If we were to assign a theme for the 2019 edition of the Next Reality 30 (NR30), it might be something along the lines of, "What have you done for me lately?" Many of the top names in the industry from the 2018 edition remain the same, but their positions have shuffled. The p ...more
Despite newer phones having larger batteries, after a few months, my battery life drops significantly. I started researching solutions after my third phone. No matter who I asked, the most recommended solution was always Greenify. And unlike other solutions, you don't need roo ...more
When Stardew Valley launched back in 2016 on Steam for PC, it was instantly deemed a success for steering the RPG farming simulator genre back on the right track. Before its release, we hadn't seen too much in this particular field of games that caught the eye of the general p ...more
So after being teased last Christmas with an email promising that the Meta 2 was shipping, nearly a year later, we finally have one of the units that we ordered. Without a moment's hesitation, I tore the package open, set the device up, and started working with it. To me, the ...more
To really personalize your HTC 10, you'll need to be rooted — but that can't happen unless you unlock your bootloader. Thankfully, HTC has made it relatively easy to unlock the bootloader on their 2016 flagship. Unlocking your bootloader will make it a breeze to install TWRP, ...more
Oftentimes, seemingly insignificant, nondescript features have the most impact on enhancing our Android's usability. A great example is Nougat's inclusion of customizable Quick Settings tiles, which adds greatly to the user experience by letting individuals tailor their expand ...more
Up until now, enabling full-time Immersive Mode on an Android device has been a tedious task which required you to run individual ADB commands each time you wanted to toggle it on or off. This was a shame, too, since Immersive Mode helps reclaim lots of screen real estate by a ...more
One of the biggest features to come out with Android O was the addition of a new System UI Tuner submenu that lets you customize the navigation bar at the bottom of your phone's screen. But as it turns out, this same feature can be enabled on devices running Android Nougat, ev ...more
Making a NANDroid backup can save you from all sorts of flashing-related mishaps and accidents. Bootloops, SystemUI crashes, accidental wipes, bad ZIPs, or a dozen other possibilities—there's almost no condition in which a NANDroid is unable to correct problems with your devic ...more
We haven't had a working jailbreak method since October of last year, and that only worked for about a month until iOS 9.2 came out and shut down the loophole it was using. So all of those cool Cydia tweaks have been out of the question for quite a while now, unless you downgr ...more
Microsoft's HoloLens comes with helpful features for capturing video and photos, but sharing whatever you record isn't as straightforward as you might expect. So here are the many ways to get your media off the device to share with the world. Step 1: Take a Picture or Record ...more
Samsung's 2016 flagship devices are some of the most beautiful, powerful smartphones ever made. And amazingly enough, thanks to legendary root developer Chainfire, the Samsung Galaxy S7 and Galaxy S7 edge are about to get even more powerful. Don't Miss: Android Root Explaine ...more
If you use a wireless mouse or keyboard, you could be leaving yourself open to attacks from hackers. Researchers at Bastille had discovered in January 2016 that attackers could make use of a cheap $15 antenna to sneak into your computer through a wireless mouse or keyboard don ...more
Welcome back, my neophyte hackers! Metasploit is such a powerful tool that I can only scratch the surface of its capabilities here. As it has developed over the years, it is now possible to use Metasploit for nearly everything from recon to post exploitation to covering your ...more
Welcome back, my novice hackers! More and more, the world is turning to and adopting the smartphone platform as the digital device of choice. People are not only using smartphones for voice communication, but also web services, email, SMS, chatting, social networking, photogr ...more
I see many people posting the same thing on the internet. "How do I become a hacker? Where do I commence?" The definition of 'Hacker' varies from person to person. Personally, I call it someone who relishes fiddling with technology, one who has the mind to manipulate technolo ...more
At last, what you all finally waited for! Hi! Fire Crackers, Welcome to my 7th post (Part-3), this tutorial will explain about some situations and how to make the Victim's Life like Hell! And fill his system with Malware. #1 Situation: After Exploiting... Go ahead and explo ...more
Welcome back, my novice hackers! In this continuing series on Metasploit basics, let's next look at a module that many aspiring hackers find useful—autopwn. Generally, when we are trying to hack a target, we want to know as much as possible about the target through reconnais ...more
Welcome back, my tenderfoot hackers! A short while ago, I started a new series called "How to Spy on Anyone." The idea behind this series is that computer hacking is increasingly being used in espionage and cyber warfare, as well as by private detectives and law enforcement t ...more
A recent update to Google Chrome replaced the colored avatar menu in the top-left (Windows) or top-right (Mac) corner of the browser that let you easily switch from profile to profile with a plain gray button that simply names what profile you're in. I use different user prof ...more
Welcome back, my budding hackers! One of the keys to being successful as a hacker, pentester, or cyber warrior is the ability to find vulnerabilities or flaws in the target system, which are what we exploit when we hack. We have looked at several ways to do that including var ...more
Welcome back, my hacker novitiates! In previous guides, we have used one of the most powerful hacking platforms on the planet, Metasploit, to perform numerous hacks. They ranged from exploiting Windows XP and Windows 7/8 vulnerabilities, to installing a keylogger and turning ...more
