Null Byte is looking for moderators. More threats to computers exist every day. Not only do we have computer viruses and malware, but we have rootkits and other nasty pieces of code that can log your keyboard strokes or even add your computer to a botnet to attack other websi ...more
Anonymity is something that doesn't exist today. Everything you do in the world is tracked, from the purchases you make to surfing the internet—even taking pictures on your iPhone. Everything you have ever said and done on the internet is still there—somewhere. This is called ...more
Here at Null Byte, we've spoken a lot about securing and anonymizing traffic. This is a big deal. With all of today's business taking place electronically via computers, we need to be secure when on-the-go. A lot of businesses don't even train their employees to secure their c ...more
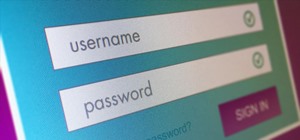
When Windows stores a password, it is done so by hashing the password in an LM hash and putting it in the Windows SAM file. In the scary moment that you lose your password, but don't want to pay some geek to have full root access to your computer, you need to recover it using ...more
Social networks like Facebook and Google+ are great for staying connected with family, friends and coworkers—even fans. But sharing and communicating with practically anyone in the digital realm has alienated us from most of the flesh-and-blood beings we see everyday—our neigh ...more
Welcome to part two in a series about steganography, the art of hiding things in plain sight. We are practicing steganography because it can be a useful skill if you don't have access to encryption software, or need a quick solution to make sure the sender and recipient are th ...more
There's a lot of talk going around about Google's new social network and how it's heavily influenced by Facebook, but truth be told, how could they build Google+ without taking a note or two from the world's most popular social network? One thing that's different (and better) ...more
There's an epidemic on the Internet, and the disease—Facebook. It's an addiction comparable to a hot cup of coffee in the morning or a soothing cigarette throughout the day—in worse case scenarios, a hit from the crack pipe. If you're on Facebook, you know what I'm talking abo ...more
Android devices are becoming more and more popular with each passing day, so why is it that Google has yet to design a software program that allows users to manage their music and video libraries on their computers? Apple's iTunes offers iPhone users an easy way to control the ...more
What's the next best thing to being an official scientist? Being a non-official one. A new website called Science for Citizens helps you find the science experiment of your dreams, hook up with the scientists involved, and actually take part in the experiment itself. Here are ...more
Your best friend's on Yahoo!, your daughter's on AIM, and now your co-worker wants to connect with you over Windows Live. Before you know it, your desktop is overflowing with buddy lists and message windows. Mismatched alert sounds are dinging and buzzing incessantly. Your com ...more
Type: Digital, Landscapes Theme: Incredible Landscapes, "Beyond the Mundane" Categories: Theme Deadline: Submissions close on February 28, 2011, midnight EST Deadline for mail-in entries is "received by", not postmark date. Eligibility: International, professional and ama ...more
Type: Digital, avian Theme: Bird portraits, "The Avian Persona", wild or in captivity Categories: Theme Deadline: Submissions close on January 31, 2011, midnight EST Deadline for mail-in entries is "received by", not postmark date. Eligibility: International, professional ...more
Get to know Congresswoman Lucille Roybal-Allard: Congresswoman Lucille Roybal-Allard was born in Bolye Heights, Los Angeles, County, California on June 12, 1941. She earned her B.A from California State University at Los Angeles in 1965. She is married to Edward T. Allard, II ...more
Researching the job market thoroughly and with the correct resources is important to the advancement of your career. Watching this video will establish how to research your career options, find information about companies and familiarize yourself with job titles that are a fit ...more
Have you ever noticed that whenever you setup your voicemail account after getting a new cell phone number, it asks you to create a security pin to access your voicemail from other phone lines? When you call your home or cell number from another phone, after a few rings your ...more
Here's something fun for the Null Byte community to do—a coding competition! This week, I wanted to get everyone involved by offering you all a nice library of possible program types to choose from and try to code. At the end of this competition, all of the submitted programs ...more
We'd like this to be one of the last HTS mission announcements, at least for now. As soon as Null Byte finds a server to play with (anyone want to donate one?), we are going to start doing root the box competitions, which is like king of the hill, except you have to hack a ser ...more
We're aiming for this to be one of the last HTS mission announcements, at least for now. As soon as Null Byte finds a server to play with, we are going to start doing root the box competitions, which is like king of the hill, except you have to hack a server and maintain acces ...more
Here's a nasty little Null Byte. An open redirect vulnerability was found in both Facebook and Google that could allow hackers to steal user credentials via phishing. This also potentially allows redirects to malicious sites that exploit other vulnerabilities in your OS or bro ...more
