In order to secure a PDF with a password when opened in Adobe Acrobat 9 Pro, press the secure button and go into password security settings. Here you can change on what versions of this software the file will run on, the next option asks which portion of the document is to be ...more
In a previous guide, I demonstrated how to extract images from a security camera over Wi-Fi using Wireshark, provided you know the password. If you don't know the password, you can always get physical with the Hak5 Plunder Bug. Using this small LAN tap, we can intercept traffi ...more
NOTICE: Ciuffy will be answering questions related to my articles on my behalf as I am very busy. Hope You Have Fun !!! As much as I love other SSH bruteforcing tools like Ncrack, Metasploit, THC-Hydra, ... ( Just to mention a few ). I prefer using my own script. The tools ab ...more
Pyrit is one of the most powerful WPA/WPA2 cracking tools in a hacker's arsenal, with the ability to benchmark a computer's CPU speeds, analyze capture files for crackable handshakes, and even tap into GPU password-cracking power. To demonstrate how quickly it can hack a WPA/W ...more
It's common for IoT devices like Wi-Fi security cameras to host a website for controlling or configuring the camera that uses HTTP instead of the more secure HTTPS. This means anyone with the network password can see traffic to and from the camera, allowing a hacker to interce ...more
In the second part of this tutorial, we are going to crack the hashes that we've captured previously. I'm going to explain how to do it with the powerful John the Ripper. It comes with Kali by default, so no need to install! Using John the Ripper If you don't know nothing ab ...more
Hello Elite Hackers! Welcome to my 3rd Post, which explains how to hack any account like G-mail, Facebook, etc. You can also use this technique to hack/spoof messengers like Facebook or WhatsApp etc. Step 1: Fire-Up Kali: I hope you know how to hack android and gain access t ...more
Copy and paste keyboard shortcuts are beautiful gifts from the gods, and any website that blocks such an offering can burn in hell. But really, Cmd+C and Cmd+V (Ctrl+C and Ctrl+V for Windows folks) are second nature to most of us, so it's very frustrating when sites like PayPa ...more
Hello guys I am ROMEO 64 (sounds weird I guess but who cares. :D).. Alright....Ever wondered what happens when you login to your Facebook account? WARNING - geeky stuff ahead! Quit now if sleepy :D You cannot imagine how much of hidden stuff happens when you press your login ...more
Hello! This is my first post on this awesome website! I know that Windows exploits are less common than the more advanced hacks, but I found something I deem pretty cool and figured why not share it with you all. Alright, enough about me, lets begin. Warning: This resets your ...more
How's it goin'? In this tutorial, we will learn about the security issues of the popen and system functions. I've seen a few people attempting to run command line utilities or whatever it is they require with calls to these two functions but may not know the security implicati ...more
Apple's dedication to iPhone security is one of the company's biggest selling points. It's no surprise then that iOS 12 offers users a simple yet powerful way to make, save, and auto-fill strong passwords to your iCloud Keychain when creating accounts in both Safari and in app ...more
The Pixel 4 and 4 XL are the first Android phones released in the US to support secure facial recognition. You no longer have to hate on your Apple's friends because you now have "Face ID" as well. So I assume you want to set it up right away — here's how. The new facial reco ...more
If you didn't get the memo, passwords aren't enough protection for your online accounts. Even a long and complex password offers only one line of defense which can falter. Two-factor authentication adds an additional layer, bolsters your defense, and decreases the risk of your ...more
Hello NullByte! This will be my first How To series. In this tutorial you'll learn what SQL is, what SQL injection is and how it benefits you as a hacker. I strongly recommend learning at least the basics of PHP before attempting to learn/use SQL Injection. list of reference ...more
Hi there again, aspiring hackers (and veterans as well)! I'm going to explain how to perform a dictionary attack on a WPA/WPA2 protected network with Wifite. Please note that this doesn't work with WPA Enterprise For that end, you'd have to use an Evil Twin to get the "Enterpr ...more
Welcome back, my neophyte hackers! I have already done a few tutorials on password cracking, including ones for Linux and Windows, WEP and WPA2, and even online passwords using THC Hydra. Now, I thought it might be worthwhile to begin a series on password cracking in general. ...more
Remote Desktop gives you access to your Windows 8 PC or device from wherever you are to run your applications and access your files remotely. Left an important document on your work computer? Want to run a legacy x86 desktop app from your Surface? You can use Remote Desktop ...more
So you want to know what that person who is always on their phone is up to? If you're on the same Wi-Fi network, it's as simple as opening Wireshark and configuring a few settings. We'll use the tool to decrypt WPA2 network traffic so we can spy on which applications a phone i ...more
ARP spoofing is an attack against an Ethernet or Wi-Fi network to get between the router and the target user. In an ARP-spoofing attack, messages meant for the target are sent to the attacker instead, allowing the attacker to spy on, deny service to, or man-in-the-middle a tar ...more