Spiders are common pests that typically prefer to live outdoors. However, insects and warmth will eventually attract them into our houses. They like to spin their webs in corners, crevices and unused areas of your house. Most species are harmless and even act as a natural repe ...more
Okay, so you're rooted and need to return your Nexus 5 to its stock firmware. Whether it's because you need to send your phone in to the manufacturer to fix a defect or you just want to use the device's over-the-air updating feature, unrooting and returning your Nexus 5 back t ...more
Welcome back, my rookie hackers! The more we know about a system or network, the better our chances of owning it and not leaving a trace for investigators to follow. One of the often overlooked sources for information is the Simple Network Management Protocol (SNMP). Many roo ...more
Welcome back, my hacker apprentices! I recently began a new series on digital forensics to show aspiring hackers what the forensic investigator can do and see while investigating a cyber attack. This is the second installment in that series and will focus upon network forensi ...more
Welcome back, my rookie hackers! A short while back, I began a new series on database hacking, and now it's time to continue and extend your education in that field. As you know, the database contains all of the most valuable info for the hacker, including personally identifi ...more
Welcome back, my fledgling hackers! It's been awhile since we did a Metasploit tutorial, and several of you have pleaded with me for more. I couldn't be happier to oblige, as it's my favorite tool. For the next several weeks, I'll intersperse some new guides that'll help expa ...more
The NSA's massive internet spying efforts will continue. In President Obama's latest press conference, he went public to (in so many words) say that the NSA's spying efforts will continue uninterrupted. This, coming just weeks after the Amash Amendment which would have defund ...more
Welcome back, my budding hackers! Previous to this tutorial, we've focused mostly on hacking the target system. If we're successful in owning the target system, we'll then want to make certain that the system administrator doesn't know we were there, and that he or she cannot ...more
In my first tutorial on Linux basics, I discussed the importance of hackers using Linux and the structure of the directory system. We also looked briefly at the cd command. In this second Linux guide, I'll spend a bit more time with changing directories, listing directories, c ...more
Smartphones are great. They help you keep in touch with your loved ones and stay up to date on what's going on in the world. The problem is that like everything else that's useful, they cost money to use, and between calling, texting, and data plans, it can get really expensiv ...more
MAC addresses (not to be confused with Macs) are unique identifiers assigned to network devices in order to access the internet. Hotels use these Mac addresses in order to check if a registered patron has agreed to their terms and conditions, how much bandwidth is being consum ...more
Pixels don't have a "Download Mode" like Samsung Galaxy phones, so there's not an easy, point-and-click way to send firmware files and low-level commands from your computer. What they do have is an even more powerful tool: Fastboot Mode. Also known as Bootloader Mode, this is ...more
In a surprising twist of expectation management, Magic Leap managed to not only ship but deliver the Magic Leap One I ordered on Wednesday by 4 p.m. PT on the same day. After spending about an hour with the headset running through set up and poking around its UI and a couple ...more
If you're using a mobile device, it's a pretty safe bet that your apps are sending lots of information back and forth from their servers. To make sure there is no inappropriate data collection going on, it's worth setting up a web proxy to spy on this traffic, so you know exac ...more
Virtual private networks, or VPNs, are popular for helping you stay anonymous online by changing your IP address, encrypting traffic, and hiding your location. However, common IoT devices, media players, and smart TVs are hard to connect to a VPN, but we have a solution: Turn ...more
Throughout this NR50 series, we have talked about the incredible growth the augmented and mixed reality space has seen in the last year. More devices, software, developers, and use-cases seem to arrive daily. For this growth to have occurred, it took the work of many people, f ...more
A new technological movement without the technology itself is just an idea sitting and waiting. Once the technology is present in the equation, movement forward can begin. This is how many of us see the head-mounted displays (HMDs) and smartglasses that have recently entered t ...more
Hello ladies and gentlemen, I'm back with another informative(hopefully) article for you all. Once again I would like to apologize for my absence for about a week or so. I have some stuff going on with my life and university and I haven't found enough time to make a fully in-d ...more
Brand loyalty is one of the main factors behind our decision to choose a particular mobile device, but it doesn't have to be the entire equation. Educated consumers know that certain devices simply fit their budget and usage better than others, which means you can't always let ...more
The older I get, the more my Friday nights involve watching Netflix at home with a bottle of Maker's Mark and a box of Oreos. Netflix is a big part of my life, and I'm not alone. YouTube and Netflix make up over 50% of all activity on the Internet, so it might be worth your ti ...more
The Droid Bionic was rooted the same day it came out with the one click method used to root the Droid 3. This tutorial will walk you through the process of rooting Motorola's Android device so that you can unlock the full potential of Verizon Wireless's flagship device. Full ...more
Spice up your computer's appearance with a cool looking screensaver like PolarClock. PolarClock works on OSX or Windows and replaces a dull screensaver with one that doubles as a clock. Now when you step away from your mouse and keyboard you can keep track of the time in style.
