Hak5 isn't your ordinary tech show. It's hacking in the old-school sense, covering everything from network security, open source and forensics, to DIY modding and the homebrew scene. Damn the warranties, it's time to Trust your Technolust. In this episode, see how to build a w ...more
Sometimes shit goes down on your home computer and you're just not able to be home to fix it. After all, most of us have commitments such as school, work, and volunteer activities that keep us away from our home computers for most of the day. For computer emergencies that can ...more
Build a device that automatically takes and uploads pictures of your life every 30 seconds on the Internet.
No longer do you need to crowd around your tiny smartphone to watch a funny YouTube video with your friends. If you've got a display nearby with a web browser and internet access, you can take control of it with your mobile device for free with the new Clik app. It's simple. ...more
For enterprise augmented reality platform makers, remote assistance apps represent one of the greatest opportunities to show off the power of immersive computing. These apps enable experts to guide front-line workers or customers with AR prompts and other content in the field ...more
The Play Store hasn't been the most secure place for apps lately. A quick Google search for "Play Store malware" will give you a taste of some of the malicious apps that snuck their way onto Android's official app store. Google is aware of the problem and they're tying to fix ...more
If you haven't heard yet, Google made it possible a couple months ago for every Android user running 2.2 or higher to track his or her smartphone or tablet using their Android Device Manager service. It's a super easy way to track, lock, and secure erase your Android device fr ...more
With the number of web applications out there today, it comes as no surprise that there are just as many vulnerabilities waiting for hackers to discover. Finding those vulnerabilities can be a difficult task, but there are plenty of tools available to make the process easier. ...more
Shannon Smith shows how to upload files using Filezilla in this episode of No Mac, No Cheese. Filezilla is useful in assisting you with putting files onto a web site. Simply type in your web address, user name, and password. Then create a folder and name it appropriately. Adju ...more
A simple security flaw can allow an attacker to gain a strong foothold with little effort on their part. When a web application permits remotely hosted files to be loaded without any validation, a whole can of worms is opened up, with consequences ranging from simple website d ...more
With popular remote desktop app LogMeIn recently ending its free service, lots of Android users have begun looking for alternatives. There are some good ones out there like TeamViewer and Microsoft Remote Desktop, but today, Google released an app that makes a pretty good cont ...more
The internet has undoubtedly changed the way we work and communicate. With technological advances, more and more people can collaborate on the web from anywhere in the world. But this remote-friendly environment inherently brings security risks, and hackers are always finding ...more
Many of our online accounts now come with an added two-factor authentication (2FA) functionality to help keep our data safe. This essentially means no one would be able to access the account until a specific set of requirements were met. It could be a combination of a password ...more
BitTorrent—corporations hate it with a passion, but the people love it. The notorious file-sharing protocol was responsible for 36.8% of all upstream Internet traffic last year, as well as 10.3% of all traffic. Unfortunately, BitTorrent has gotten a bad rap with its role in p ...more
While the Play Store has a plethora of apps available for finding lost Android phones, Google came out with its own web-based application, Google Device Manager, earlier this year to help you keep track of all your Android devices and remote lock, erase, ring, and track if nee ...more
Wireless networks. Nowadays, everyone uses 'em, but most don't secure 'em. On average, I can drive up and down any block in my city and find at least one or two open or semi-open networks on any given day. With some changed MAC addresses for good measure, an attacker can use y ...more
As smartphone users, we live in dangerous times. The value of phones continues to rise, making them prime targets for thieves. In 2015, the FCC estimated that one million phones are stolen each year, and with several devices starting to hit the $1,000 mark now, these numbers a ...more
Auditing websites and discovering vulnerabilities can be a challenge. With RapidScan and UserLAnd combined, anyone with an unrooted Android phone can start hacking websites with a few simple commands. RapidScan does an excellent job of automating the deployment of vulnerabili ...more
Enterprise augmented reality developer Atheer is bringing its AR solution for enterprise businesses to the HoloLens by way of a joint venture with fellow AR developer Design Interactive. The app, called Augmentor, provides troubleshooting guides to workers through the HoloLen ...more
Apple has a few exciting surprises for you in its latest iOS 16 and iPadOS 16 software updates. Released on Thursday, May 18, version 16.5 includes new features, bug fixes, and security patches, and there are even hints of some big things coming in future software updates for ...more
