One of Android's biggest strengths is its ability to interact with other operating systems. When you plug your phone into your Windows PC, you instantly see all of the files it holds—and all it takes is a simple syncing app to do the same with Mac. To top that off, apps like P ...more
As most of you know, I am a strong advocate for using Linux for hacking. In fact, I would go so far as to say that you cannot be a hacker without knowing Linux well. I laid out various reasons for this in my "Why Every Hacker Should Know & Use Linux" article, and I even have a ...more
Welcome back, my tenderfoot hackers! One key area on the minds of all hackers is how to evade security devices such as an intrusion detection system (IDS) or antivirus (AV) software. This is not an issue if you create your own zero-day exploit, or capture someone else's zero- ...more
Hello, everyone! Many of you don't even know about my existence here on Null Byte, so I thought of contributing something rather interesting. Recently, someone asked how to make your own "Bad USB," and I promised to make a how-to on this topic. In addition, it would be nice t ...more
Welcome back, my hacker novitiates! Eluding and evading antivirus software and intrusion detection systems is one of the most critical tasks of the hacker. As soon as a new exploit is developed and discovered, the AV and IDS developers build a signature for the attack, which ...more
Welcome back, my novice hackers! We've done a number of tutorials using one of my favorite hacking tools, Metasploit. In each of them, we've used the msfconsole, which can be reached through either the menu system or through simply typing "msfconsole" from the terminal. This ...more
Restrictions are inconvenient, and for this reason I've sought out softmods that loosen the constraints for many of the features on my smartphone. Things like adding favorite apps to the Pen Window drawer or choosing any app for Multi Window mode are now must-haves on my Samsu ...more
Welcome back, my neophyte hackers! Have you ever had a neighbor that you're certain is up to no good? Maybe you've seen him moving packages in and out at all hours of the night? Maybe you've seen people go into his home and never come out? He seems like a creep and sometimes ...more
You can easily lock any folder on your Windows computer with a simple Notepad hack. By creating a batch file, you can hide a folder and require a password be entered before it becomes visible and accessible. This is a great tool for locking sensitive information, like pictures ...more
Who am I? First let me introduce myself. I am Th3skYf0x, an -well lets call it experienced- hacker and i recently found this site and right after that i found this Null Byte "world" soo i thought... Why not teaching instead of doing nothing with my knowledge. Let me get one ...more
In this Windows 8 Tutorial you will learn how to add different languages to your Keyboard. This is very beneficial especially with the world becoming more global and connected. Once you add additional languages to your keyboard you will have the option to switch between those ...more
Welcome back, my newbie hackers! Hackers often are associated with clandestine and illegal activity, but that is not necessarily always the case. Hackers are increasingly being used and employed for law enforcement, national security, and other legitimate purposes. In this in ...more
Like a computer, your brain can store and process large amounts of information. It can remember names, solve math problems, and save tips that you might need at a later time. Unlike a brain, though, computers tend to collect information that might not be important. Not only t ...more
Microsoft's first venture into the tablet market, the Surface RT, combines many of the capabilities of a normal Windows 8 laptop into a super compact tablet, whose super-thin touch cover and kickstand can transform it into a functional mini-laptop, small and light enough to go ...more
With an ordinary birthday card, we can introduce a physical device which contains malicious files into someone's home and deceive them into inserting the device into a computer. In my last series, we used a Post-it note to trick a neighbor into visiting a website that we cont ...more
Like last year's beta release of Android Pie, Google has allowed the Android Q Developer Previews to support some non-Pixel devices. Announced at Google I/O 2019, there are 15 non-Pixel smartphones eligible for the Android 10 Beta, including 2017's Essential PH-1. With a few ...more
To please those of us who love to mod and root our Androids, OnePlus has made both the OnePlus 5 and 5T relatively easy to customize — so much so that the 5T topped our list for the best phones for rooting. Unfortunately, unlocking the bootloader and using root to modify the f ...more
If I were to lose access to the entire internet for the rest of my life, one of the websites I would miss the most would have to be Wikipedia. Wikipedia has ended countless arguments, informed me of how old and single some of my favorite actresses are, and helped me brush up o ...more
For those not used to it, working from home can be a difficult transition. Everything around you can be a distraction, and distance from your boss and coworkers means less pressure and incentive to get things done. So it's not surprising to see a major drop in productivity dur ...more
Although the Galaxy Note 9 is an amazing phone, many members of the Android community won't even look at it. This isn't just because of the Samsung Experience skin, but the large amount of bloatware that comes with this device. However, with a little work, you can remove all o ...more
