How To : Write "congratulations" in multiple languages
Write "congrats" in several languages including Japanese, Spanish, Portuguese, Russian, French, English, and Hindi.

Write "congrats" in several languages including Japanese, Spanish, Portuguese, Russian, French, English, and Hindi.
Write "Happy Anniversary" to a friend or loved one in French, Spanish, Portuguese, Russian, Japanese and English: all at once.
Watch this video to learn to write "Happy Birthday" in French, Portuguese, Spanish, Russian, Japanese and Hindi.
Write "I miss you" to a loved one in several languages including Japanese, Spanish, Portuguese, Russian, French, English, and Hindi.
Write you're sorry in Russian, Spanish, Portuguese, Japanese and English.
Watch this video to learn how to write "I love you" in multiple languages such as French, Spanish, Portuguese, Hindi, Greek, German, Russian and English.
A marriage proposal in multiple languages such as Spanish, Portuguese, Hindi, French, Japanese, Russian, and English.
Watch this video to learn to write "good luck and good bye" in French, Spanish, Portuguese, Hindi, Greek, German, Russian and English.
Tell a loved one "You're always on my mind" in many languages such as: Spanish, Hindi, French, Russian, Japanese, and English.
With tools such as Reaver becoming less viable options for pen-testers as ISPs replace vulnerable routers, there become fewer certainties about which tools will work against a particular target. If you don't have time to crack the WPA password or it's unusually strong, it can ...more
While our time with the Protostar VM from Exploit Exercises was lovely, we must move on to bigger things and harder challenges. Exploit Exercises' Fusion VM offers some more challenging binary exploitation levels for us to tackle. The biggest change is that these levels are al ...more
If we were to assign a theme for the 2019 edition of the Next Reality 30 (NR30), it might be something along the lines of, "What have you done for me lately?" Many of the top names in the industry from the 2018 edition remain the same, but their positions have shuffled. The p ...more
As a web developer, I often read articles about hackers (from the lowly to the knowledgeable) infiltrating websites via the dreaded 'SQL Injection' method and completely taking control, changing, gaining access, or destroying the owner's data. As a fellow web developer, I'm su ...more
The last few months of WikiLeaks controversy has surely peaked your interest, but when viewing the WikiLeaks site, finding what you want is quite a hard task. Despite rumors of easy access via the Kindle and iTunes App Store, there currently is no way to view the leaked docum ...more
Want to program your own Java games and applications but don't know beans about object-oriented programming? Never you fear. This free video tutorial from TheNewBostonian will have you coding your own Java apps in no time flat. Specifically, this lesson discusses how to work w ...more
Want to program your own Java games and applications but don't know beans about object-oriented programming? Never you fear. This free video tutorial from TheNewBoston will have you coding your own Java apps in no time flat. Specifically, this lesson discusses how to to create ...more
Want to program your own Java games and applications but don't know beans about object-oriented programming? Never you fear. This free video tutorial from TheNewBoston will have you coding your own Java apps in no time flat. Specifically, this lesson discusses how to use multi ...more
Want to program your own Java games and applications but don't know beans about object-oriented programming? Never you fear. This free video tutorial from TheNewBostonian will have you coding your own Java apps in no time flat. Specifically, this lesson discusses how to store ...more
Starting up a website can be daunting if you know nothing about web design or setup, but there are some tips to get the right people finding, looking, and returning to your site. A good landing page gives visitors exactly what they are looking for, and converts them from brows ...more