Technology: The Less You Know the Better? I'm sure everyone is now aware of GPS technologies and tracking techniques these days, with the release of numerous documents (even lawsuits) on big name companies like Apple, Microsoft, and Google. Yes, 2011 was a good year for eye-o ...more
Welcome back, my greenhorn hackers! Sometimes, we don't have a specific target in mind, but rather we are simply looking for vulnerable and easy-to-hack targets anywhere on the planet. Wouldn't be great if we had a search engine like Google that could help us find these targe ...more
Welcome back, my tenderfoot hackers! Web apps are often the best vector to an organization's server/database, an entry point to their entire internal network. By definition, the web app is designed to take an input from the user and send that input back to the server or datab ...more
Along with rebranding Magic Leap 1 for enterprise customers, Magic Leap has gifted its developer community with some new toys with a tease of more to come in 2020. On Tuesday, the company not only introduced a consolidated package of new and existing developer tools that it c ...more
Having an SSH or Secure SHell to tunnel your traffic through is something we have talked about many times at Null Byte. As we know, it allows us to securely route and encrypt our traffic through a remote server, effectively anonymizing us and protecting our traffic from all fo ...more
A recent TED Talk makes a strong case for the healthcare industry to adopt augmented reality as a means to expanding access to surgical care across the globe. During her presentation held in New Orleans in Nov. 2017, Nadine Hachach-Haram, surgeon and co-founder of Proximie, a ...more
Apple's latest big software update includes an entirely new Apple app, a controversial change in the TV app, better Siri control, an improved Shortcuts app, interesting Safari upgrades, Apple Music Sing, and more. Keep reading to see what iOS 16.2 has to offer your iPhone. Th ...more
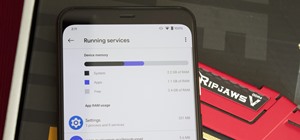
The Galaxy S6 won't hit shelves until later this spring, but that didn't stop the Android community from working its magic and pulling a handful of apps from the device's stock firmware. Several of these apps rely on framework elements that aren't present on current-generation ...more
When it comes to antivirus software, you don't want some fly-by-night developer having access to the sensitive data that these apps can scan. Luckily, most of the longest-tenured antivirus companies from the realm of desktop computers offer complete security suites for Android ...more
Every Friday, Next Reality reviews the latest headlines from the financial side of augmented and mixed reality. This Market Reality column covers funding announcements, mergers and acquisitions, market analysis, and the like. This week's column is led by two companies cashing ...more
It was only a matter of time before the apps from the new Samsung Galaxy S5 leaked for everyone to download and install, and today we've got one that takes advantage of the IR blaster on your Galaxy Note 3. Of course, I'm talking about the updated WatchON app, Samsung's built ...more
Now that we've officially seen the HoloLens 2 and Microsoft has shown off the improvements and new superpowers of the augmented reality headset, what about the specs? Luckily, Microsoft has laid bare the full specifications for its next-generation headset. Let's dive in and s ...more
We use smartphones for just about everything, and while that may be beneficial to us in our day-to-day lives, it can also be used against us in the court of law. Law enforcement officials can seize smartphones and give warrants to Apple, Google, your cellular provider—whoever ...more
If you're using a mobile device, it's a pretty safe bet that your apps are sending lots of information back and forth from their servers. To make sure there is no inappropriate data collection going on, it's worth setting up a web proxy to spy on this traffic, so you know exac ...more
Coinhive, a JavaScript cryptocurrency miner, was reportedly discovered on the BlackBerry Mobile website. It was placed there by hackers who exploited a vulnerability in the site's e-commerce software that allowed them to anonymously mine cryptocurrency every time the website w ...more
While SSH is a powerful tool for controlling a computer remotely, not all applications can be run over the command line. Some apps (like Firefox) and hacking tools (like Airgeddon) require opening multiple X windows to function, which can be accomplished by taking advantage of ...more
These days, there are Android apps for every budget—forgive me if that sounds like a car commercial, but that's just the way things are in the age of the smartphone and tablet. You've got apps that require monthly subscriptions, paid apps that will run you a $30 one-time insta ...more
Welcome back, my rookie hackers! Now that nearly everyone and everyplace has a computer, you can use those remote computers for some good old "cloak and dagger" spying. No longer is spying something that only the CIA, NSA, KGB, and other intelligence agencies can do—you can l ...more
File inclusion can allow an attacker to view files on a remote host they shouldn't be able to see, and it can even allow the attacker to run code on a target. To demonstrate these vulnerabilities, we'll be practicing PHP file inclusion using the Damn Vulnerable Web App. We'll ...more
