From laptops to tablets, technology is taking over classrooms. Elementary schools offer kids tablets, and college students are bringing laptops into lecture halls, leaving their notebooks behind. Today, many students prefer putting their fingers to a keyboard rather than pen t ...more
The future: that time that lies ahead, unknown and overwhelming. Whether you're an obsessive planner or someone who can't think more than two days ahead, considering the future can be frightening with all of the "what ifs." Don't let the future keep you awake at night—in fact, ...more
The realm of science fiction isn't all lasers and cute green toddlers, sometimes alternate science history is sci-fi, too, as exampled by the Apple TV Plus series For All Mankind. Now, in a bid to promote the second season of the space-based series, Apple has launched a new a ...more
A 6,000-year-old forest inhabitant awakens to find life in the forest around it in crisis. Plants, trees, animals, and birds are moving north to escape increasingly heated air, even as mass extinctions take place around the world. The inhabitant stirs and remembers it has live ...more
When Kaci Hickox, a Doctors Without Borders nurse, returned to New Jersey from working with Ebola patients in West Africa in 2014, she was surprised by her reception. Instead of a quiet return to her home in Maine after four weeks on the front line of Ebola treatment, she was ...more
Now that we've had a few days to recover from the VR geek versus augmented reality nerd battle between Oculus founder Palmer Luckey and Magic Leap founder Rony Abovitz, we can get back to taking a closer look at the Magic Leap One. This time, we take a very brief dip into the ...more
Dopamine is a neurotransmitter that motivates us to engage in rewarding activities such as eating and sex. Animals without dopamine stop eating and starve to death. Certain drugs are able to activate dopamine receptors, and, as revealed by brain scans, meth heads, cocaine add ...more
Dr. Roy Cruzen, an exotic veterinarian, examines Skyler, the rabbit, for Pasteurella. Do this if you are a veterinarian.
This was a busy week in the tech space. After everyone got over the major announcements of Apple's latest, we examined the metaverse through the lens of Hollywood, and then took a closer look at Facebook's first smartglasses. We also took a trip back through history using Sna ...more
Worried your canine might bite somebody? Afraid to take them on walks anymore because of what could happen if a child walks past you? Afraid of a lawsuit? These are the worries associated with overly aggressive dogs. But with proper training, an aggressive dog can be transform ...more
Two viral liver diseases could help us find the path toward the cause of Parkinson's disease. Researchers from the University of Oxford and UCL Institute of Neurology in London have reported an association between hepatitis B and C infections and an increased risk of Parkinso ...more
Some of the leading big tech companies are still working in the lab on actual products, but at least some of their leadership did have some thoughts to share on the future direction of the technology this week. Meanwhile, we had the opportunity to check out two newish AR offe ...more
Humans clearly demonstrate altruistic tendencies towards other members of groups with which they identify. One bit of evidence that this is innate comes from studies with oxytocin. Those who inhale the hormone are significantly more likely to sacrifice for the benefit of memb ...more
Have you ever marveled at those knitting doyennes at Michael's who can just run up to the yarn aisle and speedily pick up some yarn because they know exactly what type of of yarn they need for their project without reading the yarn label? Most of us struggle with different yar ...more
Remember Dan White's "Twinkie defense" in 1979? Well it turns out that the the ability to convert food into glucose is correlated with the ability to control oneself. According to one study, 90% of those in juvie have below-average glucose levels. Even more incredible, in Fi ...more
If you've ever wondered how software pirates can take software and crack it time and time again, even with security in place, this small series is for you. Even with today's most advanced methods of defeating piracy in place, it is still relatively easy to crack almost any pro ...more
Welcome back, my rookie hackers! Now that nearly everyone and everyplace has a computer, you can use those remote computers for some good old "cloak and dagger" spying. No longer is spying something that only the CIA, NSA, KGB, and other intelligence agencies can do—you can l ...more
Before attacking any website, a hacker or penetration tester will first compile a list of target surfaces. After they've used some good recon and found the right places to point their scope at, they'll use a web server scanning tool such as Nikto for hunting down vulnerabiliti ...more
The gag reflex: it can interfere while in the dentist's chair, upon seeing another person throw up, or even just getting a whiff of a disgusting, stomach-twisting scent. Every time this reflex kicks in, it stops us immediately, inducing a choking, gagging, coughing fit. To ge ...more
Welcome back, my hacker trainees! A number of you have written me regarding which operating system is best for hacking. I'll start by saying that nearly every professional and expert hacker uses Linux or Unix. Although some hacks can be done with Windows and Mac OS, nearly al ...more