Nowadays, there's a mobile app for just about everything—but that doesn't mean it should be on your smartphone. Not diggin' what SPB Shell 3D did to your home screen? Accidentally purchased Angry Sperms instead of Angry Birds? Want to try out the upcoming Smuggle Truck without ...more
One of the most annoying of the many annoying types of errors on Windows computers is when you computer won't recognize parts that have always been a part of it, like the drives or keyboard. If your computer has stopped recognizing your CD or DVD disc drive, watch this video. ...more
Interested in using Cinebench to benchmark your Microsoft Windows or Apple Mac OS X computer? You've come to the right place. This home-computing how-to from the Greyscale Gorilla will teach you everything you'll need to know. For detailed, step-by-step instructions on how to ...more
You've had a massive hard disk failure.. ...in your PC or laptop and like a large number of people who think it will never happen to them...you did not have a backup of those 2000+ family pictures, those hundred of important Word documents, those family videos that you downlo ...more
Want to mod your HTC HD2 Microsoft Windows smartphone to use wireless charging—without breaking your warantee in the process? It can be done! And quite easily at that. For complete details, and to get started modding your own HD2 phone to work with wireless chargers, watch thi ...more
If eyes are the windows to your soul then eyebrows are the gatekeepers. Keep your peepers' bodyguards in tip top shape by spic and spanning them with a perfect shape and filling them in with brow powder. Watch this makeup tutorial by celebrity makeup artist Kandee Johnson to ...more
Interested in taking professional-caliber portraits but haven't time (or money) for a bulky light rig? Great results can be had by taking advantage of the available light from windows. This photographer's guide offers a number of pointers for you shooters out there. For more i ...more
If you have a set of windows in your home that are always facing the sun, then that can be a problem. Not only can it damage any furniture that may be in the way, but it can raise the tempature in your room causing you to use more energy to cool it down. In this helpful conse ...more
In this tutorial, learn all about Swype. Swype is an app that you can add to your cell phone to make texting and e-mailing lightening fast. Say goodbye to tap texting - with Swype you just let your finger glide on the keyboard until it creates your desired word. Check out this ...more
If you're using Adobe Dreamweaver CS4, the Spry Ajax framework menus make creating dynamic drop-down windows a snap. Whether you're new to Adobe's popular WISYWIG HTML editor or a seasoned web development professional just looking to better acquaint yourself with the CS4 workf ...more
Adobe Dreamweaver CS4 is one of the most powerful tools for creating websites today. This video teaches you how to center your swl file on your website using an xhtml workaround and css. It will look much more professional as a result, since it won't be out of alignment when v ...more
This video guide will help you to fold your own hanging origami crane ornaments to hang on a Christmas tree or in your windows. Perfect for beginners. For more information, including a step-by-step overview of the folding process, as well as to get started making your own fold ...more
Converting file formats seems to stump a lot of people, so if you're coming here clueless as to how to convert an AVI to DVD, don't feel alone. In this video, learn how to turn an .AVI file to DVD using Windows Live Movie Maker easily and for free.
This tutorial on the companion Tech Ease for Mac site explains what podcasting is and shows you how to subscribe to podcasts using iTunes, a free program from Apple. Since iTunes is cross-platform, the steps shown in the movie will work on Windows as well. This movie defines p ...more
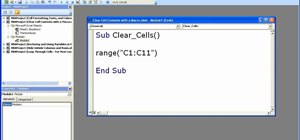
n this ASP.Net video lesson, you will explore the various ASP.NET 2.0 server controls available in Visual Web Developer 2005 Express Edition. In addition, you will begin to get familiar with the windows in VWD.
In this video tutorial, you will see how to use Tooble, free from tooble.tv, to get videos from YouTube into iTunes, then onto your iPod, iTouch, or iPhone. Unfortunately, there's no Windows version for you, it's just for Mac. But don't let that discourage you, there developin ...more