This how-to video describes how to properly write a cover letter. It explains that a cover letter is a separate selling point from the resume when applying for a job. The cover letter should only be about two-thirds of a page long and can easily be broken into three parts. Par ...more
This video features a very handy technique for writing a cover letter in less than a minute- and all you need is a tool called Text Expander, which can be easily downloaded. The basic idea behind this program is that you can create shortcut keys to text that you commonly use, ...more
Cases and stickers are always great, but they aren't the only way to customize an iPhone. The software on your device is full of customization options, from a better-looking home screen and cooler lock screen wallpapers to app icon changes and a system-wide dark mode. There's ...more
The newest version of macOS has arrived. While everyone's mind is being blown by Mojave's groundbreaking new Dark Mode, we'll be taking advantage of its insecure file permissions to establish a persistent backdoor with a self-destructing payload that leaves little evidence for ...more
An attacker with shell access to a Linux server can manipulate, or perhaps even ruin, anything they have access to. While many more subtle attacks could provide significant value to a hacker, most attacks also leave traces. These traces, of course, can also be manipulated and ...more
I noticed the neon yellow sign at the new location of Pho Bar in Chinatown right away. The sweeping cursive yellow letters spell out "Crazy Rich Broth"; the same phrase printed on the back of servers' shirts. It's the kind of minimalist but colorful design feature that is espe ...more
Third-party keyboards have been available for iPhone ever since iOS 8, but which ones are worth checking out? There have been many options over the years, and if you want keyboard features like swipe-typing and themes, you're going to have to put Apple's stock QuickType keyboa ...more
A convincing domain name is critical to the success of any phishing attack. With a single Python script, it's possible to find hundreds of available phishing domains and even identify phishing websites deployed by other hackers for purposes such as stealing user credentials. ...more
Coinhive, a JavaScript cryptocurrency miner, was reportedly discovered on the BlackBerry Mobile website. It was placed there by hackers who exploited a vulnerability in the site's e-commerce software that allowed them to anonymously mine cryptocurrency every time the website w ...more
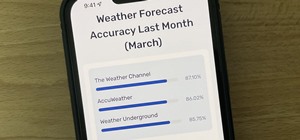
Apple released iOS 17.4 on March 5 with over 30 new features, but now it's iOS 17.5's turn for the spotlight. The update, currently in beta, gives us a few interesting updates and changes for iPhone, including a new word game, and there's even a sneak peek at what could be com ...more
After a long hiatus, we shall once again emerge from the shadowy depths of the internet to build an exploit. This time, we'll be looking at how to defeat a non-executable stack by using the ret2libc technique — a lean, mean, and brilliant way of exploiting a stack overflow vul ...more
Apple's iOS 16.3 update for iPhone had impressive new features, but iOS 16.4 might impress you even more. The latest iPhone update was released on Monday, March 27 — a day earlier than Apple Music Classical, Apple's new classical music streaming service — has at least 30 more ...more
There has been significant debate over law enforcement's right to access our digital devices in recent years. New tools from Grayshift and Cellebrite are popping up faster than ever to help government agencies, as well as traditional hackers, break into iPhones. If you're conc ...more
With a cheap computer, smaller than the Raspberry Pi, an attacker can create a remote hacking device. The device can be attached to a target router without anyone's knowledge and enable the hacker to perform a variety of network-based attacks from anywhere in the world. As th ...more
Overall, iOS is more impressive than ever with its stability enhancements, security tools, suite of apps and services, and intuitive user interface. With each passing update, things just get better and better for iPhone users. But don't think for a second that this is all beca ...more
Your phone's keyboard is one of the most commonly used apps. Whether you're typing out status updates, sending private messages, or just bombarding everyone in sight with as many emoji as you possibly can, you probably couldn't get by without a good keyboard app. Since Androi ...more
The new iOS 14 for iPhone arrived Wednesday, Sept. 15, 2020, alongside iPadOS 14, and there are a lot of features to uncover. Improved widgets. Better home screen customization. Exciting Messages improvements. New abilities in Camera and Photos. There's so much here that it'll ...more
Guitar Essentials My friends and I would secretly scribble tab in the darkly lit practice rooms in our university even though we were educated musicians. So, being able to read tablature, or tab, is essential for beginning guitarists. Tab is a curious way to write down music ...more
Have you ever wondered how to successfully create a panorama with your camera? What is a Panorama? A Panorama is a big image that has a very wide field of view, a Panorama is created by merging a sequence of photos taken adjacent to each other from the same origin, simulatin ...more
We've all attempted to fold a paper airplane before, right? One we hoped would sail majestically through the air for a good while but just ended up nose-diving into the grass. Paper planes, an invention likely as old as paper, are models of engineering; and they must account f ...more
