FarmVille hacks, cheats, glitches! FarmVille is the hottest application on Facebook which lets members manage a virtual farm by planting, growing, and harvesting crops, trees, and livestock. Grow delicious fruits and vegetables and raise adorable animals on your very own farm! ...more
Web applications are a prime target for hackers, but sometimes it's not just the web apps themselves that are vulnerable. Web management interfaces should be scrutinized just as hard as the apps they manage, especially when they contain some sort of upload functionality. By ex ...more
Not everyone digs Siri. Some of you probably can't live without the personal assistant on your iPhone, and some of you probably never even use it — and likely never will. If you fall into the latter category of iPhone users, you can simply disable the feature altogether, which ...more
Get ready to draw like Leonardo da Vinci, or, at least, trace like him. A new augmented reality app, SketchAR, is the first mobile app that uses AR to allow users trace an image on real paper. The Lithuania-based company describes their product as "an application through which ...more
If you're part of the Windows 10 Insider Program, build 15048 launched this morning, and included a nice big unannounced surprise. You can now launch the Mixed Reality Portal and enable the simulation to try out mixed reality right from your PC, even if you don't have one of t ...more
Working from home has its perks. You don't need to commute, you can work in your pajamas, and you don't even need to clean your house, especially if you're using Zoom for video meetings on your smartphone. Instead of clearing toys from the floor or moving that pile of clothes ...more
Whether you're riding the subway on your way home from work, or stuck in the backseat of the car on a long road trip, there are times when you need to entertain yourself without a mobile data connection. A good mobile game would pass the time perfectly, but not every game work ...more
You may have asked yourself, "How do hackers take my password, if the website owner can't?" The answer is simple. When a website stores your login password for the site, it is run through a cryptographic hash function before it enters the database (if the website isn't Sony). ...more
While modern browsers are robust and provide a lot of functionality, they can be unlocked to do some pretty spectacular things with browser extensions. For hackers and OSINT researchers, these tools can be used to defeat online tracking, log in to SSH devices, and search the i ...more
With the release of the Mirai source code, botnets are back in a big way. In the early days of botnets, zombies (infected hosts) would report to IRC (Internet Relay Chat) channels for CNC (command and control) instructions. Modern botnets have evolved, but they continue to use ...more
These days, there is hardly a place in America that doesn't have access to the internet. But with web usage fees and ridiculous cell phone provider contracts, sometimes it's still necessary to go a little DIY when it comes to staying connected. If you have a Windows 7 or 8 co ...more
Unlike most of Apple's other apps and services, it's not always obvious when Siri gets new features. Even if you're an avid Siri user, there's no way you can catch them all, especially when half of them aren't even mentioned by Apple anywhere. But that's what we're here for, a ...more
For many, phones are starting to replace televisions as the primary device for watching videos. Thanks to their portability and easy to use apps, it's often simpler to watch Netflix, Hulu, YouTube, or Prime Instant Video on the smaller screen. But not every phone is suited to ...more
Now that we've got all of our software installed, we're going to proceed with the next step in our HoloLens Dev 101 series—starting a fresh project and building it into a Holographic application. Then we will output the application to the HoloLens Emulator so we can see it in ...more
The LG V30 is an amazing device that will contend for best smartphone of 2017. It has all the major features you'd expect from a high-end flagship, and it even includes what's become a rare commodity these days — a headphone jack. However, for the purists out there, the LG UX ...more
Networking is built largely on trust. Most devices do not verify that another device is what it identifies itself to be, so long as it functions as expected. In the case of a man-in-the-middle attack, we can abuse this trust by impersonating a wireless access point, allowing u ...more
When you enable Low Power Mode on your iPhone, it's not always clear what measures it's taking to reduce battery drain and conserve power. Changes to energy-hungry features you use daily may be immediately noticeable, but some things you use frequently may be disabled or reduc ...more
For a photo- and video-sharing app based around privacy, Snapchat sure has a lot of security holes floating around. At one time, you were able to take screenshots of Snapchats in iOS 7 without the sender knowing, which is something that you can still do on rooted Android devic ...more
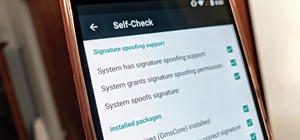
It would only make sense that Google is one of the most active app developers on the Android platform, particularly when you consider that they develop the platform itself. From my count, there are an astounding 117 unique apps that the search giant and its subsidiaries have p ...more
As Android's official app provider, the Google Play Store is packed with thousands of useful programs. But Google's terms of service is extremely restrictive, which means that countless apps simply don't qualify to be hosted on the Google Play Store. As a result, many great a ...more
