Since the release of the Samsung Galaxy Note 2, many of its features have been replicated by Android developers for other devices. The most popular feature, aside from Smart Rotation, on the Note 2 has been the multitasking multi-screen/multi-window feature, which allows you t ...more
In this article, you will learn how to move your Minecraft save files. This knowledge is very useful if you want to give your friends a copy of your offline world, or play on one of theirs. You can also make backups, or move your offline world to your server folder to play onl ...more
Start by clicking start and type regedit in the search box. Hit enter and when the screen opens go under hkey current user and click on control panel and then desktop. Under desktop go to menushowdelay. Under menushowdelay right click and then click modify. In the box that pop ...more
Welcome to this short and easy tutorial on hacking and DDosing (is that even a word I don't know) anyways lets get started First of all DDos means distributed denail of service attack, and yes i don't know what the HELL it means either. but anyway DDosing is where you spam a ...more
I've noticed that a few people using the crypto-currency, Bitcoin are having issues importing private keys to their Bitcoin wallet. This is easy to do and doesn't require anything other than your Bitcoin client/daemon (as of ver0.6.0 ) and the command line. Step 1: Setting Up ...more
Does your desktop look messy and unorganized?? Are there hundreds of icons in your desktop?? And it takes minutes to just find one?? Try this... See my messy desktop: With a few minutes and a couple of simple and easy steps, you can turn this into a classy and organized vie ...more
When I left off on our last hack, we had hacked into the ubiquitous Windows Server 2003 server by adding ourselves as a user to that system so that we can return undetected at any time. The problem with this approach is that a sysadmin who is on their toes will note that a new ...more
For all of the flak that Windows 8 received from desktop users, it certainly had some interesting and unique features. For instance, the "Charms" bar allowed you to easily access several key menus by simply hovering your mouse pointer in the top- or bottom-right corner of the ...more
Creating your own video tutorials - part 2. In this second part of our tutorial series on how to create your own video tutorial for free we will go into editing your video using Windows Movie Maker, which is provided free with all new versions of Windows. Read the first artic ...more
OneDrive, formerly known as SkyDrive, is a free online storage solution developed by Microsoft. If you're a fan of using cloud-based storage systems, then OneDrive offers you plenty of benefits. It's also heavily integrated into Windows 10, including the new File Explorer, in ...more
Microsoft's newest operating system, Windows 8, will hit stores everywhere on October 26th, and they hope this new version will shift the way we think about computers and their interfaces. In an effort to get as many early adopters as possible, Microsoft is even making their O ...more
More than likely, the first thing you noticed after booting up Windows 10 initially was a handful of new items in the taskbar across the bottom of your screen. Windows 8 users were probably glad to see the Start menu button back from the dead, but just to the right of that Win ...more
Today, Microsoft announced its Windows 10 Creators Update, adding the ability to scan objects in your world and bring them into the computer. With newly-announced inexpensive VR headsets and the HoloLens, you can enjoy those transplanted 3D objects in mixed and virtual reality ...more
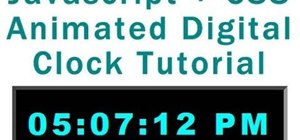
What time is it? It's a question that you'll find yourself asking a million more times throughout your life, but one that hardly goes unanswered. When you're on your phone or at your desktop, there is almost always some type of clock available to immediately give you the time ...more
Creating your own video tutorials. Over the last few years we have created a whole database of short video tutorials at helpvids.com - showing you how to use different programs. In this article I will explain some of the ways You can create your own video tutorials that you ...more
If your Safari browser is lagging when opening new tabs or windows on your Mac, there's an easy fix that will speed things back up to how they're supposed to be. In Google Chrome, when you open a new tab or window, you can start typing right away without having to click anywh ...more
Probably SSH is not as clean and fast as other useful tools like netcat, but it has some features which are very useful, and when you'll need them, here's how to behave with that huge amount of computers all over your house. Probably, you already know what SSH means, but for ...more
Now that the Surface Pro is out, you can game your heart out and get down with some serious Minecrafting. You're not just limited to downloading apps in the Windows Store anymore, like with the Surface RT. You can install a lot of Windows-compatible programs on the Surface Pro ...more
I've been using Windows 8 for a few months now, and it's definitely not as terrible as some people say, but it definitely isn't as revolutionary as the big wigs at Microsoft had hoped for. The new Metro interface is great to look at, but having to switch back and forth betwee ...more
Using either Winscp for Windows or Cyberduck for Mac you can SSH the files on your jailbroken iPhone, iPod Touch, or iPad from your computer. This will allow you to view the files on your iOS mobile device from your computer.