Welcome back, my hacker trainees! A score of my readers have been begging for tutorials on how to hack Wi-Fi, so with this article, I'm initiating a new series dedicated to Wi-Fi hacks. This will probably be around 6-9 articles, starting with the basics of the technologies. I ...more
Welcome back, my fledgling hackers! In one of my recent articles, I showed you how to install BackTrack as a dual boot system on a Windows computer. In this tutorial, I will walk you through BackTrack, giving you a tour of the most salient features for the hacker-to-be. NOTE ...more
In this article, I will be showing you how to make a crude form of aspirin from the bark of a willow tree. It is a great remedy for headaches, hangovers, and other minor pain. The use of the willow tree as a mild pain reliever goes back to the Native Americans, who used it in ...more
We see Steampunk props all the time and wonder where the maker found all their pieces. In fact, for some people it's almost like a game to examine each prop and see if they can name all of the original parts. However, for a newcomer (or a novice at prop-making), it may be rea ...more
There are many ways to attack a Wi-Fi network. The type of encryption, manufacturer settings, and the number of clients connected all dictate how easy a target is to attack and what method would work best. Wifite2 is a powerful tool that automates Wi-Fi hacking, allowing you t ...more
So you want to know what that person who is always on their phone is up to? If you're on the same Wi-Fi network, it's as simple as opening Wireshark and configuring a few settings. We'll use the tool to decrypt WPA2 network traffic so we can spy on which applications a phone i ...more
Testicular cancer is a young man's disease, and yet this is the age group that has the greatest sense of invincibility from the illness. Dr Harper demonstrates the technique you can use to self-examine your balls, and as it's best carried out in the shower, it's a great excuse ...more
Televisions used to be great for just one thing—watching TV. But a more connected world brought with it Smart TVs, devices that can access the web, stream Netflix, and even mirror your smartphone's display. And with this level of connectivity, OEMs like Samsung saw it fit to p ...more
Anonymity is something that doesn't exist today. Everything you do in the world is tracked, from the purchases you make to surfing the internet—even taking pictures on your iPhone. Everything you have ever said and done on the internet is still there—somewhere. This is called ...more
Minecart rides primarily serve two different functions—transportation or entertainment. We rarely see minecart-based transportation systems in Minecraft these days because most servers support warps or allow users to set multiple homes that they can simply teleport to. That le ...more
Welcome back, rookie hackers! We recently began an exploration of ways to hack using the Bluetooth protocol. As you know, Bluetooth is a protocol that connects near field devices such as headsets, speakers, and keyboards. Its minimum range is a 10-meter radius (~33 feet) and ...more
Welcome back, my hacker noviates! In a recent post, I introduced you to Shodan, the world's most dangerous search engine. Shodan crawls the globe from IP to IP address, attempting to pull the banners of each web-enabled device and server it finds. These banners are what the ...more
After finding and monitoring nearby wireless access points and devices connected to them, hackers can use this information to bypass some types of security, like the kind used for Wi-Fi hotspots in coffee shops, hotels, and in flights high above the ground. By swapping their M ...more
Welcome back, my budding hackers! With this article, I am initiating a new series that so many of you have been asking for: Hacking Web Applications. In previous tutorials, we have touched on some of the techniques and tools for web app hacking. We looked at web app vulnerab ...more
1 in 9 women will get breast cancer at some point in their lives, and at least a third of women will not self-check their breasts. Early diagnosis is essential in treating breast cancer, and that’s where monthly self-checks come in. If you’re not sure where to start – don’t wo ...more
Only so much data can be passed through the network and to your computer's networking interfaces. This is limited by the amount of bandwidth you have. The more bandwidth you have, the faster your network connections will be. Not only this, but your transfers will be more paral ...more
If you read my article on the OSI model, you got a good overview on communications from that model's perspective, but how does that relate to TCP/IP? We're going to take it a step further, getting into the idea behind the two address concept. How does an IP address and a MAC a ...more
Welcome back, my greenhorn hackers! Lately, much of the discussion here on Null Byte has revolved around evading detection and not getting caught hacking. Several of you have written me asking for a series on evading detection and forensics, and while I began a series 5 month ...more
When your computer first connects to a nework, it sends out a request on the network to lease an IP from the router. The router then leases your computer an unused IP address, which is used as a unique routing address for sending traffic that is meant for you, to you. As every ...more
In my first tutorial on Linux basics, I discussed the importance of hackers using Linux and the structure of the directory system. We also looked briefly at the cd command. In this second Linux guide, I'll spend a bit more time with changing directories, listing directories, c ...more
