a light switch, where it's turned on or off with an electrical signal. By connecting a relay to a Wi-Fi connected microcontroller like an ESP8266, you can build a connected switch that can be controlled from the web browser of ...more
The latest business move by Magic Leap could result in a significant boost to its spatial computing platform's performance and headset design. On Friday, Magic Leap announced the acquisition of Computes, Inc., makers of a decentralized and distributed mesh computing platform. ...more
Whether you're in high school or college, you no doubt will have your iPhone in your pocket all day long. To make your iPhone last the whole time and even help you out with your studies, these are the accessories you'll want to get your hands on. You might not think you need ...more
Conducting phishing campaigns and hosting Metasploit sessions from a trusted VPS is important to any professional security researcher, pentester, or white hat hacker. However, the options are quite limited since most providers have zero-tolerance policies for any kind of hacki ...more
A Norwegian shipping company says it will launch an unmanned container ship within four years, as the shipping industry begins to apply driverless technology to commercial sea transportation. Norway-based Yara International ASA claims the vessel will be the world's first auto ...more
Every day the young world of mixed reality is creating new ways for people to work with with computers. We are looking for, and finding, new ways for these head-worn computers to understand what we tell them. Sometimes it is with our hands, sometimes it is where we turn our he ...more
Getting caught using your iPhone at school or work (when you're using it for personal reasons) can be a little bit embarrassing. Even worse, it can be detrimental to how you're perceived by your teacher or boss. But sometimes you just have to beat that next level of Candy Crus ...more
Like insurance, it's always better to have a computer mouse and not need it than to need it and not have it. Honestly, I don't want to carry around a clunky mouse with my laptop, so I don't. I do something else, something more convenient. I use my Nexus 7. If you want to give ...more
There is nothing worse than losing valuable information or programs on your computer. And if you've ever accidentally deleted a file or document, you know how agonizing that entire process can be. In order to avoid such mishaps, you should always back up your computer's data ...more
Earlier this week, Spiderlabs' vulnerability researcher Jonathan Claudius discovered a key in Windows 7 and 8 registries that makes it easy for anyone with physical or remote access to a computer get a hold of the user's password hints. When the "UserPasswordHint" key is read, ...more
With many office workers in the US being asked to work from home if their job allows, Magic Leap's customary updates for the Lumin OS and Lumin SDK brings some help to keep distributed workforces connected. Chief among the new features arriving with Lumin OS version 0.98.10 a ...more
Augmented reality is becoming a slam dunk for sports entertainment, as leagues, their teams, and their broadcast partners have been quick to adopt AR. This obsession with the immersive space is particularly true when it comes to the NBA. The league itself has produced AR apps ...more
Transferring hundreds of screenshots, webcam recordings, keystroke logs, and audio recordings between your VPS and a local Kali machine can be tricky. Services like Dropbox don't always have the best privacy policies and suffer data breaches just like any other website. To mit ...more
After backdooring a MacBook not protected by FileVault or using a fake PDF to gain remote access, an attacker may wish to upgrade their Netcat shell to something more fully featured. While a root shell allows attackers to remotely modify most files on the MacBook, Empire featu ...more
In a LinkedIn post published on Tuesday, Microsoft's leading advocate for the HoloLens made a prediction that the mixing of immersive technologies will define augmented reality in 2018. Alex Kipman, the Technical Fellow for new device categories for Microsoft's Windows and De ...more
welcome back my masters , teachers and classmates , in this second part of this 0-day series we will learn the basic of fuzzing, and i bought some gift for nullbyte(a 0 day vuln that will be released today exclusively on null-byte) . INTRODUCTION As i love wikipedia so much a ...more
As most everyone knows, Android and Apple don't get along so well. Even the users don't get along well, with Android and iPhone users constantly berating and insulting each other online—any chance they get. I should know, since I was one of them, but I'm now rare breed who's l ...more
We use smartphones for just about everything, and while that may be beneficial to us in our day-to-day lives, it can also be used against us in the court of law. Law enforcement officials can seize smartphones and give warrants to Apple, Google, your cellular provider—whoever ...more
Dig this. 40% of the energy consumed in your home is from appliances that are allegedly 'off'. That cellular power supply charger...that 'sleeping' computer...that appliance that has a remote control. All guilty. You may be motivated by being green. Me. I am motivated by sa ...more
