To hack a Wi-Fi network, you need your wireless card to support monitor mode and packet injection. Not all wireless cards can do this, but you can quickly test one you already own for compatibility, and you can verify that the chipset inside an adapter you're thinking of purch ...more
Smartphones and other Wi-Fi enabled devices send radio signals called probe frames to locate nearby wireless networks, which makes them easy to track by listening for their unique MAC address. To show how this kind of tracking works, we can program a NodeMCU in Arduino to snif ...more
Three new iPhones means you have to make a choice: Do you go with the smaller iPhone XS, the larger iPhone XS Max, or the cheaper iPhone XR? There's lots to like about each model, but if you want to make an informed decision, it's time to learn what each has to offer. Here's w ...more
There's always an iPhone in our list of top phones for privacy and security, due in large part to advanced security measures like Face ID, consistent iOS updates, and easy ways to prevent unwanted access and excessive data sharing. However, some of those options actually do th ...more
Smartphones are like high tech buckets that collect our personal information through constant use. This has some obvious benefits, like getting a more personalized experience with our devices. On the other hand, this data is a tempting target for bad actors looking to make a b ...more
Conducting phishing campaigns and hosting Metasploit sessions from a trusted VPS is important to any professional security researcher, pentester, or white hat hacker. However, the options are quite limited since most providers have zero-tolerance policies for any kind of hacki ...more
Your iPhone has a lot of personal information contained within it, so of course you want your device to be secure. You don't want that information getting into the wrong hands — or any hands other than your own, for that matter. This guide breaks down the new privacy settings ...more
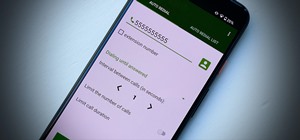
Every time you make a call or send a text, you're giving the recipient your phone number. This can be quite the security vulnerability, opening yourself up to scammers, spammers, and the feds. In this how-to, we'll look at what a burner phone is, why you might want one, and ho ...more
Hello and welcome to my article. I have made this article for anyone who wants to become a hacker, and wants to know how to get started. OVERVIEW: As you'll get further into the hacking community, and learn more about how it's all put together, you'll also realize very quick ...more
Cryptography is the science of keeping secrets, or more specifically, the science of disguising them. As a point of fact, cryptography has progressed quite a bit farther and now encompasses file and message integrity, sender authentication, and pseudo-random number generators. ...more
Safari's massive upgrade in Apple's latest iPhone software update includes new features you won't find in any other web browsers on iOS, from better ways to stay organized to enhanced security and further privacy protections. Apple's latest Safari improvements make web browsi ...more
With a simple web-based tool, you can hide secret messages for family, friends, and fellow spies inside of plain text communications, and anyone that intercepts the messages will be none the wiser. Steganography is the art of hiding secret messages comprised of text, code, au ...more
One UI has an exciting privacy feature that lets you lock apps, photos, videos, and files on your Galaxy device behind Samsung's defense-grade Knox security platform. Only you can unlock it using a pattern, PIN, or passcode, or with biometrics like fingerprint and iris locks. ...more
Your iPhone goes with you pretty much everywhere you go, and unless you have unlimited data on your cellular plan, you've probably connected to dozens of Wi-Fi hotspots over the years. Wi-Fi passwords are saved to your iPhone so you can auto-connect to the router or personal h ...more
The ESP32-CAM is a convenient little camera module with a lot of built-in power, and you can turn one into an inconspicuous spy camera to hide in any room. There's only one issue: it does omit a USB port. That makes it a little harder to program, but with an ESP32-based board, ...more
Kali Linux is the go-to Linux distribution for penetration testing and ethical hacking. Still, it's not recommended for day-to-day use, such as responding to emails, playing games, or checking Facebook. That's why it's better to run your Kali Linux system from a bootable USB d ...more
There are hidden Wi-Fi networks all around you — networks that will never show up in the list of available unlocked and password-protected hotspots that your phone or computer can see — but are they more secure than regular networks that broadcast their name to any nearby devi ...more
While obvious, it's a lot more difficult to hack into a locked computer than an unlocked computer. As a white-hat hacker, pentester, cybersecurity specialist, or someone working in digital forensics, there's an easy solution — make it so that the computer won't fall asleep and ...more
The USB Rubber Ducky is a well-known hacking device in the cybersecurity industry, but it needs to be preprogrammed before it can be used. That means it's not easy to issue commands to a target computer since you can't interact with it from afar after plugging it in. And if yo ...more
Secure Shell is one of the most common network protocols, typically used to manage remote machines through an encrypted connection. However, SSH is prone to password brute-forcing. Key-based authentication is much more secure, and private keys can even be encrypted for additio ...more
Sudo is a necessity on most Linux systems, most of which are probably being used as web servers. While the principle of least privilege is typically applied, sudo misconfigurations can easily lead to privilege escalation if not properly mediated. Which brings us to SUDO_KILLER ...more
When I review apps, I'll oftentimes end up downloading at least one or two "bad" apps that either lied about their functionality or were riddled with ads. These apps, while not as harmful as malware, can still be a major headache. This got me thinking about the other bad apps ...more
There are nearly 100,000 unique onion service addresses online with over two million people using Tor every single day. Join me as I explore a small fraction of what the Tor network has to offer. It's puzzling to imagine about 100,000 .onion websites in existence. Readers who ...more
Defcon is the largest hacker conference with something for everyone, whether it be the talks, parties, villages, or any of the hundreds of events. In this guide, we'll take a holistic view at everything that goes into attending the con for the first time, from securing your el ...more