Welcome to Minecraft World! Check out our advanced tutorials and come play on our free server. For about the past month, the folks at Mojang have been leaking pre-releases of Minecraft 1.9 and they've added many exciting things. Additions to the game include: potions, new mob ...more
Huzzah! My sentences have been recorded! This is normally the most exciting part of beginning a language with this method, because you actually had another person do something for you that is really of great value. I remember receiving my first recording in Japanese. I listen ...more
In my first installment in this series on professional hacking tools, we downloaded and installed Metasploit, the exploitation framework. Now, we will begin to explore the Metasploit Framework and initiate a tried and true hack. Before we start hacking, let's familiarize ours ...more
What if I told you that you could read minds? You'd most likely think I was crazy, and you'd be right. But what I really meant is that you could make people think that you could read minds, something that's not the least bit crazy. Performing mind reading — and it is a perfor ...more
Injection is an attack vector that involves breaking out of a data context and switching into a programming context through the use of special characters. These characters are significant to the interpreter being used, but not needed for the general user input being asked for. ...more
Introduction The 3 major anonymity networks on the Internet are Tor/Onionland, I2P and Freenet. If you feel confused on which one is the "best" one to use the answer is simple. Use all three! Each anonymity network is designed for a different specific purpose. One network al ...more
Okay, so you've decided to take the plunge, and participate in our Love. Earn program with a how-to article. But, for whatever reason, your article keeps getting rejected by WonderHowTo, and you're wondering, well, where's the love? We've decided to provide you with a few gui ...more
To create an elegant WordPress blog or website from scratch without being noticed that you're a complete beginner, you need that drive and pairs of eyes and ears. It may seem difficult at first but it can truly be fun and exciting. In order for you to have a long lasting blog ...more
In our media-enriched world, past and present, SCRABBLE has made a name for itself, whether deliberately, subconsciously, or influentially. You may have a read a book that had the popular word game within a chapter, watched a movie that showed your favorite characters bringing ...more
“Zero-zero is a big score.” Ron Atkinson "Part 0? Are we in computer science class or what? We aren't talking about arrays here, are we?" No, nothing to do with arrays. This article is simply for if you are thinking of creating a new WordPress blog and want to do that on a M ...more
Note: The article assumes that the reader has a fundamental understanding of at least one other programming language, and that this is intended serve as a quick reference for Perl's basic syntax & behavior in regards to Variables, Control Structures, & Functions. Learning to ...more
Ever since the update that turned Google Keyboard into Gboard rolled out, a lot of people have been noticing that word suggestions and auto-correct features are downright slow. The issue seems to affect users with multiple languages installed more than anyone, though it can al ...more
Choosing which programming language to learn next can be a truly daunting task. That's the case regardless of whether you're a Null Byter just beginning a career in development and cybersecurity or you're a seasoned ethical hacking and penetration tester with years of extensiv ...more
One of the first steps in attacking a web application is enumerating hidden directories and files. Doing so can often yield valuable information that makes it easier to execute a precise attack, leaving less room for errors and wasted time. There are many tools available to do ...more
Cases and stickers are always great, but they aren't the only way to customize an iPhone. The software on your device is full of customization options, from a better-looking home screen and cooler lock screen wallpapers to app icon changes and a system-wide dark mode. There's ...more
