The newest version of Apple's mobile operating system, iOS 10, has been out for about a month now. But like every year beforehand, some of you who updated will not be happy with the latest and "greatest" iOS version. If that happens to be the case for you, you've still got a ...more
Gmail has been the email standard for quite some time now, and for good reason: it's a free service provided by one of the largest tech companies in the world that offers users an amazing feature set to manage, send, and keep track of all their important emails. However, all ...more
Most of you lot would be aware what WPA/WPA2 is so I won't bang on about the encryption or protocols a great deal. In short WPA and WPA2 both have a maximum of 256bit encrypted with a maximum of 64 characters in the password. The encryption is really only 64bit but x 4 because ...more
Near Field Communication, or NFC for short, is a feature that allows our smartphones to wirelessly communicate with other devices over a short distance while using almost no power at all. Think of it like a slimmed-down version of Wi-Fi or Bluetooth that can send a small burst ...more
Hello fellow Nullbytiens, today we will be talking about IRC again (if you haven't read OTW's post about head over there now)and more specifically about using 1 nickname with multiple devices or IRC clients. IRC was a protocol that was developed in 1988 and doesn't support us ...more
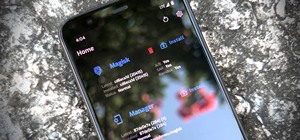
Considering that nearly half a million brand new apps were published to the Google Play Store in 2015, you can definitely call it a banner year for Android development. In fact, it's getting to the point where we're a bit spoiled as end users, since we've grown to expect somet ...more
UPDATE: This post is outdated, the latest version with the correct links and updated instructions can be found at my blog, here - https://techkernel.org/2015/12/19/embed-metasploit-payload-in-apk-manually/ Hi guys, I'm here again with my second tutorial, as I promised. Metas ...more
Greetings my fellow aspiring hackers, Huh :) . Its that part of the year when friends and family come together for reunions and family gathering. Christmas is the only time of the year where the sensation and desire to bond and repair lost and broken relationships becomes str ...more
When anyone brings up Tasker, the first topic that always gets discussed is how powerful the Android automation app can be. But all of that power can be overwhelming for some people, so even if you're a Tasker pro, it's hard to share your awesome creations with friends that do ...more
Google has finally released the next version of the world's leading operating system—Android 6.0 Marshmallow. This latest iteration isn't as much of a visual overhaul as Lollipop was, but it packs in more new functionality than almost any update before it. Awesome features lik ...more
Let's say you're flush with Google Opinion Rewards credits, or you just got a Google Play gift card for your birthday. This is a perfect opportunity to remove ads and unlock new features by upgrading some of your free apps to their paid counterparts, or to finally purchase tha ...more
Apple's special September event just wrapped up with the company unveiling several new products, including the iPhone 6S, iPhone 6S Plus, iPad Pro, and the new Apple TV set-top box. In addition to hardware, Apple also discussed a couple of its latest software platforms, iOS 9 ...more
Checking the weather ranks among the most mundane but essential tasks you can do on your smartphone. Thankfully, both the iOS App Store and Google Play are loaded with weather apps that add some much needed spice to this daily routine, giving you less of a reason to be caught ...more
Update My sincere apologies guys, but I just got a call from Rackspace to set up my "managed account". After a long discussion, there is no longer an "un-managed" option. This means that there is a minimum support fee of 50 dollars USD tacked on to every account. The instruct ...more
Whether you're just getting your first Android, or are already on your fifth annual cycle of picking up the latest flagship, there is always the question of what to do after booting up your device for the first time. You can go the route of keeping your device the way the man ...more
One of Android's biggest strengths, when compared to other mobile operating systems is its open file structure. Google introduced a built-in file manager with Marshmallow that provides basic file management, but like with most apps on Android, there are alternatives. Third-par ...more
Whether I'm in my car or making dinner, I always have music playing. And since I don't like to keep my headphones on me at all times, I end up using my Android's built-in speakers a good portion of the time. Companies like HTC know how much people use their phone's speakers, ...more
Is your Mac starting to feel messy and sluggish after using iOS 8 on your iPhone every day? Even with all of the iOS-friendly features built in to Mac OS X Yosemite, your Mac can still feel kind of "old" in comparison to an iOS device—but it doesn't have to. Using the tips and ...more
Today I am going to teach the various ways that you can use social engineering to hack a system. For those of you that have followed my past tutorials, you know that social engineering can unlock a world of possibilities. This is because no matter how many firewalls, no matter ...more
Welcome back, my greenhorn hackers, and happy New Year! Now that your heads have recovered from your New Year's Eve regaling, I'd like to grab your attention for just a moment to preview 2015 here at Null Byte. I hope you will add your comments as to what you would like to se ...more