While our time with the Protostar VM from Exploit Exercises was lovely, we must move on to bigger things and harder challenges. Exploit Exercises' Fusion VM offers some more challenging binary exploitation levels for us to tackle. The biggest change is that these levels are al ...more
Even though most phones don't have Oreo yet, Google has released Android 9.0 Pie. It's available on Google's own Pixel devices, and updates should soon be available to partnered devices from Essential, Nokia, Oppo, Sony, Vivo, and Xiaomi. We're already digging into it to highl ...more
So, your grandmother finally wants to ditch her flip phone for a shiny new smartphone? Congratulations. But helping her get used to her new device, even when it's an iPhone, is no small task. Grandma mastered checking her email in late-2012 and just recently learned there's a ...more
Privacy and security go hand in hand, especially for smartphones. When it comes to privacy, you decide what personal information about yourself is out there to discover. Security, on the other hand, is all about enforcing those privacy decisions. Sometimes privacy and securit ...more
Step 1: What Exploit Development Is and Why Should I Be Interested on About This Topic An exploit is a piece of software, a chunk of data, or a sequence of commands that takes advantage of a bug or vulnerability in order to cause unintended or unanticipated behavior to occur ...more
Your iPhone keeps track of every single place you go, especially those you frequent most often, and syncs those locations across all your iCloud-connected devices. People who gain access or already have access to your iPhone, iPad, iPod touch, or Mac may be able to view all of ...more
A dead man's switch is a fairly simple concept. If you don't perform a specific task before a set amount of time, it'll perform a specific action you set. They can be handy not just for hackers but for everyone who wants to protect themselves, someone else, or something tangib ...more
Microsoft's built-in antimalware solution does its best to prevent common attacks. Unfortunately for Windows 10 users, evading detection requires almost no effort at all. An attacker armed with this knowledge will easily bypass security software using any number of tools. As ...more
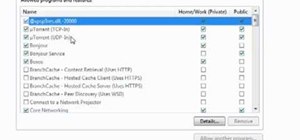
Identifying security software installed on a MacBook or other Apple computer is important to hackers and penetration testers needing to compromise a device on the network. With man-in-the-middle attacks, packets leaving the Mac will tell us a lot about what kind of antivirus a ...more
If you can't locate a specific entry in the Notes app on your iPhone, chances are that it's hiding in a different place than you thought, connected to a third-party email service such as Gmail, Yahoo, or Outlook. When one of those notes gets lost or accidentally deleted, you'r ...more
An attacker can create three, five, or even ten new Netcat connections to a compromised MacBook with one command. Performing complex post-exploitation attacks might otherwise be difficult from a single shell without this essential trick. Why Create Multiple Netcat Threads? W ...more
Penetration testing, or pentesting, is the process of probing a network or system by simulating an attack, which is used to find vulnerabilities that could be exploited by a malicious actor. The main goal of a pentest is to identify security holes and weaknesses so that the or ...more
In a time where we're more connected than ever, privacy and security have never been more important. Maybe you're not concerned, but I'm sure there's someone in your life who is, and shopping for them can be daunting. However, with these gifts, you can provide them the tools t ...more
|Choose Your View: Quick Bullet Points | Detailed Descriptions Android's newest major update is a special one — it's the tenth full version of the world's most commonly used operating system. The latest release, dubbed simply Android 10 (codename Android Q), was first showcas ...more
Smartphones are now indispensable when traveling. Domestic and overseas travel alike require food, navigation, translation, and so much more to make work or vacation successful. Gone are the days of lugging multiple tourist books around with you everywhere you go — you need to ...more
After installing Ubuntu as your primary OS, you should have protected against USB Rubber Ducky payloads, defended against hard drive forensics, and reduced the overall attack surface against physical strikes. When defending against network-based attacks, you'll want to minimiz ...more
After a long hiatus, we shall once again emerge from the shadowy depths of the internet to build an exploit. This time, we'll be looking at how to defeat a non-executable stack by using the ret2libc technique — a lean, mean, and brilliant way of exploiting a stack overflow vul ...more
A man-in-the-middle attack, or MitM attack, is when a hacker gets on a network and forces all nearby devices to connect to their machine directly. This lets them spy on traffic and even modify certain things. Bettercap is one tool that can be used for these types of MitM attac ...more
Android 11 is here. Prior to Google dropping the naming scheme, this would have been a dessert with an R name (maybe Rice Krispies Treat or Red Velvet Cake) — but nope, just plain ol' Android 11. And after months of betas and a global pandemic, it finally debuted a little over ...more
There are countless tutorials online that show how to use Netstat and Tasklist to find an intruder on your computer. But with a few PowerShell functions, it's possible for a hacker to evade detection from the almighty command line. Before we dive into the technical sections, ...more
Signal is one of the best end-to-end encrypted messengers on the market. It offers robust security, keeps minimal information about its users, and is free to use. Switching to it as your main messenger can be a bit daunting, so to help, we created a guide to walk you through t ...more
You've protected your Ubuntu system from physical attacks, annoyed network hackers, and sandboxed potentially malicious applications. Great! Now, the next logical steps to locking down your OS include thoroughly auditing Ubuntu for weak points, using antivirus software that re ...more
Apple's new iOS 16 software update is finally here, and there are over 350 new features and changes for you to enjoy on your iPhone. There are major lock screen and home screen improvements, a pleasant surprise for the Contacts app, and tons of new upgrades to Safari, Mail, Me ...more
The new iOS 14 for iPhone arrived Wednesday, Sept. 15, 2020, alongside iPadOS 14, and there are a lot of features to uncover. Improved widgets. Better home screen customization. Exciting Messages improvements. New abilities in Camera and Photos. There's so much here that it'll ...more