Welcome back, everyone! In this lesson, I'm going to go over the use of the echo function and variables, as well as basic syntax. You will need: A text editor - I personally recommend the free (and amazing) Notepad ++, but you can use any text editor you want, even Windows' ...more
Welcome back, my amateur hackers! Over the course of the next year, we will be developing our own zero-day exploits. In my first article in this series, I introduced you to buffer overflows, which are the source of some of the most lethal exploits, particularly the "remote co ...more
Have you ever gotten into a taxi in a foreign country and had trouble expressing where you want to go? Or tried to ask a waiter what's in the dish you're eyeing on the menu? Perhaps you just want to know what's happening in another country, and the news outlets don't offer a t ...more
Your social security number, credit card information, and medical history can fall into the wrong hands if you're not careful about how and where you share your data online. If you really care about your data, there are tools and techniques you can utilize to protect yourself ...more
Hello, everyone! Many of you don't even know about my existence here on Null Byte, so I thought of contributing something rather interesting. Recently, someone asked how to make your own "Bad USB," and I promised to make a how-to on this topic. In addition, it would be nice t ...more
Welcome back, my greenhorn hackers, and happy New Year! Now that your heads have recovered from your New Year's Eve regaling, I'd like to grab your attention for just a moment to preview 2015 here at Null Byte. I hope you will add your comments as to what you would like to se ...more
Welcome back, my greenhorn hackers! Recently, I asked the Null Byte community what subject they would most like me to cover in future tutorials. Many of you cited scripting, and I decided it's best to cover this subject soon, so here goes. Any self-respecting hacker must be ...more
Undo. Redo. These two actions are forever intertwined, but they're missing from the standard keyboard on Android. Accidentally delete a word, and there is no Ctrl + Z to undo this mistake. But there is finally a solution available on Samsung Galaxy phones. Now, if you acciden ...more
North American users get a raw deal when it comes to Sony devices. For some reason, the critically-acclaimed Xperia lineup of smartphones is hardly ever available here, whereas in Europe, the Sony Xperia Z series is one of the most popular flagship devices around. But now, th ...more
In this series you will learn how to use PHP to perform attacks, gather information, and setup backdoors. Along with performing attacks you will learn how to protect yourself from them. In this part you will learn about PHP as well as install Apache and PHP. What you'll need f ...more
Hello my anxious hackers, the week has started and here we begin a new series that I think will help many here and not only, for those that have the opportunity to follow our tutorials but they are not yet part of the community. Don't be a script-kid? what do you mean? In pro ...more
Apple's iOS 13 has been available for beta testing since June, and the stable release pushed out to everyone on Thursday, Sept. 19. To help you make the most out of iOS 13 for iPhone, we've rounded up everything you'll want to know, whether a colossal feature, small settings c ...more
We're almost there to completing the setup of your Mac for hacking! Now that we have Git and Homebrew under our belts, it's time to take on something fairly easy, but very important for our hacking needs. Ruby is an object-oriented scripting language used to write powerful pr ...more
Have you ever used an open wifi, which after you connect displays a website to enter your credentials to get internet? That website is called captive portal and widely used in airports, hotels, universities etc. Have you ever wondered what would happen if someone would set up ...more
Hi, everyone! Recently, I've been working on a pretty interesting and foolish project I had in mind, and here I'm bringing to all of you my findings. This guide's main aim is to document the process of building an Android kernel, specifically a CyanogenMod kernel and ROM, and ...more