The new iPhone 5 was just revealed yesterday, and it's 18 percent thinner and just 1/5 the weight of its 4S predecessor. It's also taller with a larger screen, which gives you a fifth row for apps now. As far as speed is concerned, it has a speedy A6 chip and can tap into wire ...more
While the airline, casino, cruise, and hotel industries are asking for government bailouts during the COVID-19 pandemic, companies around the US are giving away its apps and services for a limited time. So while you're stuck at home, keep your mind off of coronavirus with free ...more
While modern browsers are robust and provide a lot of functionality, they can be unlocked to do some pretty spectacular things with browser extensions. For hackers and OSINT researchers, these tools can be used to defeat online tracking, log in to SSH devices, and search the i ...more
There's no doubt iOS 13 has dominated the talk around the Apple community this month. Since the announcement and release of the first developer beta, we iPhone users have had a treasure trove of new features and changes to explore and discuss. Now the fun continues with iOS 13 ...more
When it comes to attacking devices on a network, you can't hit what you can't see. Nmap gives you the ability to explore any devices connected to a network, finding information like the operating system a device is running and which applications are listening on open ports. Th ...more
In the last decade, the number of people working remotely in the US has increased dramatically, and so has their need for technology and software to supplement that remote work. Whether you work from home or a coworking office space, the requirement for highly compatible and h ...more
Computers all over the world rely on a program called "libssh" to use the SSH communications protocol, which allows trusted users to log in and administer computers remotely. Due to a flaw in libssh, fooling a computer into granting SSH access is as easy as telling it you alre ...more
It's no secret that Apple's iOS 16 update is packed with useful features, but some of them Apple never even mentioned. Not at the software's unveiling in June and not even after iOS 16's public release in September. It's actually surprising considering that one little-known ne ...more
The first developer beta for iOS 13 is available to install on iPhone models, but the process for doing so may be a bumpy ride. Apple has not included configuration profiles for the developer beta yet, and many developers are having issues installing iOS 13 even with macOS 10. ...more
In this video tutorial, Chris Pels will show how to deploy a web site using the Copy Web Site Tool in Visual Studio. First see how to connect to a remote web site and deploy an entire site to the target location. Next, learn how to synchronize an entire source and target web s ...more
This tutorial covers the steps on how to turn a Windows enabled mobile phone into a web cam that you can stream over the internet.
Good news, Apple browser fans: Safari now comes with extensions. The bad news? They're not yet enabled by default, and there's no official add-on gallery from Apple. The better news? There's a workaround, and it's easy. In this How To video, we'll show you not only how to enab ...more
This tutorial demonstrates using Amazon Web-Enabled Movie Collection Starter Kit in Visual C# Express.
Hak5 isn't your ordinary tech show. It's hacking in the old-school sense, covering everything from network security, open source and forensics, to DIY modding and the homebrew scene. Damn the warranties, it's time to Trust your Technolust. In this episode, see how to defend yo ...more
In this video, you will learn the steps to take to enable JavaScript in Microsoft's Internet Explorer (IE) web browser. Although JavaScript support is typically enabled by default in most modern browsers and many web applications depend on JavaScript being enabled to function ...more
The Junkyard Jumbotron is an amazing project that allows a collection of random web browser enabled displays—laptops, smartphones or tablets—to share a single image split across the group, creating one large virtual display. Created by Rick Borovoy at MIT's Center for Future C ...more
Like the recent XSS 0day exploit found in the Mac and Windows versions of Skype, a similar one has been found in the Skype app for iPhone. The vulnerability allows an attacker to send a message that contains malicious JavaScript code in the "Name" parameter. This code can stea ...more
In this video tutorial, viewers learn how to use Remote Desktop on Windows Vista to connect to another computer over a network connection, specifically Windows XP. You can get access to your Vista applications or data stored on a remote computer from your XP PC. Users will ne ...more
With give or take 250 million cars in America, odds are most city dwellers waste time hunting for parking spots. And while a smartphone app can't make free parking spots magically appear, it can aid in the searching process. The Parker app isn't new to the iPhone, but its fou ...more
No Wi-Fi? No problem. All you need is a Bluetooth-enabled phone and laptop to surf the Web from anywhere.
At first, it seemed like a clever art installation housed on the web, but now we're not so sure... the Newstweek hack may indeed be legit. Earlier this year, Newstweek claimed to have developed a way to hack into webpages on a local Wi-Fi network using a homemade device that ...more