If you took a big step back and really looked at the world, you'd see how downright silly our nations look when they put up fences to separate themselves from one another. Creatures big and small roam free while respecting each other's space, but humans create borders and phys ...more
While most of us don't think twice about dragging a pattern or using Touch ID to open our phones, or entering a password in for our email and bank accounts, these features are there to protect some of our most private information. Only problem is, they don't do a good job of i ...more
It seems like every day now that we see a new headline on a cyber security breach. These headlines usually involve millions of records being stolen from some large financial institution or retailer. What doesn't reach the headlines are the many individual breaches that happen ...more
When the Chromecast first came out about a year ago, developers were quick to find a way to root the streaming device. Google was almost as fast, however, in updating the Chromecast's firmware to close the loophole that this method used. Recently, the developers at Team Eurek ...more
It was the star of the show, but now that Android L has been released for preview to Nexus 5 and Nexus 7 owners, there's a lot that Google didn't tell us about their latest mobile operating system, rumored to be called Lollipop. First off, if you haven't already installed the ...more
Multitasking has always been one of Android's strengths relative to other mobile operating systems. As the first cell phone OS with "true" multitasking, Android's been ahead of the game in this department for quite some time. To stay on top of the heap, though, further innova ...more
When Apple recently unveiled iOS 8, many of the newly-added features in their mobile OS seemed eerily familiar to Android users. This is probably because the vast majority of these new features have been available in Android for quite some time. If imitation truly is the sinc ...more
Whether it's spotty data coverage, bad customer service, or a high monthly bill, at some point many of us consider changing carriers. The problem is, we often don't want or need to change our devices. Since it's now legal to unlock devices to bring to new carriers, getting dev ...more
April Fool's Day, aka National Screw with Your Friends Day, is finally here. You can always pull a conventional prank, like strategically placing a whoopee cushion on your mom's chair, but that joke has been exhausted generations before smartphones were around. We live in a d ...more
From personal photos and videos to online banking passwords saved in your web browser, your phone has all kinds of sensitive data that needs to be protected. One of the best things you can do for your Samsung Galaxy S4's data is have a lock screen with a hard-to-guess PIN or p ...more
Welcome back, my neophyte hackers! Have you ever had a neighbor that you're certain is up to no good? Maybe you've seen him moving packages in and out at all hours of the night? Maybe you've seen people go into his home and never come out? He seems like a creep and sometimes ...more
Attention all veterans and active-duty military personnel—this coming Tuesday, November 11th, is Veterans Day, that time of year where the whole country thanks us for our service. For the most part, a simple thanks will do, but some folks like to go above and beyond and give u ...more
The integration of technology into automobiles is becoming more and more widespread each year. Tesla's Model S features a 17" display in the middle of the dash with navigation, music control, and even an Internet browser. Mercedes is working on incorporating Google Glass into ...more
Whenever a friend borrows my Samsung Galaxy S3 to browse the web or make a quick call, I always pause to make sure there's nothing incriminating on it. I'm no superfreak, but some of my friends are, so I have more than a few photos on my device that I wouldn't wish upon anyone ...more
Today's project will show how you can convert your laptop, smartphone, or tablet computer into a makeshift projector—just in time for March Madness! It's super cheap to build, and can add a little bit of creative fun to your next sports party. Video: . This DIY is geared mainl ...more
Remote Desktop gives you access to your Windows 8 PC or device from wherever you are to run your applications and access your files remotely. Left an important document on your work computer? Want to run a legacy x86 desktop app from your Surface? You can use Remote Desktop ...more
There is never a dull moment when it comes to the internet. You can find practically anything you want, whenever you want it. To make that process even smoother and more direct, companies have created a bunch of apps designed to help you find what you're looking for, or enligh ...more
Will the predicted apocalyptic date—December 21st, 2012—really be the end of the world? In this ongoing five-part series, we examine what would happen if zombies, nuclear weapons, cyber wars, earthquakes, or aliens actually destroyed our planet—and how you might survive. End ...more
All kinds of people pretend to be someone they're not on the internet, including scammers, people attempting to wind others up, hackers and web predators. Almost all of these people will leave bases uncovered and they're all easy to expose when you understand how to. Here are ...more
Apple's new iOS 16 software update is finally here, and there are over 350 new features and changes for you to enjoy on your iPhone. There are major lock screen and home screen improvements, a pleasant surprise for the Contacts app, and tons of new upgrades to Safari, Mail, Me ...more