Gaining access to a system is always exciting, but where do you go from there? Root or bust. Sure, a compromised host is a great way to run a botnet, or do some other boring, nefarious thing—but as hackers, we want root. We also want to take the easiest path possible, search o ...more
The Galaxy S8's Always On Display is a fantastic feature that gives you a brief overview without having to wake up your phone. But AOD now has a virtual home button, which kinda ruins the sleek look and can even cause screen burn-in. Regardless of your reason, if you're not a ...more
Auditing websites and discovering vulnerabilities can be a challenge. With RapidScan and UserLAnd combined, anyone with an unrooted Android phone can start hacking websites with a few simple commands. RapidScan does an excellent job of automating the deployment of vulnerabili ...more
By default, as soon as you join a meeting on Zoom, both your microphone and camera turn on, sharing your audio and video to the other chat participants. While that isn't usually a problem, it can be an issue if the meeting hasn't started or you're entering in the middle of a c ...more
Dating websites allow you to see a person in a very intimate context, framing their successes and accomplishments in life to an important audience. The information contained in these profiles often can't be found elsewhere, offering a unique look into the personal life of the ...more
Kali Linux is established as the go-to operating system for penetration testing, but in its default configuration, it's less than ideal for regular desktop use. While in many scenarios, a live boot or virtual environment can resolve these issues, in some situations, a full ins ...more
Coinhive, a JavaScript cryptocurrency miner, was reportedly discovered on the BlackBerry Mobile website. It was placed there by hackers who exploited a vulnerability in the site's e-commerce software that allowed them to anonymously mine cryptocurrency every time the website w ...more
Using an iPhone isn't difficult, but it can be if you're using it for the first time, especially if you switched from an Android phone. That's primarily because of the massive difference in the user interface between the two operating systems. And when it comes to taking scree ...more
Web applications are becoming more and more popular, replacing traditional desktop programs at an accelerated rate. With all these new apps out on the web comes various security implications associated with being connected to the internet where anyone can poke and prod at them ...more
Once a hacker has created a PowerShell payload to evade antivirus software and set up msfconsole on their attack system, they can then move onto disguising their executable to make it appear as a regular text file. This is how they will get a Windows 10 users to actually open ...more
Take a look at this instructional video and learn how to load virtual console games onto your Nintendo Wii. You'll need the Twilight Hack and an SD card for this process. The Twilight hack allows you to run unofficial software through the SD (Secure Digital) card inserted into ...more
You can easily get to level 100 on Happy Aquarium with Cheat Engine. But hurry, before they patch the game. Hurry to level up! Watch this video tutorial to learn how to hack Happy Aquarium levels with Cheat Engine (10/09/09). For all of the details on this Happy Aquarium hack ...more
A simple security flaw can allow an attacker to gain a strong foothold with little effort on their part. When a web application permits remotely hosted files to be loaded without any validation, a whole can of worms is opened up, with consequences ranging from simple website d ...more
The new Samsung Galaxy S8 and Galaxy S8+ phones were announced on March 29 at the Samsung UNPACKED 2017 event. Preorders start on March 30 for the Korean tech giant's latest flagships, and sales officially begin in the US on April 21. Samsung will need a smooth release to win ...more
There are tons of good reasons that you might want to use Android on your desktop. Perhaps your favorite game is only available on Android, or maybe you use a messaging service that doesn't have a Windows companion app. Whatever the reason, if you've ever found yourself wishi ...more
The Raspberry Pi loads an operating system from whatever SD card you insert, allowing you to keep different operating systems on separate SD cards depending on which OS you wish to run. A tool called BerryBoot cuts down on the number of SD cards needed by providing the ability ...more
Club Penguin is a flash-based website with an a virtual world of online games for kids to play. Learn how to hack Club Penguin with tricks and cheats. Watch this video tutorial to learn how to wear member clothes as a non-member in Club Penguin (09/23/09). Download CP Trainer ...more
In the past, Apple never really put much work into its Contacts app for iPhone, making the tool much less useful than its Mac and iCloud counterparts. But now the Contacts app for iOS is a force to be reckoned with. Packed with new features (some hidden), it's finally good eno ...more
In this video you will learn how to download a torrent PC game, mount and the burn it. For this you will need a torrent program (to download torrents), daemon tools (to mount the images) and powerISO (to burn it). To get a torrent go on site mentioned in the video or on other ...more
In one of my previous articles, I discussed ShinoBot, a remote administration tool that makes itself obvious. The goal is to see if the user could detect a remote administration tool or RAT on their system. In this article, I'll be demonstrating the use of Pupy, an actual RAT, ...more
