The first sneak peak of Android O is finally here. The developer preview promises more features, stabilization, and better performance, according to the Android Developers Blog. Furthermore, there's speculation that the latest operating system will be code-named "Android Oreo, ...more
Relentless in its fury, the iOS text messaging exploit that exploded onto the scene late last week seems to do more damage than initially reported. Used to reboot devices and crash the Messages app, the string of text can also be used to crash third-party apps such as Instagr ...more
Want to get even this Halloween? Want to scare somebody with nothing but a few lines of code? Here's how it can be done... So, with arguably the best holiday quickly approaching us, I thought I'd do a fun post on a cool way to prank your friends, enemies, or maybe even the wh ...more
So, you've got a brand new PlayStation 4, but unfortunately, you've got "No Signal" now, too. You can't really game or watch movies on your new toy if you can't even bring up the PlayStation menu on your TV screen. However, there are a few ways to fix the no connection alert, ...more
We've gotten pretty close to a Google Experience before, and even played around with the actual Google Play Edition build. However, the devs over at XDA have a much better solution: actually converting your HTC One into a complete factory-fresh Google Play Edition. Since most ...more
Having access to your computer from your cell phone is an extremely useful feature. Whether you need to edit documents or send files that are on your home desktop, or you simply want to watch movies you have saved on your computer, access is key. Kind of makes you wish you co ...more
Until recently, brainwave-reading devices have pretty much only existed in science fiction. Sure, electroencephalography (EEG), the technology that powers these devices, has been used in medicine and psychiatry since the late 1800s, but diagnosing people's brains and reading t ...more
With the upcycling revolution, folks are turning their otherwise useless junk into something functional for the home. Practically anything that you would normally toss or recycle can be reused for a bigger and better purpose. Your milk jugs, chopsticks, toilet paper cardboard, ...more
One thing that's very crucial to gardening is the seed starter. Seed starters are very important for a number of reasons, including the fact that is an excellent way to make sure your seeds survive in their own little environment until you’re ready to transfer them to your gar ...more
There's a direct correlation between the proliferation of augmented reality apps and the demand for 3D content, and PTC just quantified that in dollars. On Wednesday, the company committed $470 million to acquire Onshape, makers of computer-aided design (CAD) software that ha ...more
Drone mishaps, such as the collision that scratched a military helicopter in New York, are becoming something of an everyday hazard. And professional drone operators sweat bullets when their drones hover too close to their clients' things — especially their expensive things. ...more
In recent weeks we've talked about the growing trend of smartglasses makers moving the brains of their devices to smartphones, and now a veteran of the space has joined that movement. On Wednesday, Epson revealed the Moverio BT-30C, the company's first truly affordable smartg ...more
For the past few months, Fortnite has been one of the most-watched games on Twitch, and it's likely to keep a top spot on the live streaming platform once Fortnite Battle Royale becomes available for smartphones. While there are not any live streaming capabilities built direct ...more
Rumors that Apple is honing its automated car technology have skyrocketed. Thanks, now, in no small part to some enterprising members of the media who leaked the names of Apple's self-driving car team to the public. Driverless previously reported that Apple received a permit ...more
A group of researchers from Stanford University and Princeton University has put together the largest RGB-D video dataset to date with over 1,500 scans of over 700 different locations across the world, for a total of 2.5 million views. This dataset, called ScanNet, has been s ...more
Cheap Chinese knockoffs have been around for ages, but recently, skyrocketing demand has led to a massive influx of counterfeit smartphones. Sellers on Craigslist seem to have no trouble getting ahold of these fake devices, then passing them off as the real deal and turning a ...more
Welcome back, my greenhorn hackers! After the disaster that was Windows Vista and the limited and reluctant adoption of Windows 8 and 8.1, Windows 7 has become the de facto standard operating system on the desktop/client. Although the most valuable information to the hacker ...more
There's nothing worse than holding an ice cold brewski on a hot summer day and having no way to open it. If you're a Bud fan, you'll have no problem opening the bottle because most mass-market beers have twist-off caps. But if you have a taste for finer, more expensive brews, ...more
This year, as part of the Next Reality 30, in partnership with Snap, we're spotlighting an up-and-coming innovator in augmented reality. Specifically, we were searching for an independent developer or creator who embodies the bleeding edge spirit of AR and its ability to lever ...more
Phone specs get better and better each year, and multiplayer mobile games are right there with them. Instead of playing solo, jump into some real-time gameplay with co-op and player vs. player modes, and battle friends, family, and strangers from around the world. But which mu ...more