This two part how to video series will cover the written Arabic language and then speech. This first lesson contains the basic isolated consonant forms. The second lesson will teach how to write basic words and how the isolated consonants change shape depending on where they a ...more
STANDP'S WINDOWS 7 "ASTON-2" CUSTOMIZED DESKTOP IT ROCKS COMPLETELY!. DEC 07 Computer Backup If you have taken good care of your computer then you know what you have to do to keep it running smoothly. It has to be cleaned regularly so there isn't any dirt and dust on it. It ...more
In this article, I'll be exploring the basics of Python, i.e. variables, input and output. You'll need Python (2.7+), a computer, and some free time. Variables Simply put, variables are like envelopes. They are empty and meaningless until we place objects and meaning into th ...more
Some of you might be using Tor to host hidden services, and some of you might not even know what hidden services are. If the latter's you, do not miss this article. Why? Because you can host your websites and services on the I2P darknet. It's safe and secure—it's anonymous. I ...more
At some point, we all go from organized to disorganized. Let's assume you are a business executive working in a busy corporate building. Chances are you are going to get a heavy workload and it will impact how clean your workspace is. However, this article is about keeping you ...more
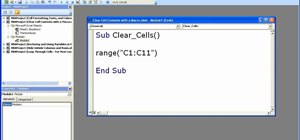
Ever wanted to display text in Minecraft? It's actually not overly difficult. In this tutorial, I will endeavor to guide you through the process between storing and displaying text from memory. To do this, we will examine two different methods of displaying and storing text in ...more
Since the invention of the printing press, books have been a dominant and iconic paradigm in our culture and throughout the world. During my years in elementary and high school, the digital world was on the rise sparking the conversation: Are Books Obsolete. Over the last year ...more
Welcome to Minecraft World! Check out our advanced tutorials and come play on our free server. For last week's Workshop, we decided to attempt to communicate long distance without the use of the chat bar. To accomplish this, we built an elementary redstone pulser that would a ...more
Guitar Essentials My friends and I would secretly scribble tab in the darkly lit practice rooms in our university even though we were educated musicians. So, being able to read tablature, or tab, is essential for beginning guitarists. Tab is a curious way to write down music ...more
Ever wonder how all of those tiny chips and components can fit inside your laptop or smartphone? If you tried to squeeze them in there yourself, your laptop would quickly become too heavy for your lap, and your mobile phone would need wheels to stay mobile. The secret to mini ...more
Have you ever forgotten your password and didn't know how to get back on your computer? Or ever had an annoying roommate you wanted to play a trick on to teach them a lesson? Or perhaps overly religious parents who think the internet is of the devil and won't let you read onli ...more
Night People: A Bad Vibes Label Profile Shawn Reed is one of our favorite people, not content with making music with Wet Hair, he also runs 'Night People' - an almost complete DIY record and tape label operation in Iowa - a label which has consistently put out and introduced ...more
I've decided to write this post so some of the fledgling street artists who may or may not follow this world in the future are informed about two things in the urban art world that are either not discussed at all, or distorted (intentionally or otherwise) to the point of misin ...more
It was brought up a while back in a Community Call to Arms that *math* is handy for encryption (and let's face it, everything) so let us go over things you just have to know. "In its simplest meaning in mathematics and logic, an operation is an action or procedure which produc ...more
This article is dedicated to sugarcane, because we all want more sugarcane in Minecraft. The best way to generate sugar cane is with an automatic reed farm that uses pistons and redstone. The pistons push the canes into the water canal you'll build, then delivers them to the c ...more
STANDP'S CUSTOM DESKTOP "ASK NOT WHAT YOUR DESKTOP CAN DO FOR YOU...". http://standp-how-to-vidzzz.wonderhowto.com/corkboard/new-post/text/ Showing newest posts with label tips-n-trick. Show older posts DEC 07 Computer Backup If you have taken good care of your computer th ...more
So, you scratched up your $500 Adobe CD and now it's unreadable. You could go buy a new one, but you already purchased it! Searching The Pirate Bay and downloading some Adobe software can usually be easy enough, but what should you watch out for? And what about your movies? W ...more
Anonymity is something that doesn't exist today. Everything you do in the world is tracked, from the purchases you make to surfing the internet—even taking pictures on your iPhone. Everything you have ever said and done on the internet is still there—somewhere. This is called ...more
Password cracking is a specialty of some hackers, and it's often thought that raw computing power trumps everything else. That is true in some cases, but sometimes it's more about the wordlist. Making a custom, targeted wordlist can cut down cracking time considerably, and Wor ...more
Deep down inside, Android is really just a fork of Linux, the popular open source desktop OS. You can see traces of its roots everywhere, and this lineage still holds a certain appeal with many Android fans. If you're in that boat, you'll love the newest notes app we just foun ...more