These days, that pocket-sized computer we call a smartphone is home to your entire digital life. But with the onset of mobile payments and online banking, the line between your virtual world and the physical realm is becoming increasingly blurred. We vigilantly remember to lo ...more
With Cheat Engine you can hack just about any flash game, including Happy Island. And the one thing you're going to want to hack over and over again is money! See this video tutorial for learning how to do a coin cheat on Facebook's Happy Island (12/19/09). Download Cheat Eng ...more
They're finally here — Samsung has officially revealed the Galaxy S9 and S9+, which run Android Oreo out of the box. Since we've spent plenty of time with the Oreo beta for the Galaxy S8, we already know about some of the best new software features coming to the Galaxy S9. Lik ...more
There's no doubt Kali has established itself as the most popular penetration distribution available. However, just because it's the fan favorite of beginners and security researchers doesn't make it right for everyone. Manjaro Linux is a beginner-friendly Arch-based distributi ...more
Using a keylogger to intercept keys pressed on an infected computer can circumvent encryption used by email and secure chat clients. The collected data can often reveal usernames, passwords, and potentially compromising and private information which hackers abuse for financial ...more
One Instagram creator's augmented reality homage to Disney's deep bench of animated characters has earned him fifteen minutes of fame. Taking a page from the enchanted book attraction at the Sorcerer's Workshop of Disney California Adventure, content creator Arno Partissimo p ...more
In 2013, Offensive Security released Kali Linux, a rebuild of BackTrack Linux derived from Debian. Since then, Kali has gone on to become somewhat of a standard for penetration testing. It comes preconfigured with a collection of tools accessible by a menu system, tied togethe ...more
Google Meet might not have virtual backgrounds like Zoom, but it hits all of the other basics, from hosting many multiples of video participants to sharing your screen, that you'd expect from a robust video conferencing platform. However, one of those essential features, shar ...more
The outstretched arm, the perfectly positioned angle, the shot and the subsequent array of tinkered saturation, contrast and shadows. In almost every car, changing room, or Starbucks, these string of events happen—you might know it as the selfie. Whether these self-portraits ...more
Kali Linux is the obvious first choice of an operating system for most new hackers, coming bundled with a curated collection of tools organized into easy-to-navigate menus and a live boot option that is very newbie-friendly. But Kali isn't the only distribution targeted at pen ...more
For most of us regular folk, the only opportunity to relish in the conveniences of a maid is during hotel stays. Personally, I would love to have a maid around to help fold my clothes and sweep up those crumbs that accumulate in the corners of my kitchen, but sadly, I currentl ...more
So this is my methodology for this project of writing a rootkit. Please leave feedback on what is right/wrong. I tried to simplify concepts the best I could however... One needs an deep understanding of how different types of processors work and how memory protection is imple ...more
Rooting. As an Android user, I'm sure you've heard the word once or twice. According to Kaspersky, 7.6% of all Android users root — but for the 92.4% who don't, we wanted to talk to you. Rooting allows you to remove barriers and open Android to a level of unprecedented contro ...more
"Cheating is for losers" is only something that losers like to say. If you want to smash your friends and fly up the leaderboards, though, sometimes you have to go that extra mile. Bejeweled Blitz is a PopCap game that can be played on your computer, through Facebook, or even ...more
Facebook Messenger is a messaging app first, but of its more than 1.3 billion monthly users, 32 percent use its video chat feature at least once every month. While it may seem pretty straightforward to video call with family and friends on Messenger, there are many tips and tr ...more
With an ordinary birthday card, we can introduce a physical device which contains malicious files into someone's home and deceive them into inserting the device into a computer. In my last series, we used a Post-it note to trick a neighbor into visiting a website that we cont ...more
Contrary to popular belief, augmented reality apps have been available for a while now. I remember using the Layar app (still available for iOS and Android) to explore nearby businesses and landmarks with varying success via an early-generation Android handset. It would be ha ...more
If you buy an Android phone from any of the big US carriers, it will come with several extra apps in addition to any apps the manufacturer preinstalled. It's all in the name of profit, of course. Some of these apps are from companies that paid the carriers to distribute their ...more
Holographic technology has made a push towards becoming a reality for everyday consumers, most recently with the introduction of the Microsoft's HoloLens, which combines real-world and virtual elements in one awesome device. While it may be a while until that this technology ...more
Goertek's AM3D offers world-class audio processing software that powers millions of high-end devices around the world. Their biggest advancement is likely Virtual Surround Sound, which can make two speakers sound like a full 5.1 setup. You normally can't get these features on ...more