There's a feature that every Apple Watch owner should know about — one that makes navigating menus, tapping tiny icons, and interacting with complications, among other things, much easier on the small display. The little-known feature gives you complete control of your Apple ...more
We’ve all been there before. Relentlessly refreshing Ticketmaster and filling in those CAPTCHA codes only to receive the miserable “No tickets are available at this time” message. That’s because ticket brokers with a dozen screens and God knows how many browsers snatch up anyt ...more
Join the Pilot program and learn how to fly! But you're not going to be flying airplanes in this Pilot program, you'll be trying your hands at Google's first laptop computer. It's called the Cr-48, a black notebook wh ich runs an extraordinary operating system— Google Chrome. ...more
These days, eReaders are everywhere. For die-hard book nerds, eReaders offer the convenience of a full library without having to sacrifice shelf space. Sure, there are the paper buffs who swear that you just can't take an eReader with you into the bathtub, but when's the last ...more
I've seen numerous tutorials on how to create a "strong" password. This makes me laugh. These titles imply "one" password, which is wrong in and of itself. A person should have many passwords, all different, and all extremely long. People may ask how they're supposed to rememb ...more
There’s a race on to see who'll be the Instagram of moving pictures. This makes sense, since many of our phones are clogged with video that, so far, no one is going to see. Wouldn’t it be great if there were a simple app that could take our video content, edit it for us, and t ...more
Spam is everywhere and Facebook is no exception. In fact, spammers are constantly stepping up their game by tricking unsuspecting Facebook users to participate in quizzes, games, apps, or "new features" that are actually dangerous computer viruses, spyware, or other trojan hor ...more
WonderHowTo is a how-to website made up of niche communities called Worlds, with topics ranging from Minecraft to science experiments to Scrabble and everything in-between. Check in every Wednesday evening for a roundup of user-run activities and how-to projects from the most ...more
The community here on Null Byte has always been great and helpful in sharing their know-how, even before I took up admin duties in this World. I jumped at the chance of leading Null Byte because I enjoy teaching and informing people on all of the important need-to-know things ...more
Big brother is watching when you're playing around on another system—and big brother is that system. Everything from operating systems to intrusion detection systems to database services are maintaining logs. Sometimes, these are error logs that can show attackers trying vario ...more
WonderHowTo is made up of niche communities called Worlds. If you've yet to join one (or create your own), get a taste below of what's going on in the community. Check in every Wednesday for a roundup of new activities and projects. Thanks to all of our active moderators and ...more
Welcome to the Google+ Insider's Guide to all things Google+. We're dedicated to keeping you updated with all the latest news, tips and tricks on Google+, and this official index will serve as a one-stop catalog of all our How-To articles, as well as all the news & updates we' ...more
Welcome back, my greenhorn hackers! As hackers, we often take for granted that nearly all of our hacking tools and operating system are free and open source. I think it's important to examine a bit of background on how we arrived at this intriguing juncture in the history of ...more
Those of us who are actively developing for the HoloLens, and for the other augmented and mixed reality devices and platforms that currently exist, are constantly looking for the next bit of news or press conference about the space. Our one hope is to find any information abou ...more
With the new year right around the corner, it's time to talk about the end of the 19th century, a time which plays an enormous role in Steampunk. If you've done any reading of British books written from about 1890 to 1899, you may have come across the phrase 'fin de siecle' an ...more
Smartphones are vital travel companions. While you're on the go, they connect you with loved ones back home, help you find tickets and passes for tourist attractions, and make it easy to find your way through foreign roads — but even the most powerful smartphone could use help ...more
After receiving $100 million in funding in 2018, smartglasses maker Rokid is going the crowdfunding route to finance its latest product. On Tuesday, Rokid launched a Kickstarter campaign to fund Rokid Air, AR smartglasses that serve as a virtual display by tethering not only ...more
After tapping Nvidia for its first AR headset, Magic Leap is calling in reinforcement for its future enterprise-focused efforts. On Wednesday, Magic Leap disclosed a partnership with chipmaker AMD to produce a "semi-custom" system on a chip (SOC) that will handle computing, g ...more
Since bringing augmented reality features to Search and Maps, Google has made them arguably the most useful augmented reality products in its portfolio. On Tuesday, at Google I/O, Google unveiled some of its new AR capabilities for the pair of mobile apps. Don't Miss: Google ...more
The virtual collaboration tool known as Spatial has consistently been one of our favorites due to its ability to leverage high-end augmented reality headsets to more easily facilitate remote meetings. Well, now the product just took a massive leap forward by allowing anyone w ...more