What happens if you unknowingly connect a malicious USB drive and it starts infecting your entire office network? Instead of having a panic attack and working all night to find a fix, you can just put on a mixed reality headset like Microsoft's HoloLens and point. Don't Miss: ...more
While landing a job isn't the easiest thing in the world, you can probably blame your résumé for a number of lost opportunities. Writing up a cover letter and résumé is frustrating and time-consuming, but if you spend the time to get them right, the effort will drastically inc ...more
Undo. Redo. These two actions are forever intertwined, but they're missing from the standard keyboard on Android. Accidentally delete a word, and there is no Ctrl + Z to undo this mistake. But there is finally a solution available on Samsung Galaxy phones. Now, if you acciden ...more
While hackers know and love the Raspberry Pi, many don't know of its cheaper cousin, the microcontroller. Unlike a Pi, which can be used more or less like a regular computer, microcontrollers like the Wi-Fi connected ESP8266 require some necessary programming skill to master. ...more
A lot of people still trust their web browsers to remember every online account password for them. If you're one of those users, you need to adopt a more secure way of managing passwords, because browser-stored passwords are hacker gold mines. With a USB Rubber Ducky and physi ...more
Hackers and makers are often grouped under the same label. While hackers draw on computer science skills to write programs and find bugs, makers use electrical engineering to create hardware prototypes from microprocessor boards like the Arduino. We'll exercise both sets of sk ...more
We use our smart devices for pretty much everything these days, from getting directions to playing games just to kill time. They're extremely important to our daily routine, and as we use our devices more and more, things get a little bit messy. Having tons of apps, contacts, ...more
Traveling is a rich and rewarding experience. When you don't speak the language, however, your trip can present some tricky obstacles. Google knows this, which is why they will now automatically translate user reviews in Google Maps and Google searches. Which is great, becaus ...more
Typing on a mobile device has come a long way since the days of flip phones. Today, there are awesome keyboard apps like Gboard, which integrates Google search features and makes typing a breeze. But the whole experience still stands to improve if you take some time to learn a ...more
Hello everyone! This is my first attempt at a tutorial here. There are a couple great assembly tutorials here, and I wanted to toss my coin in the fountain. I figured, the more tuts the better, as I had trouble learning assembly in the beginning and had to read alot of tutori ...more
I rarely receive spam mail, but every now and then I’ll get an email from Cat Fancy Magazine. I’ve never read an issue of Cat Fancy Magazine or been to their website. Actually, I’m allergic to cats. So how did they manage to get my information? Well, anytime you register for ...more
Snapchat has had more than its fair share of security failures and mishaps. The photo-sharing company is looking to better address some of these security gaps by adding new features, and today its most recent addition is live: the Captcha. New users will be asked to verify the ...more
Welcome back, my greenhorn hackers! Recently, I asked the Null Byte community what subject they would most like me to cover in future tutorials. Many of you cited scripting, and I decided it's best to cover this subject soon, so here goes. Any self-respecting hacker must be ...more
A macOS computer can reveal a lot of information about the owner, including which Wi-Fi network they have permission to access. With an Arduino-based attack, we'll use a five-dollar setup to inject a rogue Wi-Fi network and steal the list of trusted Wi-Fi networks, allowing us ...more
With an inconspicuous Android phone and USB flash drive, an attacker can compromise a Windows 10 computer in less than 15 seconds. Once a root shell has been established, long-term persistence to the backdoor can be configured with just two simple commands — all while bypassin ...more
Wi-Fi tools keep getting more and more accessible to beginners, and the LAZY script is a framework of serious penetration tools that can be explored easily from within it. This powerful and simple tool can be used for everything from installing new add-ons to grabbing a WPA ha ...more
Hate slogging through pages and pages of weighty books and lengthy work documents? You may not be able to depend on speed-reading apps, but with the right font, you can increase the number of words you scan each second, speeding up your reading pace exponentially. Familiar Is ...more
If you have a hard time remembering what you've just read on your iPad or Kindle, try changing the font next time. The typeface you use to read books, newspapers, and online articles is either hurting or helping your memory, and you'll be surprised which ones are killing your ...more
Choosing which programming language to learn next can be a truly daunting task. That's the case regardless of whether you're a Null Byter just beginning a career in development and cybersecurity or you're a seasoned ethical hacking and penetration tester with years of extensiv ...more
Your writing is just that — yours — so the work you do in Apple Pages should remain private until you choose to share it. Apple seems to share this sentiment. As another symbol of its dedication to user privacy and security, the company includes a feature in its word-processin ...more