Computer vision is a key component in enabling augmented reality experiences, but now it can help give sight to the blind as well. In this case, that assistance comes from Envision, developers of mobile apps for iOS and Android that use optical character recognition (OCR) and ...more
After a rough run of news, smartglasses maker North still has the confidence of investors, as evidenced by its latest round of funding. Speaking of smartglasses, Google will continue to court businesses over consumers, as the tech giant announced its next-generation of Glass ...more
It looks like there is a fatal flaw in the current macOS High Sierra 10.13.1, even straight from the login menu when you first start up the computer. This severe vulnerability lets hackers — or anyone with malicious intentions — do anything they want as root users as long as t ...more
Generally speaking, in terms of modern devices, the more simple you make an interface to navigate, the more successful the product is. The product could be a coffee maker, an electric piano, a smartphone, or computer operating system. This very idea was one reason that Window ...more
With chips in four out every five PCs made since 2010, few companies are as pervasive in modern computing as Intel. That's why an advisory released Monday, May 1, confirming a remotely exploitable vulnerability in all non-server business hardware made in the last seven years h ...more
Even though your phone has a built-in media player, it's got nothing on VLC. The popular third-party video player supports virtually every codec and file format, and even better, you can use it to stream movies, shows, and other video files from your computer to your phone. I ...more
When you wear a holographic computer on your face, you gain some things and lose others. That's certainly the case when using Skype in Microsoft's HoloLens. Some video chats will work better because your caller can see what you see, rather than your face—but others just feel w ...more
In a letter dated February 16th, Apple CEO Tim Cook responded to the FBI's demand that Apple create a "backdoor" to bypass the encryption on an iPhone used by one of the perpetrators of last year's terrorist attack in San Bernardino, CA. Cook began the letter by stating that A ...more
I saw many people asking for a Tutorial about writing their own Remote Administration Tool, so I now introduce you in a basic kind of RAT. This program is not for real use, but for learning how you could write this kind of tool. It will be basicly coded and not very refined. I ...more
Hi I am a new member of null byte(although I am reading this website from the beginning) and this is going to be my first post. Let me introduce myself first ! I am from Greece, I am working as a network engineer and I am into system and network administration but definitely ...more
In part one of this tutorial we found out that your English teacher is a paedophile, by using a Man in the Middle attack to intercept his internet traffic. Now you're faced with the dilemma of how to alert other staff at the school to how creepy he is without letting on that ...more
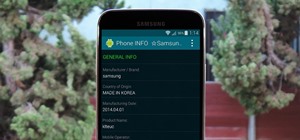
There really isn't any custom manufacturer skin, like Sense, that can match the clean look and fluidity that comes with stock Android. HTC knows this, and they, just like Samsung, include a Google Play Edition version in their flagship lineup. In effect, these GPE variants pu ...more
You probably use your smartphone to mostly surf the web, play games, and communicate with others, but there's so much more it can do. Thanks to integrated features and third-party apps, you can seamlessly control things around your home, including your TV, tablet, Bluetooth sp ...more
Welcome back, my hacker novitiates! Finding vulnerabilities in systems can be one of the most time-consuming tasks for a hacker. There will be times, though, when you'll find yourself in a position that you know that a particular port represents a vulnerable application or se ...more
A single movie download can consume a good ten percent of the storage on your Nexus 7 tablet, unless you went all crazy and opted for the 32GB model. Even then you're bound to run out of space fast, especially if you're like me and have tons of media files you want readily acc ...more
These days, we increasingly have more and more devices in our everyday possession. While a notebook computer, a tablet, and a smartphone may seem like overkill, they do work to make our lives easier and even help reduce clutter in certain ways. A single one of these devices c ...more
Welcome back, my hacker novitiates! Like in my last article on remotely installing a keylogger onto somebody's computer, this guide will continue to display the abilities of Metasploit's powerful Meterpreter by hacking into the victim's webcam. This will allow us to control t ...more
When setting up a Raspberry Pi, it's easy to overlook changing the default password. Like many IoT devices, the Raspberry Pi's default Raspbian operating system installs with a widely-known default password, leaving the device vulnerable to remote access. Using a tool called r ...more
Your social security number, credit card information, and medical history can fall into the wrong hands if you're not careful about how and where you share your data online. If you really care about your data, there are tools and techniques you can utilize to protect yourself ...more