What is Google Dorking? Well, simply put, "Google Dorking" is just an efficient way to utilise keywords in order to perform very specific searches on a given subject. In this case, one would look for websites/servers that are vulnerable to attacks or are configured improperly ...more
File Transfer Protocol, or FTP, is a network protocol made for transferring files in a client and host fashion over a Transmission Control Protocol (TCP) network, such as the internet. FTP is integrated into most browsers, and you have probably used it before. It is a common w ...more
GRUB, or the GRand Unified Bootloader, is a program that installs to your Master Boot Record and controls what operating system you load at boot time. Normally, it is used for multi-boot systems. Multi-boots allow you to switch between operating systems installed on seperate d ...more
Welcome to part three in a series about steganography, the art of hiding things in plain sight. We are practicing steganography because it can be a useful skill if you don't have access to encryption software, or need a quick solution to make sure the sender and recipient are ...more
You'll see a lot of Linux action going down here at Null Byte. We use Linux for hacking-related stuff because it provides a more relaxed programming environment, making it easy to write exploits and tools. Linux has many features Windows is lacking, such as full control over t ...more
It's no secret. Professional video editors everywhere are irate at the newest edition to Apple's popular non-linear video editing software, Final Cut Pro X. As of right now, Final Cut Pro X has 503 five-star ratings in the Mac App Store. Not bad. But it also has 671 one-star r ...more
Do you know how you are perceived by your peers? In real life and online? In the physical world, you could be seen as intelligent, thoughtful and hard-working, but on the Web you could be looked at as irrational, selfish and slothful. There's just something about the Internet ...more
You've had a hard day at work and need to get out of the house, have a few drinks, but you don't want to go just anywhere—you want the right crowd and the right bar. For those nights, barhopping just isn't the answer, it's SceneTap. It's a new free mobile application coming s ...more
At first, it seemed like a clever art installation housed on the web, but now we're not so sure... the Newstweek hack may indeed be legit. Earlier this year, Newstweek claimed to have developed a way to hack into webpages on a local Wi-Fi network using a homemade device that ...more
Over the past few years, I have downloaded several third-party web browsers for the iPhone, iPod touch and iPad, and the one I have found most advanced and feature rich is Atomic Web. While many mobile browsers have their unique features, Atomic Web could well be considered th ...more
Attention all National SCRABBLE Association members: You know that newsletter that you get in your mailbox every month or two? That SCRABBLE News mailing from the NSA? Well, they're axing it. No more printed SCRABBLE News. No more ink on your fingertips. No more surprises in ...more
In my Wireshark article, we talked a little bit about packet sniffing, but we focused more on the underlying protocols and models. Now, I'd like to dive right back into Wireshark and start stealing packets. The filtering capabilities here are very comprehensive. You can filte ...more
This morning, I received a message from a friend who was reading a hack log, and she had some questions about the commands used. This got me thinking, as Linux has a ton of commands and some can be archaic, yet useful. We are going to go over everything you need to know to rea ...more
There are so many hackers around these days, and they are becoming very smart. So smart that they have successfully taken down many government websites. The most recent attack was on the Department of Justice (DOJ). To read about the history of these hackers, check out Wikiped ...more
Google+ has managed to double their user count from three months ago, now standing at over 90 million Google+ accounts created. But how did it get so many so quick? By tricking people who are signing up for Gmail or a regular Google account into setting up a Google+ account, t ...more
Haven't you ever wanted to live in a futuristic home? I think that homes are headed towards an era where they will be controlled by our computers and smartphones. No longer will you have to find your keys to unlock your door, or wait until you get home to monitor your security ...more
Can a free cloud-based video editor that lives in your browser replace iMovie? In three words: yes, it can. But whether you should use it instead of iMovie or an equivalent depends not on the functionality of the editor you need, as WeVideo can do what most of what iMovie doe ...more
Video Introduction to Edit on a Dime. Hey there, Interwebs and welcome to Edit on a Dime, your community for reviews, tutorials and news in the world of free and low cost creative tools. The purpose of this World is to make your video, audio and images look professional withou ...more
Kaplan University presents Visionary Voices, a series of interviews that chronicle our goals in regards to adult education and continuing education throughout your life. Kaplan University offers online degree programs designed to expand the way you think and help you develop b ...more
When Apple‘s iTunes was introduced back in 2001, it rekindled my interest and purchasing of music. I was so excited by the program that I immediately started converting all my rather large collection of CDs into MP3 tracks. I then sold off my CDs and remaining vinyl albums, an ...more