In this video tutorial, we learn how to use the greenpois0n jailbreak tool to jailbreak an Apple mobile device running iOS 4.1 from a Microsoft Windows (or GNU/Linux) PC. For detailed, step-by-step instructions, and to get started jailbreaking your own iOS 4.1 iPhone, iPod Tou ...more
Looking for a quick primer on how to resize a Windows Boot Camp partition? It's easy! So easy, in fact, that this home-computing how-to can present a complete, step-by-step overview of the process in a matter of a few minutes. For more information, including detailed instructi ...more
In this clip, you'll learn how to change the default color of highlighted text on a Windows Vista PC. With a little bit of know-how, it's easy. So easy, in fact, that this video guide can offer a complete overview of the process in a matter of a few minutes. For more informati ...more
In this clip, you'll learn how to install a 2G Bamboo Pen & Touch tablet on your Windows or Apple desktop or laptop computer. Happily, it's an easy process. So easy, in fact, that this video tutorial can present a complete, step-by-step overview of the process in just under fo ...more
In this clip, you'll learn what it takes to copy and transfer data from a corrupted Windows profile to a new profile. It's easy! So easy, in fact, that this home-computing how-to from the folks at Britec can present a complete overview of the process in just over five minutes. ...more
Need help figuring out how to troubleshoot and repair a Missing OS error on a Windows PC? It's easy! So easy, in fact, that this home-computing how-to from the folks at Britec can present a complete overview of the process in just over five minutes. For more information, inclu ...more
When people upgrade their windows few software don't run on new OS. How to fix the problem? Setting program compatibility solves the issue. Watch the video we made and submitted earlier in You tube. Video: .
Using a second monitor is great for multitasking, especially if you tend to max out your computer's brain power on tons of simultaneously running apps that you want to see, well, simultaneously. That second screen becomes more like a lifesaver. But, as I always say—with all t ...more
This year, Google released two Nexus phones to glowing reviews, and as we've grown to expect, the Android community wasted no time in coming up with a root method for both. In fact, legendary root developer Chainfire even devised an entirely new "systemless" method for rooting ...more
These days, there is hardly a place in America that doesn't have access to the internet. But with web usage fees and ridiculous cell phone provider contracts, sometimes it's still necessary to go a little DIY when it comes to staying connected. If you have a Windows 7 or 8 co ...more
Security researcher Nadim Kobeissi has discovered that the Windows 8 SmartScreen feature, meant to screen downloads for malicious software, actually reports the data about which applications users are installing to Microsoft. He also says that "the Microsoft server is configur ...more
Google Play Music has been my go-to music service ever since its release. The free cloud storage for 50,000 songs and full access to Songza-powered radio stations make it a great music app, even without the $10/month streaming service. The only downside is that the desktop ex ...more
A lot of computers come with a ton of pre-installed software from the manufacturer, some of which you need and some of which you could most certainly live without. And over time, you may have downloaded and installed a bunch of programs and apps that you probably can't even re ...more
There is no such thing as too much space when it comes to our smartphones. Space is the great equalizer of all things. No matter how many awesome features a device has, the amount of storage space available will always be a determining factor. Be it music, apps or photos, it's ...more
Whenever something goes wrong with your iPhone, or whenever you want to downgrade from an iOS beta back to the regular iOS release, you can restore your iPhone to your last saved state. Restoring to an iCloud backup is great but won't work in all situations. Plus, if you saved ...more
Just like the recently rediscovered Star Wars ruins in the Tunisian desert, there are tons of hidden treasures in your Samsung Galaxy Note 2 just waiting to be unearthed. Rooting enables you to install custom ROMs, exclusive features from other devices, add Wi-Fi tethering, o ...more
Just a little desktop comparison. Post your gorgeous desktops too! Any OS :D.