Although the Essential PH-1 got off to a rocky start, thanks to steady updates, it has slowly become one of the best Android phones to come out in recent years. For $499, the Essential Phone is a cheaper Pixel, receiving updates almost as soon as the Pixel lineup does. What's ...more
If you use Google Chrome as your default desktop/laptop browser, then Chrome OS will be pretty easy to get up and running if transitioning from Windows or macOS. Google has created an operating system that is fast, lightweight, and versatile enough to be adopted by pros and no ...more
Welcome back, my rookie hackers! Now that nearly everyone and everyplace has a computer, you can use those remote computers for some good old "cloak and dagger" spying. No longer is spying something that only the CIA, NSA, KGB, and other intelligence agencies can do—you can l ...more
Welcome back, my novice hackers! There are SOOOO many ways to hack a system or network, which means you need to think creatively in order to be successful. Many novice hackers focus way too much energy on cracking passwords (which should be a last resort unless you have spec ...more
Dropbox continues to make headlines with their recent programming blunder which left the accounts of its 25 million customers wide open during a four-hour time span. During the duration, anyone in the world could access any Dropbox profile by typing in any password. And seeing ...more
With all the web applications out on the internet today, and especially the ones built and configured by novices, it's easy to find vulnerabilities. Some are more perilous than others, but the consequences of even the slightest breach can be tremendous in the hands of a skille ...more
If you read the reviews on Google's Pixel C, you'll notice one big complaint about the tablet/laptop—most reviewers feel that Android simply isn't ready to be used as a desktop OS. The developers at Jide felt the same way, so they set out to make a custom version of Android wi ...more
Google has already started to roll out the over-the-air update of Android 5.0 Lollipop to older Nexus series phones and tablets, but chances are it will take a long time for the OTA to hit your device. If you don't want to wait, you can manually install Lollipop right now if ...more
Welcome back, my fledgling hackers! If you're like most aspiring hackers, at one time or another you've probably spent too much time playing Call of Duty and not enough time preparing for your final exams. So for today, we'll look at how to break into your school's server to ...more
Google Reader is soon to be no more. Yesterday, the company announced that the service will be shutting down as of July 1, 2013, as part of Google's second "Spring Cleaning." Predictably, users are freaking out—the process of backing up and exporting all your feeds can take a ...more
Today I will show you how to create a simple keylogger in Visual C# Sharp, which will start up hidden from view, and record anything the user types on the keybord, then save it into a text file. Great if you share a PC and want to track what someone else is writing. You Will ...more
USE WINDOWS 7 ULTIMATE x64 w/ all the latest updates always OF COURSE AND... USE THE ASTON 2 SHELL REPLACEMENT, MENU, DESKTOP, W/ THEMES... USE EASEUS DATA RECOVERY WIZARD V5+... USE FROSTWIRE P2P FILE SHARING CLIENT... USE INCREDIMAIL 2 (LATEST)... USE SAFARI (ONE OF THE ...more
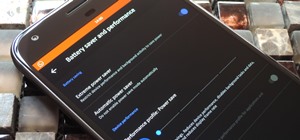
Because of the way Android is laid out, you automatically lose a portion of the top and bottom of your screen thanks to the status and navigation bars. The thing is, you don't always need the navigation buttons. By hiding them, you can enjoy more of your Galaxy S10's big, beau ...more
Even though your phone has a built-in media player, it's got nothing on VLC. The popular third-party video player supports virtually every codec and file format, and even better, you can use it to stream movies, shows, and other video files from your computer to your phone. I ...more
Don't let the lack of owning a HoloLens stop you from joining in on the fun of creating software in this exciting new space. The HoloLens Emulator offers a solution for everyone that wants to explore Windows Holographic development. At $3,000, the HoloLens can be cost-prohibi ...more
You may not know what HTTP is exactly, but you definitely know that every single website you visit starts with it. Without the Hypertext Transfer Protocol, there'd be no easy way to view all the text, media, and data that you're able to see online. However, all communication b ...more
Winter is already here, and when Jack Frost is nipping at your nose, he tends to nip on your wallet, too. That's right—between holiday parties, gift-giving, heating bills, and all the required snow and wet-weather gear you need, the winter months can get pretty expensive. So ...more
Mac OS X has finally added a way to use two apps side by side in full screen mode, à la Microsoft's Windows Snap. But since it's only available in 10.11 El Capitan right now, those of us with older systems will have to wait until the El Capitan Public Preview or final build is ...more
Your best friend's on Yahoo!, your daughter's on AIM, and now your co-worker wants to connect with you over Windows Live. Before you know it, your desktop is overflowing with buddy lists and message windows. Mismatched alert sounds are dinging and buzzing incessantly. Your com ...more
This tutorial describes the procedure to remove autorun.inf and boot.com virus. This virus is commonly called as resycled/boot.com virus, which could damage the system files and may steal important information from the system.This can be removed by any malware / spyware remove ...more