WonderHowTo is a how-to website made up of niche communities called Worlds, with topics ranging from Minecraft to science experiments to Scrabble and everything in-between. Check in every Wednesday evening for a roundup of user-run activities and how-to projects from the most ...more
Injection is an attack vector that involves breaking out of a data context and switching into a programming context through the use of special characters. These characters are significant to the interpreter being used, but not needed for the general user input being asked for. ...more
Amazingly, a lot of people I know haven't even heard of SOPA or PIPA. Now, every English-reading person with an internet connection will finally have those two four-letter acronyms emblazoned in their minds. For the entire day today, Wikipedia's English-language site will be i ...more
There are seemingly endless photography apps for the iPhone—it is perhaps one of the most popular arenas for application developers. We've covered a few in Giveaway Tuesdays, but nothing comprehensive. We would be remiss to omit the two most popular frontrunners—Hipstamatic ( ...more
Last week, I demonstrated how to go a little deeper into your Google+ profiles, photos, and introduced cross-posting. This week, I'm highlighting a bunch of different unofficial resources that have sprung up that will help improve your Google+ experience, and give you the late ...more
Okay, stop me if you've heard this one. You have a document that you want your co-workers' advice on. You attach said document onto a mass email. The first reply comes back with an edited version of the document. You begin to make changes, but another email comes in, with yet ...more
You've seen his explanation of a combination lock's inner workings. You'll never lose another game of Jenga, thanks to his winning wooden pistol. And nearly 4 million YouTube users have marveled at his wooden marble machine sculpture. He's Matthias Wandel, and he's accomplishe ...more
Spending five days with the game is enough to know it's not to my liking. Is it a horrible MMO? Yes, yes it is. There are better Free to Play MMOs launched years ago that are better than this. As a fan of the Final Fantasy series (I am currently playing and liking Final Fantas ...more
I want to write this article because in my childhood, I had experienced internet stalking which ultimately ended in physical stalking which then lead to several attempted abductions. I have now learned how to use the internet safely, who to communicate with and I've learned ho ...more
I have an absolutely wonderful time making projects and writing articles for all of you mad scientists! Today, I will bring you behind the scenes for a look at the workbench, tools, and software that make the Mad Science World possible. Above is my beautiful workbench! My who ...more
By Ethical Traveler As the world becomes ever more interconnected, being an ethical traveler becomes both easier and more urgent. Travelers today have access to far more information than we did even 10 years ago. We can observe–almost in real time–the impact that smart or sel ...more
STANDP'S CUSTOM DESKTOP "ASK NOT WHAT YOUR DESKTOP CAN DO FOR YOU...". http://standp-how-to-vidzzz.wonderhowto.com/corkboard/new-post/text/ Showing newest posts with label tips-n-trick. Show older posts DEC 07 Computer Backup If you have taken good care of your computer th ...more
SCRABBLE. I miss it. That idiosyncratic smell of cardboard, cheap wood and plastic that rushes out when I remove the box's cover. The instant gratification of unfolding the board into the sweet spot of the table, smoothing it out into the perfect receptacle for a heated battl ...more
Are you trying to access Facebook when you shouldn't? This video will help. Watch and learn how to use a proxy to get to blocked websites, like Facebook. Now you can go on Facebook and other websites anywhere, even at school.
Getting spammed or too many viruses? This trick will protect your computer from websites trying to access or corrupt it. Block Sites That are: Cookie Following Ads Virus Sites Pop Up Email Scams Pop Up Sites Follow along with the video and complete the steps on your own comp ...more
In this video tutorial, viewers learn how to turn off the system firewall without admin privileges. Begin by clicking on the Start menu and open he Run program. Type in "system.msc" and click OK. Scroll down the Services list and look for Windows Firewall. Double-click on it a ...more
This video tutorial from agseo presents how to unlock applications in Facebook social internet network. For more detailed information go to www.agseo.blogspot.comTo unblock Farmwille and other applications on Facebook social network login to your Facebook account.From top menu ...more
This fast tutorial will show viewers the basics of how to use Facebook for those who are new to using the website. After creating an account and logging into Facebook, you will see your homepage, which has most of the new information regarding your friends and their recent act ...more
The Dropbox utility can automatically sync your computer files with other devices each time you save them. In this tutorial, learn all of the steps you need to sync files with Dropbox. You Will Need • Internet access • Compatible mobile device • Dropbox software Step 1: In ...more
If you like to shop online then it is extremely helpful to have a PayPal account to safely make your online purchases. Help reduce your risk of identity theft by using protected methods like PayPal when your credit card information is involved. PayPal is a service that allows ...more