While Wi-Fi networks can be set up by smart IT people, that doesn't mean the users of the system are similarly tech-savvy. We'll demonstrate how an evil twin attack can steal Wi-Fi passwords by kicking a user off their trusted network while creating a nearly identical fake one ...more
Apple's iOS 13 for iPhone includes new features in Safari that make browsing the web a little bit better when compared to iOS 12. Some changes are small while others add functionality that just wasn't there before. Plus, there are more security enhancements. While Safari didn ...more
Computers all over the world rely on a program called "libssh" to use the SSH communications protocol, which allows trusted users to log in and administer computers remotely. Due to a flaw in libssh, fooling a computer into granting SSH access is as easy as telling it you alre ...more
Most websites and apps support two-factor authentication (2FA), which adds an extra layer of security to your accounts by requesting another form of identification beyond username and password. The second factor can be a recovery code, physical security key, or one-time passwo ...more
Have you ever been locked out of your iPhone? Maybe you forgot your passcode. Or perhaps someone with access changed the passcode as a prank. Your iPhone's display could have even been damaged and unresponsive. Whatever the reason, there's an easy way to get back access to you ...more
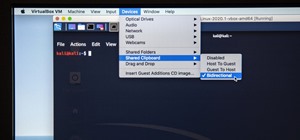
If you've spotted an unintended Ethernet connection and wondered what you could do with all of the information coursing through those wires, there's an easy way to hack into it and find out. Let's say there's a router that we need to know the password for, and we have physica ...more
You've probably connected your Android device to dozens of Wi-Fi networks since you've had it, and your phone or tablet remembers each of them. Whether it's a hotspot at home, school, work, the gym, a coffee shop, a relative's apartment — or even from a friend's phone — each t ...more
Airgeddon is a multi-Bash network auditor capable of Wi-Fi jamming. This capability lets you target and disconnect devices from a wireless network, all without joining it. It runs on Kali, and we'll cover installing, configuring, and using its jamming functionalities on a smal ...more
If your current cellular provider costs too much, has poor reception in your area, or doesn't support features you'd like to use, switching to another carrier is the obvious move. But can you bring your current iPhone or Android phone? In most cases, your current smartphone w ...more
As a web developer, I often read articles about hackers (from the lowly to the knowledgeable) infiltrating websites via the dreaded 'SQL Injection' method and completely taking control, changing, gaining access, or destroying the owner's data. As a fellow web developer, I'm su ...more
Last weekend, some unlucky Gmail users inadvertently had their email accounts wiped out. Actually, it was 0.02 percent of all Gmail users—or roughly 40,000 of the 200 million who use the email service, due to an "unexpected bug" which affected copies of the data. Gmail does ma ...more
If you use Office 2008 for Mac and all its applications (Word, PowerPoint, Entourage, Excel), than you need to know about the predefined workflows available using the Script menu that uses Automator to help perform mind-numbing tasks. The Microsoft Office for Mac team shows yo ...more
Does your network begin to crawl right around the time your sinister-looking next-door neighbors get home from work? Do you harbor suspicions that one or more of them may be stealing your Wi-Fi? It's easy to find out. And equally easy to give freeloaders the boot. In the guide ...more
Did you know that you can use Gmail to make free phone calls to anywhere in North America? We're not talking computer to computer, but actual free phone calls to cell phones and home phones. All you need is a Gmail account, a microphone, and speakers plugged into your compute ...more
Over the years, I have enjoyed playing with Asterisk. I have found Asterisk to be extremely powerful and fun to play with. There are several books and many scattered how to articles out there, but most are outdated and the information required to build Asterisk from beginning ...more
Want to hack a LAN? Well, hacking local area networks is easier than you'd think. And by watching a few short videos, you can become a master hacker, something every techie wants to achieve. And what's the best way to hack a LAN? Ettercap, a password sniffing program. The pro ...more
Have a file or a number of files too sensitive to be stored on your desktop hard drive? Thwart would-be snoopers with an encrypted USB flash drive. This free video tutorial from the folks at CNET TV will show you everything you'll need to know to create your own password-prote ...more
If you're trying to learn how to use Wi-Fi on your iPad, take a look at this tutorial on connecting your iPad to a wireless network so that you can access the internet. You'll need to use the settings and know the name of the wireless connection you want to use. Make sure you ...more
The Motorola XOOM was just released last week to Android-hungry fans waiting the next best thing to Apple's iPad. But should it have been released, considering Verizon's switching to the 4G LTE network soon? From what I saw across Android forums, yes—because most could not wa ...more
If you want to password restrict some of your data, or just want to know who is doing what in Microsoft Access 2007, you will want to set up a login form for MS Access 2007. This is an easy procedure, and you can create one yourself with just a basic understanding of the struc ...more