NOTICE: Ciuffy will be answering questions related to my articles on my behalf as I am very busy. Hope You Have Fun !!! Hello Guys, Welcome to my tutorial and in this tutorial, We are basically going to create a python script that serves as a proxy server ( Without External ...more
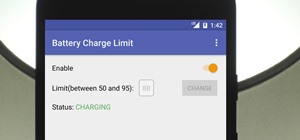
It's the icing on top of your cake (or whipped cream on top of your Android Pie) of despair. You may have not had the easiest time rooting your device, but you feel like you overcame all of the obstacles. Only now to discover that those very apps and mods you were rooting for ...more
Welcome back, my tenderfoot hackers! As most of you know, I am strong advocate for using Linux as a hacking platform. In fact, I would say that without knowing Linux, you will never become a professional hacker/pentester. On the other hand, there are many here who come to Nu ...more
Welcome back, my tenderfoot hackers! Those of you who have been reading my posts here for awhile know how much I emphasize good reconnaissance. Novice hackers often jump into a hack/exploit without doing proper recon and either fail or get caught. Experienced and expert hacke ...more
Samsung kicked off their Android Oreo rollout earlier this week. The update already improved the lock screen significantly with new wallpaper color-matching for the clock. With the newest update, we also get the ability to tweak the transparency of lock screen notifications. ...more
The video featured in this article demonstrates the function and design of a powerful form of air cannon that operates using a purpose made valve that opens very rapidly. This allows for a massive amount of pressurized air to be released at once to throw a projectile many hund ...more
Whether we like it or not, our personal information and smartphones are tied together at the hip. The former needs the latter to deliver a personalized experience that matches our individual needs. This personal data, however, makes your phone a prime target for thieves of all ...more
When learning Wi-Fi hacking, picking a compatible Wi-Fi network adapter is the first step to learning to crack Wi-Fi passwords. Many compatible adapters have swappable antennas, and there are several different kinds of specialized antennas you can add to a network adapter to ...more
Surveying a target's Wi-Fi infrastructure is the first step to understanding the wireless attack surface you have to work with. Wardriving has been around since the '90s and combines GPS data and Wi-Fi signal data to create accurate, in-depth maps of any nearby Wi-Fi networks ...more
What if I told you that you could read minds? You'd most likely think I was crazy, and you'd be right. But what I really meant is that you could make people think that you could read minds, something that's not the least bit crazy. Performing mind reading — and it is a perfor ...more
Restrictions are inconvenient, and for this reason I've sought out softmods that loosen the constraints for many of the features on my smartphone. Things like adding favorite apps to the Pen Window drawer or choosing any app for Multi Window mode are now must-haves on my Samsu ...more
With the release of the Mirai source code, botnets are back in a big way. In the early days of botnets, zombies (infected hosts) would report to IRC (Internet Relay Chat) channels for CNC (command and control) instructions. Modern botnets have evolved, but they continue to use ...more
Five Phases of Hacking:- The five phases of Hacking are as follow: Reconnaissance Scanning Gaining Access Maintaining Access Covering Tracks The Five Phases of Hacking Reconnaissance:- This is the primary phase where the Hacker tries to collect as much information as possib ...more
When it comes to attacking devices on a network, you can't hit what you can't see. Nmap gives you the ability to explore any devices connected to a network, finding information like the operating system a device is running and which applications are listening on open ports. Th ...more
Smartphones are crazy awesome. You can do your banking, track your children, find directions, and even pretend to have a mustache. The only thing that these personal supercomputers are missing is physical interaction with the environment. I wanted to be able to call my house ...more
Welcome back, my nascent hackers! In the conclusion of the Mr. Robot television series, Elliot and fsociety successfully completed their mission of encrypting all of Evil Corp's data with AES-128 encryption and destroying the key. Now that all of the data on Evil Corp's serv ...more
This is second post in my series of posts for finding hacked accounts online. Please do read the part 1 of the post at http://null-byte.wonderhowto.com/how-to/find-hacked-accounts-online-part-1-0164611/ In this post we will explore more about finding hacked accounts online, w ...more
After a hacker has configured Metasploit on a remote private server, created a resource script for automation, and created a simple payload, he or she can begin the process of remotely controlling someone's Windows 10 computer with just a few moments of physical access — even ...more
Welcome back, my hacker novitiates! In previous guides, we have used one of the most powerful hacking platforms on the planet, Metasploit, to perform numerous hacks. They ranged from exploiting Windows XP and Windows 7/8 vulnerabilities, to installing a keylogger and turning ...more
While the USB Rubber Ducky is well known by hackers as a tool for quick in-person keystroke injection attacks, one of the original uses for it was automation. In this guide, I'll be going the latter, explaining how we can use it to automate Wi-Fi handshake harvesting on the Ra ...more