Augmented objects in the classroom are closer than they appear. Within celebrated the close of summer with Wonderscope's unveiling of a fourth installment in its iOS app, titled Clio's Cosmic Quest. This educational AR experience lasts about 10 minutes, and it is designed for ...more
Learning Chinese is hard, but it can be a lot easier with the help of a few great apps. As a native English speaker who's currently living in China, this is a process I've recently gone through. After playing the field, here are the three apps I personally think will help you ...more
Not content with bringing the first untethered mixed reality headset to market, Microsoft wants to expand their Windows Holographic operating system beyond HoloLens into vastly more robust technologies. Through partnerships with other hardware manufacturers, Microsoft is hopi ...more
Welcome my aspiring hackers and programmers! Today i will introduce you to a programming language that as a hacker you should have in your set of hacking/programming skills (except if you're only interested in web hacking/programming...then you should go learn some html or PH ...more
Samsung unveiled their new flagship device, the Galaxy S4, at a live event in New York City today. Here's a quick rundown of the specs and all of the new features that you can expect when you finally get your hands on one (whenever that will be). The GS4's Specs 5" 1920x1080 ...more
Welcome back, my tenderfoot hackers! In some of my past articles, I've shown numerous ways of embedding a listener/rootkit on a remote system, including buffer overflows of the operating system, getting the victim to click on a link to our malicious website, and sending a mal ...more
The keyboard on your iPhone or iPad has a few new tricks up its sleeve with Apple's latest software updates, such as improved autocorrect and emoji stickers. However, a particularly hidden feature that lets you change the sound values of letters in other languages has gone unn ...more
While you're probably already used to the keyboard on your iPhone, you'll likely never be able to type on it as fast as you can on a computer keyboard. But that doesn't mean you can't get any faster at typing on your iPhone. By using keyboard shortcuts to auto-populate commonl ...more
In order for software developers to do their jobs as new hardware reaches the market, they will need the right tools to get their projects off the ground and into augmented and mixed reality devices. There have been completely new approaches to development when it comes to AR ...more
Welcome back! Sorry I've been gone for so long, but if anyone has been keeping up with these articles, you'll know that when I get quiet, something is cooking under the surface. In other words, I've been working on a project lately, so I haven't had much time! When I was thin ...more
Welcome back, my novice hackers! In a recent tutorial, I showed you how to use shikata_ga_nai to change the signature of a payload to evade detection by security devices (firewalls, IDS, etc.) and AV software. Shikata_ga_nai is an encoding module in Metasploit that XORs the ...more
 How To:
Make Your iPhone Do All Your Talking for You on Calls and in Person
How To:
Make Your iPhone Do All Your Talking for You on Calls and in Person
 How To:
Add Website Shortcuts to Your iPhone's Home Screen for Fast Access to Web Apps and Bookmarks
How To:
Add Website Shortcuts to Your iPhone's Home Screen for Fast Access to Web Apps and Bookmarks
 News:
Apple Pencil 3 Is Almost Here — And It Comes with Squeeze Gestures and These Other Features
News:
Apple Pencil 3 Is Almost Here — And It Comes with Squeeze Gestures and These Other Features
 How To:
The Messaging Trick You Never Knew You Needed
How To:
The Messaging Trick You Never Knew You Needed
 How To:
Customize and Use Control Center on Your iPhone for Quick Access to Your Most-Used Apps, Features, and Settings
How To:
Customize and Use Control Center on Your iPhone for Quick Access to Your Most-Used Apps, Features, and Settings
 How To:
11 Features Coming to Apple News on Your iPhone with iOS 17.5 — Including Some Big Ones!
How To:
11 Features Coming to Apple News on Your iPhone with iOS 17.5 — Including Some Big Ones!
 How To:
Apple's Integrating Game Center Leaderboards into News+ Puzzles with iOS 17.5
How To:
Apple's Integrating Game Center Leaderboards into News+ Puzzles with iOS 17.5
 How To:
Apple Has a Killer New Word Game Puzzle Called Quartiles Hiding on iOS 17.5
How To:
Apple Has a Killer New Word Game Puzzle Called Quartiles Hiding on iOS 17.5
 How To:
Identify Any Song Playing on Instagram, TikTok, and Other Apps on Your iPhone Using Shazam
How To:
Identify Any Song Playing on Instagram, TikTok, and Other Apps on Your iPhone Using Shazam
 How To:
Apple News Gives You More Options for Automatic Downloads on iOS 17.5
How To:
Apple News Gives You More Options for Automatic Downloads on iOS 17.5
 How To:
27 New Features and Changes Coming to Your iPhone with iOS 17.5
How To:
27 New Features and Changes Coming to Your iPhone with iOS 17.5
 How To:
Download and Install iOS 17.5 Beta on Your iPhone — And Try New Features Before Everyone Else
How To:
Download and Install iOS 17.5 Beta on Your iPhone — And Try New Features Before Everyone Else
 How To:
Download and Install iPadOS 17.5 Beta on Your iPhone to Explore New Features Before Everyone Else
How To:
Download and Install iPadOS 17.5 Beta on Your iPhone to Explore New Features Before Everyone Else
 How To:
Update Your iPhone's Lock Screen with an Attention-Grabbing Note, Reminder, Warning, or Other Custom Message
How To:
Update Your iPhone's Lock Screen with an Attention-Grabbing Note, Reminder, Warning, or Other Custom Message
 How To:
Your iCloud Email Lets You Create Aliases to Protect Your Primary Email Address and Organize Your Inbox
How To:
Your iCloud Email Lets You Create Aliases to Protect Your Primary Email Address and Organize Your Inbox
 How To:
Use Your iPhone's Built-in Image Analyzer to Reveal the Hidden Meaning Behind Symbols, Signs, and More
How To:
Use Your iPhone's Built-in Image Analyzer to Reveal the Hidden Meaning Behind Symbols, Signs, and More
 Text Replacements:
The Secret Weapon to Typing More with Less on Your iPhone, iPad, or Mac
Text Replacements:
The Secret Weapon to Typing More with Less on Your iPhone, iPad, or Mac
 How To:
Focus Profiles Will Change How You Use Your iPhone — Here's How to Set Them Up for Distraction-Free Experiences
How To:
Focus Profiles Will Change How You Use Your iPhone — Here's How to Set Them Up for Distraction-Free Experiences
 How To:
Force Restart an iPhone 15, 15 Plus, 15 Pro, or 15 Pro Max When It's Frozen, Glitchy, or Won't Turn On
How To:
Force Restart an iPhone 15, 15 Plus, 15 Pro, or 15 Pro Max When It's Frozen, Glitchy, or Won't Turn On
 How To:
Create Unlimited iCloud Email Address Variations to Take Total Control Over Your iCloud Mail Inbox
How To:
Create Unlimited iCloud Email Address Variations to Take Total Control Over Your iCloud Mail Inbox
 How To:
Make Your iPhone Do All Your Talking for You on Calls and in Person
How To:
Make Your iPhone Do All Your Talking for You on Calls and in Person
 How To:
See Passwords for Wi-Fi Networks You've Connected Your Android Device To
How To:
See Passwords for Wi-Fi Networks You've Connected Your Android Device To
 How To:
Use FaceTime's Secret Hand Gestures and Reaction Buttons to Add Animated On-Screen Effects to Your Video Feed
How To:
Use FaceTime's Secret Hand Gestures and Reaction Buttons to Add Animated On-Screen Effects to Your Video Feed
 How To:
Dox Anyone
How To:
Dox Anyone
 How To:
Make Spoofed Calls Using Any Phone Number You Want Right from Your Smartphone
How To:
Make Spoofed Calls Using Any Phone Number You Want Right from Your Smartphone
 How To:
Dial These Secret Codes to See if Someone Is Hijacking Calls & Texts on Your iPhone
How To:
Dial These Secret Codes to See if Someone Is Hijacking Calls & Texts on Your iPhone
 VLC 101:
How to Stream Movies from Your Computer to Your Android Phone
VLC 101:
How to Stream Movies from Your Computer to Your Android Phone
 How To:
Play straight gin
How To:
Play straight gin
 How To:
Keep Your Night Vision Sharp with the iPhone's Hidden Red Screen
How To:
Keep Your Night Vision Sharp with the iPhone's Hidden Red Screen
 How To:
Hack Apache Tomcat via Malicious WAR File Upload
How To:
Hack Apache Tomcat via Malicious WAR File Upload
 Modular Origami:
How to Make a Cube, Octahedron & Icosahedron from Sonobe Units