It's important to know who you're dealing with after hacking your target's MacBook. Getting remote access is simple, but covertly gathering information about the user and their system can be a challenge. Continuing with our situational awareness attacks, we'll be further orie ...more
Using Netcat to backdoor a macOS device has its short-comings. If the compromised Mac goes to sleep, the Netcat background process will occasionally fail to terminate correctly; This leaves Netcat running infinitely in the background and the attacker with no new way into the d ...more
The misconception that macOS is more secure than the Windows operating system is far from the truth. With just one small command, a hacker can completely take over a MacBook and control it remotely. The sheer volume of Windows computers currently in operation around the world ...more
As someone with a pretty nice TV, I've never found the allure in purchasing a projector. While they're certainly smaller and sleeker than a television, and more portable, they can be pricey and produce a less than stellar image. And who really buys a projector anyways? They're ...more
Roughly a year and a half after unveiling the HoloLens-like ThinkReality A6, Lenovo is back with its take on enterprise-grade smartglasses, and the results look impressive. Then again, looks can be deceiving. On Sunday, a day ahead of the opening of the virtual Consumer Elect ...more
For over three decades, Microsoft's landmark program, Excel, has helped businesses accomplish tasks and problem solve quickly and efficiently. Whether you're a budding entrepreneur or navigating a remote career, Excel can help you apply your business skills at a higher level. ...more
While consumer-grade smartglasses are the holy grail for tech companies, smartglasses maker Vuzix knows where its bread is buttered, and that's in the enterprise segment. As such, the company used the Consumer Electronics Show (CES) 2020 as its stage for unveiling the M4000, ...more
Over the past year, Magic Leap has teased its cross-platform vision of the AR cloud, which it dubs the Magicverse. While the company shared a timeline for its debut next year, it also served up new developer tools for the present. Facebook is also looking to the future of aug ...more
When the Steam Link app was first introduced in 2018, I was impressed. As long as you were on the same network as your PC, you could play your Steam games on your phone. But now, it's even more impressive. By enabling a few extra settings, you can play your Steam library on mo ...more
While modern browsers are robust and provide a lot of functionality, they can be unlocked to do some pretty spectacular things with browser extensions. For hackers and OSINT researchers, these tools can be used to defeat online tracking, log in to SSH devices, and search the i ...more
Auditing websites and discovering vulnerabilities can be a challenge. With RapidScan and UserLAnd combined, anyone with an unrooted Android phone can start hacking websites with a few simple commands. RapidScan does an excellent job of automating the deployment of vulnerabili ...more
The old school staple of many US homes with children, the remote control race track, has been given new life in augmented reality thanks to the Room Racer app for iPhones and iPads. Using ARKit, the app places a miniature race track on a floor or tabletop. The game includes n ...more
Images captured by Microsoft's next generation Kinect depth-sensing camera that will facilitate augmented reality experiences in the next version of the HoloLens and give computer vision to untold multitudes of connected devices in enterprise facilities, have made their way in ...more
SSH is a powerful tool with more uses than simply logging into a server. This protocol, which stands for Secure Shell, provides X11 forwarding, port forwarding, secure file transfer, and more. Using SSH port forwarding on a compromised host with access to a restricted network ...more
In a previous article, we learned how to take advantage of a feature, Dynamic Data Exchange (DDE), to run malicious code when a Microsoft Word document is opened. The biggest challenge of this attack is that it requires getting the user to agree to a pop-up prompt. Fortunately ...more
If competition in the augmented reality space was a spectator sport, then ARKit, ARCore, and HoloLens dominate the prime-time broadcasts on ESPN. If you're looking for the race to be the "Cardboard for AR," you might need to tune-in to ESPN2. There, you would learn that Mira ...more
Every year, football fans get excited about the next crop of blue chip prospects joining their teams, from five-star high school recruits graduating to college to first-round rookies drafted into the NFL. Those who follow the game more closely realize that, despite their prom ...more
In my previous article, we learned how to generate a vulnerable virtual machine using SecGen to safely and legally practice hacking. In this tutorial, we will put it all together, and learn how to actually hack our practice VM. This will provide some insight into the methodolo ...more
Imagine for a moment that a VPN is like putting on a disguise for your computer. This disguise works to change your IP address, secure your traffic with encryption, and mask your location to bypass regional restrictions. This makes it a helpful tool for both whistleblowers and ...more