Never being contacted for a job you're interested in interviewing for is a terrible feeling. It might make you feel inadequate as if your qualifications aren't up to par, but the problem might be that your resume isn't even getting read in the first place. Most recruiters and ...more
Captions are great for catching every word and important sound in a movie or TV show, but now there's a way in Google Chrome's desktop browser to enjoy captions for any audio file or source. You could ensure you never mishear a comment during an online meeting, and you could e ...more
In response to Sony unveiling its own holographic display back in October, Looking Glass Factory CEO Shawn Frayne quickly penned a letter welcoming the electronics mainstay to the field, with a post-script teasing the reveal of their own for December of 2020. That day is fina ...more
Apple just released the fourth public beta for iOS 14 today, Thursday, Aug. 6. This update comes two days after the company released iOS 14 developer beta 4, 15 days after Apple seeded developers the third dev beta, and two weeks after the release of public beta 3. Apple rele ...more
Apple just released the fourth developer beta for iOS 14 today, Tuesday, Aug. 4. This update comes 13 days after Apple seeded developers the third dev beta, and 12 days after public testers got their hands on public beta 3. Apple released this update at 10 a.m. PDT, the stand ...more
Apple just released the third public beta for iOS 14 today, Thursday, July 23. This update comes one day after the company released iOS 14 developer beta 3, and two weeks after the release of iOS 14 public beta 2. Apple released this update at 10 a.m. PDT. While we expected t ...more
Apple just released iOS 14 developer beta 3 for iPhone today, Wednesday, July 22. The update comes 15 days after Apple released the second developer beta for iOS 14, and 13 days after the release of iOS 14 public beta 2. Apple released this update at 10 a.m. PDT, the company' ...more
Whether you miss the good old days of Telnet or you want to know what hacking was like when security was nothing but an afterthought, Telehack is the game for you. The text-based hacking game is a simulation of a stylized combination of ARPANET and Usenet, circa 1985 to 1990, ...more
When it comes to sniffing Wi-Fi, Wireshark is cross-platform and capable of capturing vast amounts of data. Making sense of that data is another task entirely. That's where Jupyter Notebook comes in. It can help analyze Wi-Fi packets and determine which networks a particular p ...more
People fundamentally distrust magicians. And they should. The illusions they proffer are just that, illusions meant to astound rather than tangible interactions and results that have weight and meaning in our real world. Our lizard brains know this, and, no matter what the out ...more
Router gateways are responsible for protecting every aspect of a network's configuration. With unfettered access to these privileged configurations, an attacker on a compromised Wi-Fi network can perform a wide variety of advanced attacks. Brute-Forcing Router Logins with Pat ...more
Apple released iOS 13.0 on Sept. 19 and announced on the same day the release of iOS 13.1 on Sept. 30. But that deadline was pushed up to Sept. 24, and that's why we have 13.1 just five days after 13.0. But that's good news since we don't have to wait any longer for some of th ...more
Why do you need augmented reality? Because enterprise, they say. And while that's certainly true for several disciplines, there's still that mainstream use case hanging out there waiting for users to discover beyond the realm of enterprise and gaming. After much thought — and ...more
Since we wouldn't have Android without Google, everyone has come to realize that the Pixel smartphones are a prime example of what an Android smartphone should be. With so many unique software related features, no wonder people want that Pixel experience. OnePlus offers its O ...more
The price of hacking Wi-Fi has fallen dramatically, and low-cost microcontrollers are increasingly being turned into cheap yet powerful hacking tools. One of the most popular is the ESP8266, an Arduino-programmable chip on which the Wi-Fi Deauther project is based. On this ine ...more
A relay is an electrical component that works like a light switch, where it's turned on or off with an electrical signal. By connecting a relay to a Wi-Fi connected microcontroller like an ESP8266, you can build a connected switch that can be controlled from the web browser of ...more
Many popular IoT devices have terrible security. For instance, a hacker who's on the same Wi-Fi network as a Sonos speaker can assume direct control over the device's behavior. If an IoT device doesn't secure the messages used to control it over a network, it's easy for somebo ...more
If you've grown bored of day-to-day hacking and need a new toy to experiment with, we've compiled a list of gadgets to help you take password cracking and wireless hacking to the next level. If you're not a white hat or pentester yourself but have one to shop for, whether for ...more
Smartphones and other Wi-Fi enabled devices send radio signals called probe frames to locate nearby wireless networks, which makes them easy to track by listening for their unique MAC address. To show how this kind of tracking works, we can program a NodeMCU in Arduino to snif ...more
The most common Wi-Fi jamming attacks leverage deauthentication and disassociation packets to attack networks. This allows a low-cost ESP8266-based device programmed in Arduino to detect and classify Wi-Fi denial-of-service attacks by lighting a different color LED for each ty ...more