With HoloLens 2 (hopefully) just around the corner, Microsoft has announced that it will no longer be providing any major operating system updates to the original HoloLens. The HoloLens 1 was released back in 2016, which feels a bit like ancient history in the ever-evolving w ...more
You need a good microphone on your computer in order to make audio recordings, voice chat, or use speech recognition. However, not every computer comes with a built-in mic, and not every built-in mic works great. You can purchase a cheap computer microphone on Amazon for as l ...more
Cortana, Microsoft's personal assistant for its Windows Phones and Windows 10, will soon be released for Android. That is, officially released. It's hard to keep a good thing locked away, and to that end, Cortana for Android has been leaked, thanks to APK Mirror. Don't Miss: ...more
Presented by Apartments.com When looking for a new apartment, it's hard not to notice the improvements (on large and small scale) needed prior to moving in. While your landlord may be taking care of new carpeting, cleaning the central air vents, and fresh paint on the walls, ...more
Welcome back, my fledgling hackers! There's an evil dictator hellbent on destroying the world, and in one of our last hacks, we successfully compromised his computer and saved the world from nuclear annihilation. Then, we covered our tracks so no one would know what we did, a ...more
This is, by far, the easiest way to root your Android phone, and it's even got its own name— the "SuperOneClick" method. This is a universal technique that applies to most Android-based smartphones (minus the HTC Evo and T-Mobile G2/Vision). TheUnlockr shows you the secret beh ...more
There are lots of Linux distros out there. Normally, you'll have to download the ISO and then burn the image onto a CD. But nowadays, it's easier and cheap to install it on a USB drive. A multiplatform program called UNetbootin can install a variety of Linux distros on a USB. ...more
Steve Lee Ignacio explains the procedure to be followed to build a Bart PE Professional Rescue CD. He says that the basic requirements for completing this process is a Windows XP Pro or Home CD, a Bart PE builder, a Windows Computer, a program to burn .ISO files and a CD burne ...more
Keep your possessions safe from thieves with these tips. You Will Need * Motion detector lights * Locks * A locksmith * A security alarm system * A safety deposit box or home safe * An engraving pen * A trusted neighbor * Bolts or wooden dowels (optional) Step 1: Eliminate bu ...more
Burglary is common, but is also quite preventable with these tactics. You Will Need * A dog * Motion detector lights * A security system * Strong doors * Impact-resistant doors and windows * Neighborliness * A wooden dowel Step 1: Get a dog Get a dog. Even small dogs will bar ...more
New to Ubuntu Linux? This computer operating system could be a bit tricky for beginners, but fret not, help is here. Check out this video tutorial on how to install Zekr (Qur'an Study Tool) on Ubuntu Linux, Windows, and Mac OS. Zekr is an open platform Quran study tool for si ...more
Board up a window for protection against strong storms and hurricanes. Learn how to board up a window. You Will Need: * Exterior-grade plywood, at least 5/8 of an inch thick * Drill * Drill bits * Hammer * Lag screws and plastic-coated permanent anchors (for wood-framed hous ...more
Microsoft has informed HoloLens users that the company will begin rolling out a mandatory update for HoloLens as part of its Windows 10 October 2018 release that brings a number of new features and quality-of-life improvements to the headset. The update's new features are hea ...more
For modders, there are few tools more important than TWRP. TeamWin's custom recovery makes flashing mods like Magisk, Xposed, and custom ROMs incredibly easy, and it lets you root your phone at the press of a button. On top of that, it can make complete backups of your phone i ...more
A new repository appeared in Microsoft's GitHub account a few months ago for a project called HoloJS. For those JavaScript developers out there that have been wanting to make HoloLens apps, this one's for you. Microsoft has been surprising the development world recently by fu ...more
When it comes to modifying Android, the single, most powerful tool available is TWRP custom recovery. It's even more capable than simple root access when it comes to changing the look and feel of your software, and you can even use TWRP to root your device in a few simple step ...more
The latest beta of the popular open-source media player VLC just hit the Windows Store, which means it not only runs on Windows 10 and Xbox One, but the HoloLens as well. VLC isn't new to Windows, obviously, but the beta released in the Windows Store offers a slew of special ...more
It seems like every day now that we see a new headline on a cyber security breach. These headlines usually involve millions of records being stolen from some large financial institution or retailer. What doesn't reach the headlines are the many individual breaches that happen ...more
Finding an instrumental or karaoke version of a song can be pretty easy unless you're dealing with a song that isn't popular. That leaves you with just the full version of the song, complete with vocals. So how do you convert it into an instrumental or karaoke track? Accompan ...more
Root, TWRP, Xposed, Magisk, custom ROMs — before you can have any of these, the first thing you should do is unlock your bootloader. Thankfully, the Pixel 2 and Pixel 2 XL are some of the most modder-friendly phones out there, so you only need to send a single fastboot command ...more