Problem with your primary hard drive? This clip provides some helpful advice on how to resolve this common and frustrating problem. It's simple! So simple, in fact, that this home-computing how-to from the folks at Britec can present a complete overview of the process in just ...more
In this clip, you'll learn how to use the AnyToISO disc image converter to convert BIN, CDI, NRG, IMG, DEB and DMG files to ISO files. It's easy! So easy, in fact, that this home-computing how-to from the folks at Britec can present a complete overview of the process in just o ...more
Microsoft's updated web browser, Internet Explorer 10, has only been out for a few days on Windows 8, and there is already a storm of controversy surrounding its launch. Microsoft has pegged IE10 as one of the fastest and safest internet browsers on the market. In an effort t ...more
USE WINDOWS 7 ULTIMATE x64 w/ all the latest updates always OF COURSE AND... USE THE ASTON 2 SHELL REPLACEMENT, MENU, DESKTOP, W/ THEMES... USE EASEUS DATA RECOVERY WIZARD V5+... USE FROSTWIRE P2P FILE SHARING CLIENT... USE INCREDIMAIL 2 (LATEST)... USE SAFARI (ONE OF THE ...more
It's remarkable that a gaming device (from Microsoft, no less) designed for geeky gamers has incited broad innovation in medicine and robotics. But that Kinect has captured the imagination of hackers-with-MBAs-in-mind is downright amazing. Below, six videos demonstrating a va ...more
This is an intermediate guide on how to easily fix or retrieve data from a bad hard drive. What we're trying to do: 1. Fix a hard drive with a corruption problem (i.e., blue screen) or that is full of viruses to the point of being inoperable. 2. Retrieve data from a hard dr ...more
Welcome back, my hacker apprentices! Metasploit framework is an incredible hacking and pentesting tool that every hacker worth their salt should be conversant and capable on. In a previous post, I had provided you a cheat sheet of meterpreter commands. These commands are ess ...more
This tutorial was written with Windows 7 in mind, but the principle applies to all versions starting from 7. User Account Control (UAC) Processes in Windows run at different levels of integrity, representing the different amounts of "trust" they have to interact with the com ...more
If you've received the "hal.dll is missing or corrupt" error message from your Windows machine, then you're in luck! This video will show you how to correct that problem with the Recovery Console tool that comes with the Windows 2000 and XP CDs. Using the Windows Recovery Cons ...more
Did you know Kali 1.0.8? You probably did, and you probably know about the EFI boot option that has been added. That's a very interesting new feature because it allows Kali to be easily booted on Mac too, and every EFI-supported device. First three preview lines gone? As alw ...more
Warnings INTERNET EXPLORER IS USED BY MANY PROGRAMS BECAUSE IT IS ALWAYS THERE, AND MANY PROGRAMS LOAD IT EVEN IF YOU HAVE YOUR DEFAULT AS SOMETHING ELSE, I KNOW IT CAN BE A PAIN, BUT IT'S A FACT AND WON'T BE GOING AWAY, JUST LIKE IE WON'T BE GOING AWAY FORE IF YOU UNINSTALL ...more
As the world goes into a frenzy over the latest strain of WannaCry ransomware, it might be a good time to remember to update all your devices. Yes, those little reminders your phone and computer throw at you every now and then to update your junk can be really annoying, but no ...more
Remote desktop is a windows feature which can be used to access a windows computer from an other windows computer over the internet. Note that to access a windows computer using remote desktop the computer must run on Windows Professional or Ultimate version. Remote desktop do ...more
Welcome back, my greenhorn hackers! A few years back, Microsoft implicitly recognized the superiority of the Linux terminal over the GUI-based operating system by developing PowerShell. Since Windows 7, every Windows operating system has had PowerShell installed by default, a ...more
All of my hacks up to this point have been operating system hacks. In other words, we have exploited a vulnerability usually in an operating system service (SMB, RPC, etc.) that all allow us to install a command shell or other code in the target system. As I have mentioned nu ...more
As an added functionality to the S Pen, the Pen Window enables you to create floating application windows on your Samsung Galaxy Note 3—a tool that's extremely useful when it comes to multitasking. However, there's always room for improvement. In today's softModder guide, I' ...more
The Shadow Brokers, a hacker group known for its dump of NSA hacking tools in 2016, has just leaked their remaining set of data which implies that the NSA compromised SWIFT, the global provider of secure financial services, to spy on banks in the Middle East. The hackers have ...more
Welcome back, my hacker trainees! A number of you have written me regarding which operating system is best for hacking. I'll start by saying that nearly every professional and expert hacker uses Linux or Unix. Although some hacks can be done with Windows and Mac OS, nearly al ...more
This video tutorial shows you how to make your Vista look like Mac Os X To make Windows Vista look like a Mac Os X using Vista Glazz Application: * Open a internet browser using any search engine, then download the Vista Glazz application. * Install it and in the start menu s ...more
Apple's codec for photos and videos in iOS 11, HEVC (High-Efficiency Video Coding), as well as the container, HEIF (High-Efficiency Image File Format), result in a reduction in size for pictures and movies without sacrificing quality. Seems like a win-win situation, but Window ...more
Need to clear you cache? This guide details how on any web browser (Chrome, Internet Explorer, Firefox, Opera, Safari, Internet, and Dolphin) for any platform (Windows, Mac OS X, iOS, and Android). What Is the Cache Exactly? The web cache stores certain information (HTML page ...more
The latest Star Wars movie, Solo: A Star Wars Story, has grossed almost $350 million worldwide during its first month in theaters. This is a good opportunity to discuss how hackers can use media hype (in this case, Hollywood movie hype) to disarm an unsuspecting Windows user i ...more
In this tutorial I am going to show you how to create an undetectable Meterpreter Trojan using a Domain name. I have taken a few guides/tutorials and built it into one. The first part is creating the DNS Payload. The second part is creating the Executable file. Part 3 is using ...more