Social Profile Change the privacy settings on your social profile (Facebook, MySpace, Friendster, Twitter, etc.) so that the following information can't be found by a random person who you didn't accept you as a friend: Birthdate E-mail address Hometown Pictures A hacker ca ...more
Want to make a phone call on an iPhone 4 running Apple's iOS 4.1, but don't know its passcode? Not a problem. In this clip, we learn a simple trick that will allow you to bypass the lock screen entirely and permit you to view the phone's contact list and place phone calls to a ...more
In this tutorial Mike Lively of Northern Kentucky University shows you how to get started with Wireshark. Wireshark is a network protocol analyzer for Unix and Windows. It is used for network troubleshooting, analysis, software and communications protocol development. PART 1: ...more
WonderHowTo is a great place to find advice and learn things that you want to know, but can't find anywhere else. On this website, there are tons of people who make articles and videos to show you how to do stuff. In this tutorial, you will learn how to make your own WonderHow ...more
There has been an update with the NES emulator, so you have to put the ROMs in the /var/mobile/Media/ROMs/NES folder, and not the /var/root/Media/ROMs/NES folder. Another Note: you must install BSD Subsystem and OpenSSH through Installer in your iPod before configuring your i ...more
Have you ever wanted to make your own Minecraft server on Windows? This tutorial will teach you how, without having to download Hamachi. The whole process is a lot simpler than you might think, and it will only take a few minutes! You will need: Firefox web browser Computer ...more
If you're an owner of a BlackBerry smartphone, chances are you're going to want to use BBM, which for all of you newbie BlackBerry owners, stands for BlackBerry Messenger. BBM is an instant messaging application developed solely for BlackBerry device owners. Video: Add contact ...more
Plastic Jungle.com offers an awesome service in which you can sell your unused gift cards for cash, other gift cards, and even Facebook credits! You can visit their website and create an account then trade in your gift cards for cash and browse other gift cards that you can b ...more
According to Amazon.com, Kindle was their best-selling item this year, which means many, if not all of you are playing with a brand new Kindle on Christmas Day. Of all of Amazon's Kindle models, the Kindle 3 (6") will be the most common eReader in everyone's hands, either the ...more
Nowadays, there's a mobile app for just about everything—but that doesn't mean it should be on your smartphone. Not diggin' what SPB Shell 3D did to your home screen? Accidentally purchased Angry Sperms instead of Angry Birds? Want to try out the upcoming Smuggle Truck without ...more
Join the Pilot program and learn how to fly! But you're not going to be flying airplanes in this Pilot program, you'll be trying your hands at Google's first laptop computer. It's called the Cr-48, a black notebook wh ich runs an extraordinary operating system— Google Chrome. ...more
WikiLeaks. In recent weeks, it's been the hottest topic on the web. It's been attacked on a multinational level by political influence peddling. First, U.S. Senator Joe Lieberman swayed Amazon's decision to stop hosting WikiLeaks. Then, Tableau Software removed graphs from th ...more
With FarmVille being one of the hottest Facebook games on the market, it's no wonder it's the primary target for scams and virus downloads. Anyone playing FarmVille is at risk, but the primary targets are those looking to improve their gameplay and build their farms and neighb ...more
What's the easiest way to keep track of your website passwords? Maybe in a password-protected document on your computer? Makes sense. But surprisingly, this is no easy task in Mac OS X. Snow Leopard does not have an easy one-click option for password protecting files and fold ...more
Anonymity is something that doesn't exist today. Everything you do in the world is tracked, from the purchases you make to surfing the internet—even taking pictures on your iPhone. Everything you have ever said and done on the internet is still there—somewhere. This is called ...more
No doubt you've seen some of the hack logs being released. One part that stands out over and over again is the heavy database usage. It used to be early on that virus and hackers would destroy data, usually just for lulz. However, with the explosive commercial growth of the In ...more
To decipher my password, you need to know my mother's maiden name, where I was born, and what I had for breakfast on August 12th, 1996 (trick question, I was in a food coma). This was a bit simpler... May God have mercy on his soul. Images by bash.org, icebox500
To create an elegant WordPress blog or website from scratch without being noticed that you're a complete beginner, you need that drive and pairs of eyes and ears. It may seem difficult at first but it can truly be fun and exciting. In order for you to have a long lasting blog ...more
Previously, we talked about how to secure Firefox. Today, we will talk about securing a Chromium based Browser. Why? Because Chrome recently beat Firefox in holding more customers. It is obvious that Google Chrome tracks our every move online, so what alternatives is out ther ...more
If you ever want to delete your Yahoo Account for any reason, the option to do so is not easily available on the site.In fact, many people do not even know that such a feature exists. However, this video shows the necessary steps required to do so. Of course, you need to know ...more