For all the benefits 5G brings to cellular data, it isn't without weaknesses, the biggest being privacy. Yes, the latest standard comes with breakneck downloads speeds up to 4.3 Gbps, but at what cost? Like with all things on the internet, 5G devices open opportunities for bot ...more
Along with rebranding Magic Leap 1 for enterprise customers, Magic Leap has gifted its developer community with some new toys with a tease of more to come in 2020. On Tuesday, the company not only introduced a consolidated package of new and existing developer tools that it c ...more
Gathering information on an online target can be a time-consuming activity, especially if you only need specific pieces of information about a target with a lot of subdomains. We can use a web crawler designed for OSINT called Photon to do the heavy lifting, sifting through UR ...more
Introduced along with the iPhone X, Animoji are animated characters, mostly animals, that are rendered from the user's facial expressions using the device's TrueDepth camera system to track the user's facial movements. The first viral phenomenon to emerge from the launch of t ...more
If you've taken the time to edit a video on your iPhone or Android phone, you probably have a purpose for it. Maybe you want to share it to YouTube in hopes of making the next viral sensation. Maybe you just want to save the video to your phone to show off to friends and famil ...more
Most carmakers now agree with Waymo that piloting driverless cars is best left to the machine — with no meddling from the human. In Waymo's case, this assumption dates back years ago. More recently in 2014, Google's driverless arm (before it became Waymo) shocked Detroit when ...more
One thing that I got more and more excited about as we got closer and closer to the Microsoft Build 2017 developers conference was finally learning about the new Acer Windows Mixed Reality head-mounted displays (HMD). Brandon Bray, Principal Group Program Manager at Microsoft, ...more
If you're all out of prank ideas for April Fool's Day, we've got a few that your Apple-loving friends will enjoy (or hate?). You can have a little bit of fun if you don't have access to their iOS device or Mac, but for the best pranks, you will need access to their devices, ev ...more
There was lots of new tech to check out at CES 2016, but you could argue that the majority of the big-ticket items weren't the most unique things in the world. Thankfully, there were a few innovative, unconventional ideas on display, and here are some of our favorites. We Get ...more
When it comes to security, there are usually only a handful of things that you want protected from prying eyes on your iPhone—private photos, scandalous videos, and important text, such as credit card and social security numbers. Protecting your iPhone with a lock screen pass ...more
As a hacker or an aspiring one, You need to be careful and anonymous if your doing anything illegal. But you slipped up. Now someone is tracking you! Well luckily you read this post ahead of time and have a backup plan! The first step in remaining safe is to remain anonymous. ...more
If you took a big step back and really looked at the world, you'd see how downright silly our nations look when they put up fences to separate themselves from one another. Creatures big and small roam free while respecting each other's space, but humans create borders and phys ...more
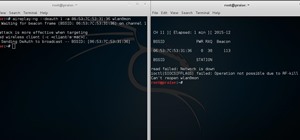
An internet connection has become a basic necessity in our modern lives. Wireless hotspots (commonly known as Wi-Fi) can be found everywhere! If you have a PC with a wireless network card, then you must have seen many networks around you. Sadly, most of these networks are sec ...more
A dead man's switch is a fairly simple concept. If you don't perform a specific task before a set amount of time, it'll perform a specific action you set. They can be handy not just for hackers but for everyone who wants to protect themselves, someone else, or something tangib ...more
It's been done for ages, but for most of us, "regift" entered our vocabulary after the 98th episode of Seinfeld—"The Label Maker." In this episode, Elaine calls Dr. Whatley (played by Bryan Cranston) a "regifter" after he gives Jerry a label maker—the same label maker that Ela ...more
Minecraft is unique among computer games in that some users have created such breathtaking works of beauty and ingenuity that it challenges the very idea that Minecraft is even a game at all, but suggests that it is instead a tool for artistic expression much like Photoshop. ...more
I want to write this article because in my childhood, I had experienced internet stalking which ultimately ended in physical stalking which then lead to several attempted abductions. I have now learned how to use the internet safely, who to communicate with and I've learned ho ...more
I don't know what I'd do without my computer. I can't do my job without the internet. I communicate with employers, friends, and family through emails, video chat and Twitter. I schedule meetings and plan deadlines. I bank. I shop. I read the news. I play games. I watch my fav ...more
In 1965, the world was a different place. There was no Google yet. Or Yahoo. Or Stumbleupon, for that matter. In 1965, the year of your birth, the top selling movie was The Sound of Music. People buying the popcorn in the cinema lobby had glazing eyes when looking at the pos ...more
Night People: A Bad Vibes Label Profile Shawn Reed is one of our favorite people, not content with making music with Wet Hair, he also runs 'Night People' - an almost complete DIY record and tape label operation in Iowa - a label which has consistently put out and introduced ...more