Modular Origami:
How to Make a Cube, Octahedron & Icosahedron from Sonobe Units
 Warning:
Sensitive Info You Black Out in Images Can Be Revealed with a Few Quick Edits on Your iPhone
Warning:
Sensitive Info You Black Out in Images Can Be Revealed with a Few Quick Edits on Your iPhone
 How To:
Create an Admin User Account Using CMD Prompt (Windows)
How To:
Create an Admin User Account Using CMD Prompt (Windows)
 How To:
Crack SSH Private Key Passwords with John the Ripper
How To:
Crack SSH Private Key Passwords with John the Ripper
 How To:
16 Harry Potter Spells for Siri That Turn Your iPhone into a Magical Elder Wand
How To:
16 Harry Potter Spells for Siri That Turn Your iPhone into a Magical Elder Wand
 How To:
Hide Stories in Your Facebook Feed on iPhone or Android
How To:
Hide Stories in Your Facebook Feed on iPhone or Android
 How To:
Scan for Vulnerabilities on Any Website Using Nikto
How To:
Scan for Vulnerabilities on Any Website Using Nikto
 How To:
Make Siri Say Whatever You Want Every Time You Connect Your iPhone to a Charger
How To:
Make Siri Say Whatever You Want Every Time You Connect Your iPhone to a Charger
 Redstone Logic Gates:
Mastering the Fundamental Building Blocks for Creating In-Game Machines
Redstone Logic Gates:
Mastering the Fundamental Building Blocks for Creating In-Game Machines
 How To:
Disarm a Manipulative Sociopath
How To:
Disarm a Manipulative Sociopath
 How To:
Trigger iMessage Effects with Just a Keyword
How To:
Trigger iMessage Effects with Just a Keyword
 How To:
15 Hidden iMessage Features for iPhone You Probably Didn't Know About
How To:
15 Hidden iMessage Features for iPhone You Probably Didn't Know About
 How To:
Scrape Target Email Addresses with TheHarvester
How To:
Scrape Target Email Addresses with TheHarvester
 How To:
Fold the Record-Setting Glider-Style Paper Airplane (Guinness World Records)
How To:
Fold the Record-Setting Glider-Style Paper Airplane (Guinness World Records)
 How To:
Make a Self-Freezing Coca-Cola Slushy (Or Any Kind of Instant Soda Slurpee)
How To:
Make a Self-Freezing Coca-Cola Slushy (Or Any Kind of Instant Soda Slurpee)
 How To:
Apple Has a Killer New Word Game Puzzle Called Quartiles Hiding on iOS 17.5
How To:
Apple Has a Killer New Word Game Puzzle Called Quartiles Hiding on iOS 17.5
 How To:
Perform Advanced Man-in-the-Middle Attacks with Xerosploit
How To:
Perform Advanced Man-in-the-Middle Attacks with Xerosploit
 How To:
34 New Features and Changes for Your iPhone on iOS 17.4
How To:
34 New Features and Changes for Your iPhone on iOS 17.4
 How To:
Make a Homemade Bee & Wasp Trap (Kill or No-Kill)
How To:
Make a Homemade Bee & Wasp Trap (Kill or No-Kill)
 Android Basics:
How to Install ADB & Fastboot on Mac, Linux & Windows
Android Basics:
How to Install ADB & Fastboot on Mac, Linux & Windows
 How To:
Boot Your Galaxy S8 or S8+ into Recovery Mode or Download Mode
How To:
Boot Your Galaxy S8 or S8+ into Recovery Mode or Download Mode
 How To:
Use John the Ripper in Metasploit to Quickly Crack Windows Hashes
How To:
Use John the Ripper in Metasploit to Quickly Crack Windows Hashes
 How To:
Delete the T-Mobile App from Any Android Phone — No Computer Needed
How To:
Delete the T-Mobile App from Any Android Phone — No Computer Needed
 How To:
Create the Most Compact 2x2 Hidden Piston Door in Under 50 Seconds!
How To:
Create the Most Compact 2x2 Hidden Piston Door in Under 50 Seconds!
 How To:
Create a Hidden Piston Door in Minecraft
How To:
Create a Hidden Piston Door in Minecraft
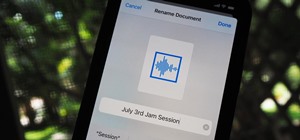 How To:
Quickly Extract the Audio Track from Any Video on Your iPhone — Right from the Share Sheet
How To:
Quickly Extract the Audio Track from Any Video on Your iPhone — Right from the Share Sheet
 How To:
Hack Wi-Fi & Networks More Easily with Lazy Script
How To:
Hack Wi-Fi & Networks More Easily with Lazy Script
 How To:
Build a Beginner Hacking Kit with the Raspberry Pi 3 Model B+
How To:
Build a Beginner Hacking Kit with the Raspberry Pi 3 Model B+
 How To:
Exploit PHP File Inclusion in Web Apps
How To:
Exploit PHP File Inclusion in Web Apps
 How To:
10 Ways to Open a Beer Without a Bottle Opener
How To:
10 Ways to Open a Beer Without a Bottle Opener